How to Spot Phishing Emails: Essential Tips for 2025
Phishing emails are everywhere and the stakes are getting higher every year. Just think, phishing scams caused over $4.1 billion in losses in 2020, hitting businesses hard and showing no sign of slowing down. Most assume fancy tech will keep them safe but psychology tricks and well-written emails slip through even the best filters. The biggest danger often comes from a simple click you barely remember making.
Table of Contents
- Understanding The Risks Of Phishing Emails
- Key Warning Signs In Suspicious Emails
- Steps To Safeguard Your Business Network
- Building A Cybersecurity Awareness Culture
Quick Summary
| Takeaway | Explanation |
|---|---|
| Identify key signs of phishing emails | Look for misspelled addresses, urgent language, and grammatical errors as indicators of phishing attempts. |
| Invest in employee training | Regularly educate staff on recognizing phishing tactics and reporting suspicious emails to mitigate risks. |
| Implement technological safeguards | Utilize multi-factor authentication, email filters, and regular updates to enhance your cybersecurity defenses against phishing. |
| Promote a cybersecurity culture | Foster continuous learning and engagement around security practices to raise awareness and compliance among employees. |
| Develop data protection strategies | Establish regular backups and incident response plans to prepare for potential phishing-related breaches or attacks. |
Understanding the Risks of Phishing Emails
Phishing emails represent a significant digital threat capable of compromising sensitive personal and organizational data. These deceptive communications exploit human psychology and technological vulnerabilities to manipulate recipients into performing harmful actions. Learn more about our cybersecurity protection strategies.
Financial and Data Breach Implications
The financial consequences of phishing attacks are staggering. According to the Federal Bureau of Investigation, phishing schemes resulted in over $4.1 billion in losses during 2020 alone. These attacks target businesses of all sizes, with mid-sized organizations particularly vulnerable due to potentially less robust security infrastructure.
Typical financial risks include unauthorized fund transfers, ransomware payments, and direct monetary theft. Beyond immediate financial losses, organizations face additional expenses related to incident response, system recovery, and potential legal liabilities.
Psychological Manipulation Techniques
Successful phishing emails leverage sophisticated psychological manipulation strategies. Cybercriminals craft messages that trigger emotional responses like fear, urgency, or curiosity. They meticulously design communications mimicking trusted sources such as banks, government agencies, or colleagues.
Common psychological tactics include:
- Urgent Language: Creating artificial time pressure that discourages careful scrutiny
- Authority Impersonation: Presenting messages as coming from high-ranking executives or official institutions
- False Rewards: Offering unexpected bonuses, prizes, or exclusive opportunities
These strategies exploit natural human tendencies to trust familiar communication channels and respond quickly to perceived threats or opportunities.
Long-Term Organizational Impact
Beyond immediate financial damage, phishing attacks can inflict severe long-term consequences. Data breaches might compromise customer information, erode organizational reputation, and trigger regulatory penalties. Companies might face significant legal challenges, loss of client trust, and potential business disruptions.
Small and medium-sized enterprises are particularly susceptible, with limited resources to implement comprehensive cybersecurity measures. Proactive education, robust technological defenses, and continuous employee training become critical in mitigating these evolving digital risks.
Understanding these multifaceted risks underscores the importance of developing a comprehensive, adaptive approach to email security. By recognizing potential threats and implementing strategic defensive measures, organizations can substantially reduce their vulnerability to these increasingly sophisticated cyber attacks.
Key Warning Signs in Suspicious Emails
Identifying phishing emails requires a keen eye and understanding of sophisticated digital deception techniques. Cybercriminals continuously evolve their strategies, making it crucial to recognize multiple warning signs that indicate a potentially malicious communication. Learn about our advanced email security techniques.
Sender Address Anomalies
The sender’s email address provides critical initial clues about potential phishing attempts. According to the Cybersecurity and Infrastructure Security Agency, suspicious email addresses often exhibit several distinctive characteristics:
- Misspelled Domain Names: Slight variations in legitimate company names that appear almost identical at first glance
- Random Character Combinations: Email addresses containing seemingly random strings of letters and numbers
- Impersonation Tactics: Addresses that closely mimic genuine organizational email formats but with subtle differences
Professional organizations maintain consistent email naming conventions. Any deviation should immediately trigger your suspicion. For instance, an email claiming to be from your bank but originating from a Gmail or Hotmail account represents a significant red flag.
