Vulnerability Management
Harden your attack surface. Imagine having the power to see every vulnerability and a clear understanding of how to remediate them.One complete tool for client protection and compliance
Dynamic threats call for a dynamic approach. Our vulnerability scanning & compliance management tool designed and priced specifically for small-to-medium-sized companies (SMBs). Best practices are built in, for your ease of use.
Security Platform Includes
Pricing from R50 per endpoint per month
Learn More
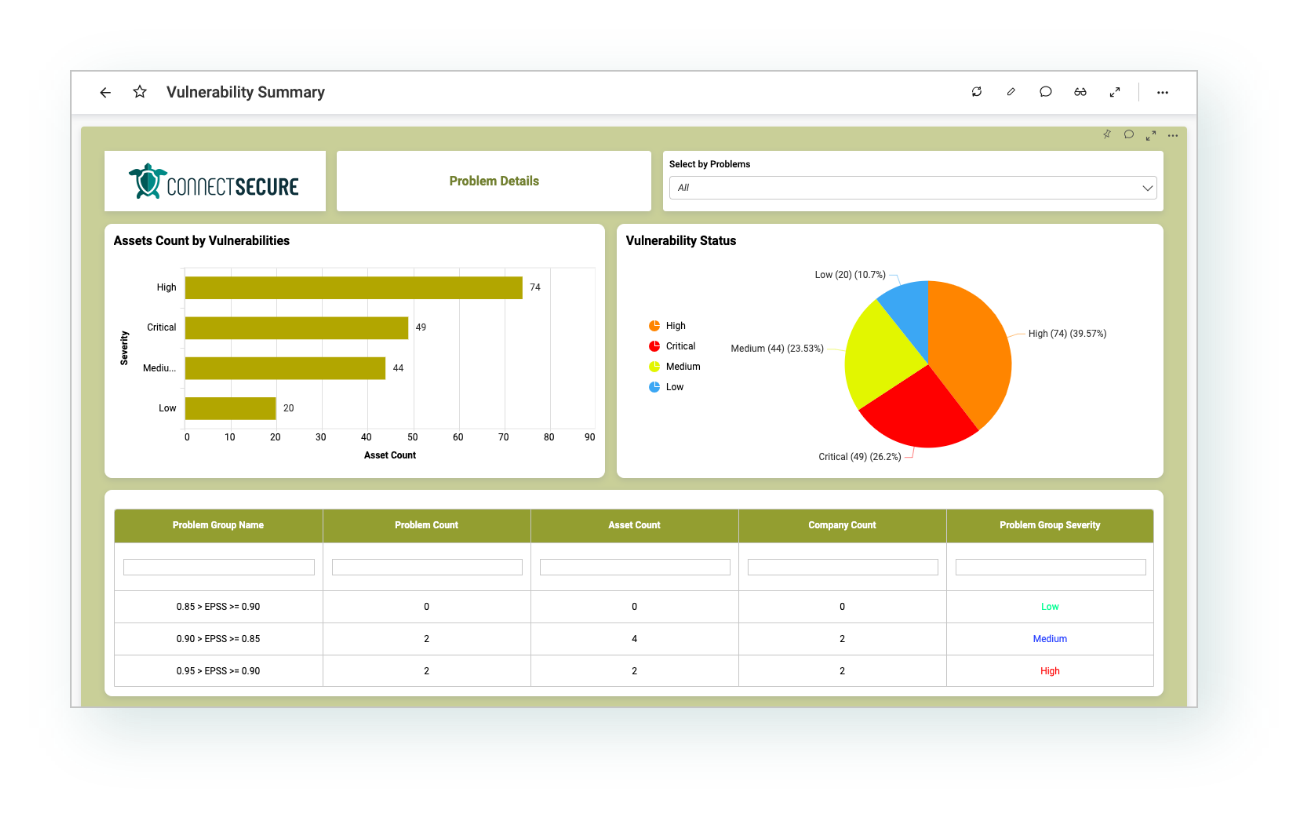
Prove your compliance visually
Easy-to-understand reporting is essential. With customizable client dashboards and automated reporting, ConnectSecure does the heavy lifting for you. Helping your company prepare for regulatory assessments has never been easier
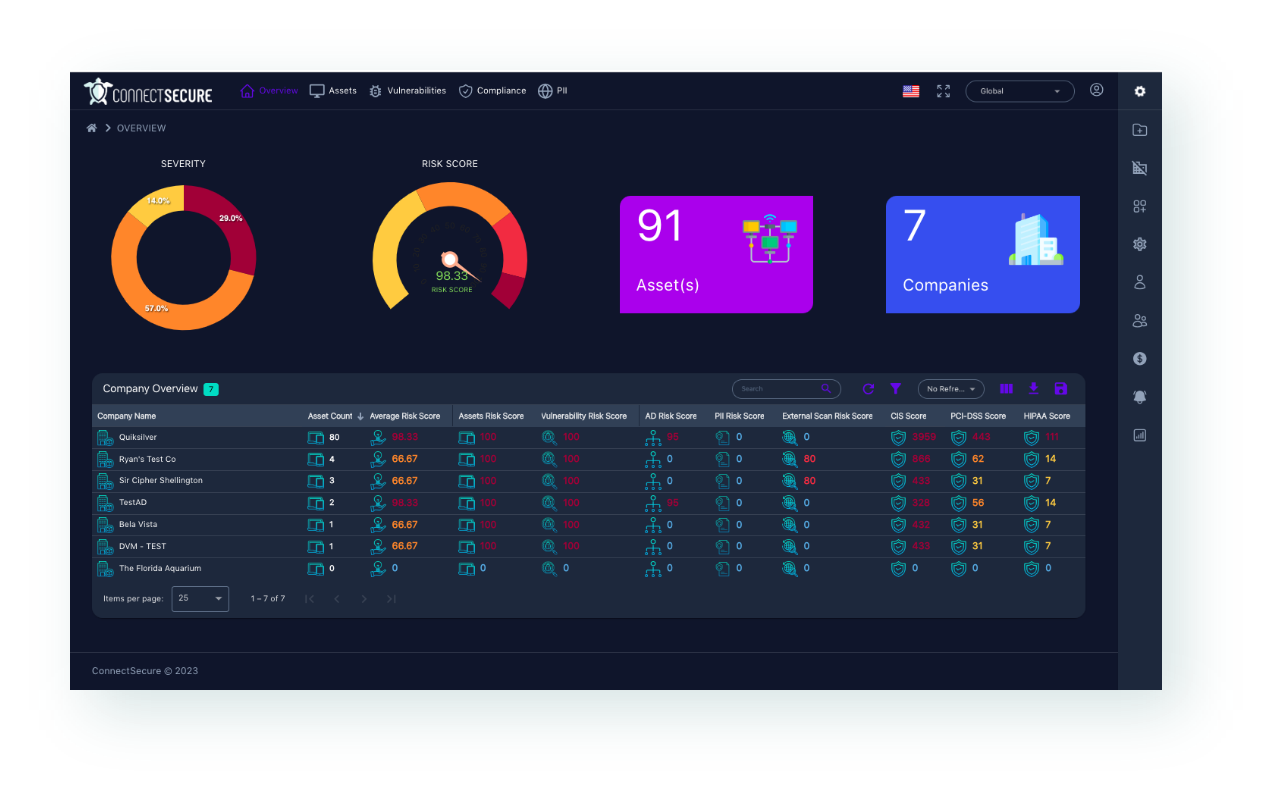
Flag security vulnerabilities and compliance gaps with confidence
Unlimited visibility brings optimal security. Whether ad-hoc or continuous and automated, the ConnectSecure vulnerability scans captures hardware, software, and networks, including internet-facing vulnerabilities, open ports, and exposed systems. Expert curated vulnerabilities reduce false positives.
Vulnerability Management
Proactively identify and address security weaknesses, reducing the risk of cyberattacks and potential data breaches.
Compliance Management
Ensure your clients are in compliance with PCI DSS, HIPAA, GDPR IV, NIST 800-53, NIST 800-171, CIS, CIS 8.0, ISO 27002, Cyber Essentials, and Essential Eight.
Vulnerability Assessment
Effectively uncover and address security vulnerabilities across your clients' networks.
PII Scanning
Safeguard personal information from cyber threats, ensuring the privacy and security of individuals and organizations.
Device, Network & Application Discovery
Use our network probe technology to discover all the IP-based assets on your network(s).
Attack Surface Scanning
Perform external Deep Attack Surface Scans to identify and address vulnerabilities in digital infrastructure and enhance overall security.
Active Threat Management
Provide enhanced protection with EPSS (Exploit Prediction Scoring System) against evolving cyber threats through proactive monitoring, detection, and response measures.
Cloud & Local Active Directory Auditing
Use on-site AD scanning to detect and prevent unauthorized access, enforce MFA, and provide Office 365 Risk Scoring.
Application Baseline Audit
Harness the power of comprehensive software system assessment to proactively reduce vulnerabilities, and monitor both the required and denied software services across all assets.
One Agent for Everything, on Anything
Simplify your security management by having one agent that works on all operating systems (MS, Linux, Raspberry PI, Mac).
Role-Based Ready Reporting
Drag and drop to provide well-designed, customized reports in MS Office formats for technical and management reviews. A white label option is also available.
Fully Managed
This is a fully managed service supported by an experienced team of engineers, who are available to assist your internal IT teams.