Content and Language Indicators
Georgetown University’s Information Security Office highlights specific linguistic and structural elements that frequently signal potential phishing attempts. These warning signs include:
- Urgent or Threatening Language: Messages creating artificial time pressure or emotional manipulation
- Generic Greetings: Impersonal salutations like “Dear Customer” instead of specific names
- Grammatical Errors: Poorly constructed sentences, spelling mistakes, and awkward phrasing
- Inconsistent Formatting: Unusual font styles, sizes, or color variations within the same message
Cybercriminals often rush email compositions, resulting in linguistic inconsistencies that distinguish their communications from legitimate corporate correspondence.
Link and Attachment Verification
Malicious emails frequently incorporate dangerous hyperlinks and attachments designed to compromise system security. The University of Tennessee’s Office of Innovative Technologies recommends careful examination of these elements:
- Suspicious URL Structures: Links that do not match the purported sender’s domain
- Shortened or Obscured Links: URLs intentionally shortened to mask their true destination
- Unexpected Attachments: Files from unknown senders, particularly executable formats like .exe
- Mismatched Link Text: Hyperlink text that differs from the actual destination URL
Before clicking any link, hover your cursor over it to reveal the underlying web address. Legitimate organizations maintain transparent, predictable link structures aligned with their official domains.
Understanding these warning signs transforms email interactions from potential vulnerability to an opportunity for proactive cybersecurity. By developing a systematic approach to email scrutiny, individuals and organizations can significantly reduce their risk of falling victim to sophisticated phishing schemes.
Here is a summary table to help you quickly identify key warning signs of phishing emails, grouped by the type of indicator discussed above:
| Warning Sign Area | Common Indicators |
|---|---|
| Sender Address | Misspelled domains, random characters, impersonation of trusted organisations |
| Content & Language | Urgent tone, generic greetings, grammatical errors, inconsistent formatting |
| Links & Attachments | Suspicious URLs, shortened links, unexpected/executable files, mismatched link text |
Steps to Safeguard Your Business Network
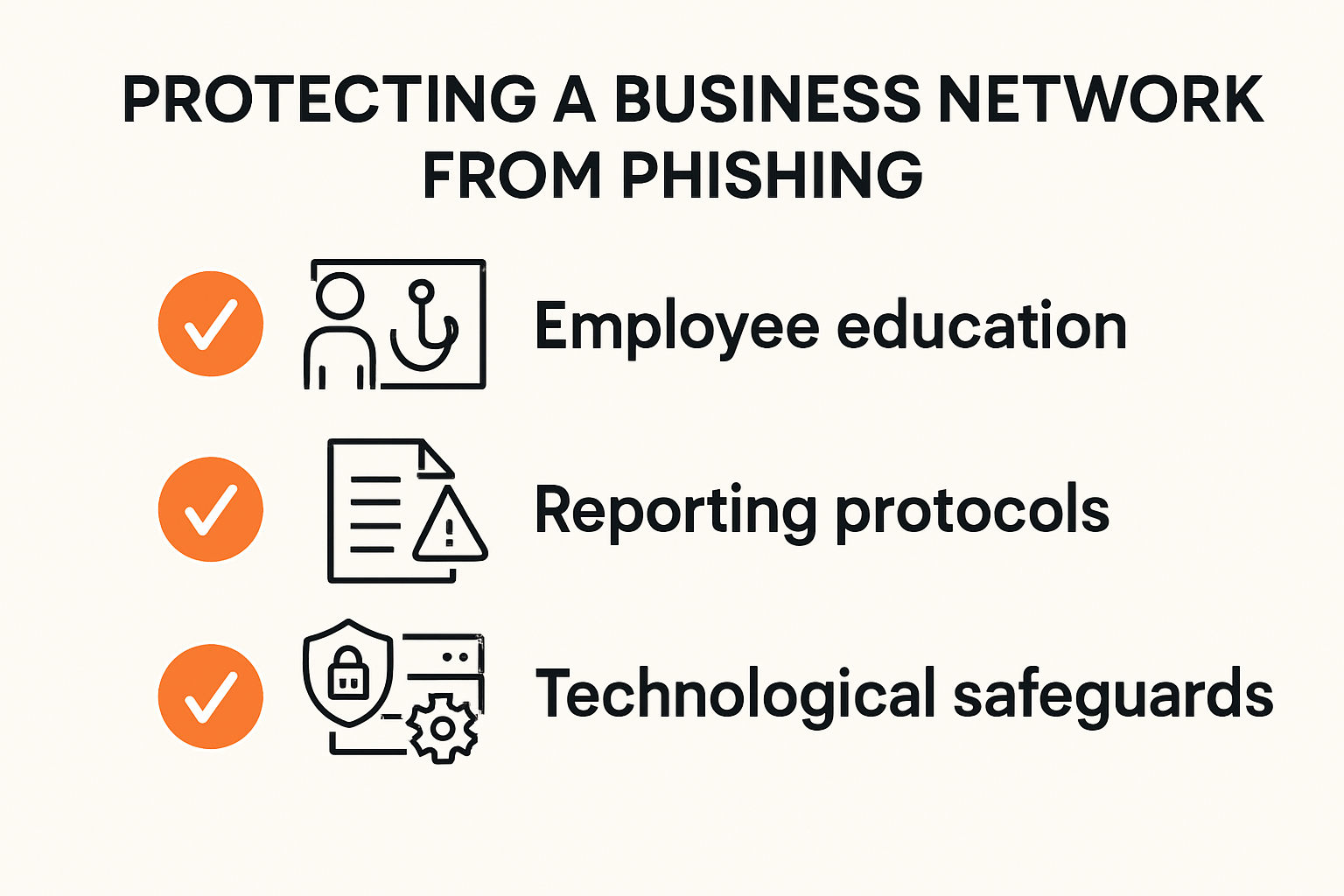
Protecting your business network from phishing threats requires a comprehensive, multilayered approach that combines technological solutions, employee education, and proactive security strategies. Explore our comprehensive cybersecurity solutions.
Employee Training and Awareness
Human error remains the most significant vulnerability in cybersecurity defenses. According to the Cybersecurity and Infrastructure Security Agency, regular and comprehensive employee training is critical in preventing successful phishing attacks. This training should encompass:
- Recognizing Suspicious Email Characteristics: Teaching staff to identify red flags in email communications
- Reporting Protocols: Establishing clear procedures for reporting potential phishing attempts
- Simulated Phishing Exercises: Conducting regular mock phishing tests to assess and improve employee readiness
Organizations should implement ongoing education programs that keep pace with evolving cyber threats. Interactive training sessions, real-world scenario demonstrations, and continuous learning modules can significantly reduce the risk of successful phishing attempts.
Advanced Technological Safeguards
The National Institute of Standards and Technology recommends implementing robust technological defenses to protect against sophisticated phishing attacks. Key technological strategies include:
- Multi-Factor Authentication (MFA): Implementing additional verification layers beyond passwords
- Email Filtering Systems: Deploying advanced software that detects and quarantines suspicious emails
- Network Segmentation: Limiting potential damage by isolating critical network components
- Regular Security Patches: Maintaining up-to-date software and system protections
Advanced endpoint protection solutions can provide real-time monitoring and automatic threat detection, creating an additional barrier against potential phishing infiltrations.
Data Protection and Recovery Strategies
The Federal Trade Commission emphasizes the importance of comprehensive data protection and recovery strategies. Critical considerations include:
- Regular Data Backups: Creating multiple, isolated backup copies of critical business data
- Offline Backup Storage: Maintaining backup systems disconnected from primary network infrastructure
- Incident Response Planning: Developing detailed protocols for addressing potential security breaches
- Continuous Monitoring: Implementing ongoing network surveillance and threat detection mechanisms
Businesses should develop a robust incident response plan that outlines specific steps for containing and mitigating potential phishing attacks. This includes immediate isolation of affected systems, comprehensive forensic analysis, and strategic recovery procedures.
Effective network protection is not a one-time effort but a continuous process of adaptation and improvement. By combining employee education, advanced technological solutions, and comprehensive data protection strategies, businesses can significantly reduce their vulnerability to increasingly sophisticated phishing threats.
Below is a comparison table summarising the three main pillars of business network protection against phishing, as discussed in this section:
| Pillar | Key Actions | Objective |
|---|---|---|
| Employee Training & Awareness | Regular training, reporting protocols, simulations | Increase staff vigilance, reduce human error |
| Technological Safeguards | MFA, email filtering, network segmentation, security patches | Block/philter threats at system level |
| Data Protection & Recovery | Backups, incident response plans, monitoring | Ensure data resilience and recovery |
Building a Cybersecurity Awareness Culture
Creating a robust cybersecurity awareness culture transcends traditional technical solutions. It requires a strategic, holistic approach that integrates proactive education, organizational commitment, and continuous learning. Discover our tailored cybersecurity training programs.
Establishing Organizational Security Foundations
A comprehensive cybersecurity culture begins with clear leadership commitment and structured policy development. According to NIST Special Publication 800-50, organizations must develop comprehensive security awareness and training programs that address both technical and human elements of cybersecurity.
Key foundational elements include:
- Clear Security Policies: Developing transparent, accessible guidelines that outline expected behaviors
- Leadership Accountability: Ensuring executive-level commitment to cybersecurity principles
- Regular Policy Updates: Continuously adapting security protocols to emerging technological threats
Successful implementation requires moving beyond bureaucratic documentation to creating meaningful, engaging security frameworks that employees understand and appreciate.
Interactive Training and Engagement Strategies
Effective cybersecurity awareness demands more than passive information delivery. The SANS Institute emphasizes the importance of interactive, engaging training methodologies that transform security education from a compliance requirement to an organizational value.
Innovative engagement approaches include:
- Gamification of Security Learning: Creating competitive, interactive training experiences
- Real-World Scenario Simulations: Developing practical exercises that mirror actual cyber threats
- Personalized Learning Paths: Tailoring training to individual roles and technological exposure
- Continuous Micro-Learning: Implementing short, frequent learning modules
By making cybersecurity education dynamic and relevant, organizations can foster genuine interest and proactive security behaviors among employees.
Measuring and Sustaining Cultural Transformation
Building a cybersecurity awareness culture requires ongoing measurement and adaptation. Gartner Research recommends implementing comprehensive metrics that track not just compliance, but genuine behavioral change.
Critical measurement strategies include:
- Behavioral Risk Assessments: Regularly evaluating employee security practices
- Incident Response Metrics: Tracking improvements in threat detection and response times
- Cultural Sentiment Surveys: Gauging employee attitudes toward cybersecurity
- Continuous Improvement Frameworks: Developing adaptive training programs
Successful cybersecurity cultures are not static but continuously evolving ecosystems that adapt to technological changes and emerging threat landscapes.
Transforming organizational cybersecurity requires more than technological solutions. It demands a holistic approach that empowers employees, integrates security into daily operations, and creates a shared commitment to protecting digital assets. By investing in comprehensive awareness strategies, businesses can develop resilient, security-conscious teams capable of effectively navigating complex digital challenges.

Frequently Asked Questions
What is phishing email?
Phishing emails are deceptive messages crafted by cybercriminals to trick recipients into providing sensitive information, such as passwords and financial details. They often appear to come from legitimate sources.
How can I identify a phishing email?
To spot a phishing email, look for key warning signs such as misspelled sender addresses, generic greetings, urgent language, grammatical errors, and suspicious links or attachments.
What should I do if I receive a suspicious email?
If you receive a suspicious email, do not click on any links or attachments. Instead, report the email to your IT department or email provider. Delete the email to prevent accidental engagement.
How can I protect my organization from phishing attacks?
To safeguard your organization, invest in employee training on recognizing phishing tactics, implement advanced technological safeguards like multi-factor authentication, and develop robust data protection and incident response strategies.
Take Control of Email Threats with Expert IT Solutions
Phishing emails are a growing danger for South African businesses, putting your finances, data, and reputation on the line. If the warning signs in this article made you wonder how secure your organisation truly is, you are not alone. Many engineering and financial firms face the same fears—what happens after a single misplaced click? Mistakes and overlooked risks can lead to serious disruptions, new compliance headaches, and major financial losses.
Do not let one phishing attempt compromise everything you have worked for. Discover how our cybersecurity and managed IT services can help you spot threats earlier, empower your team with awareness training, and protect your most valuable digital assets. Now is the best time to act because attacks are only getting smarter and business recovery costs are climbing. Visit Techtron IT Solutions to get started or to learn more about how we support South African mid-sized companies in building stronger, safer email and network environments for the future.