Network Security Best Practices for Modern Businesses
Network security risks are not just an IT issue anymore. A single ransomware attack can cost a business over R6.2 million on average and nearly half of those breaches start with a simple human mistake like clicking the wrong link. You would think the newest firewalls or encryption tech would keep you safe. Surprisingly, it turns out that your biggest defence is actually educating staff and creating a security-aware culture instead of just relying on gadgets or software.
Table of Contents
- Understanding Key Network Security Risks
- Implementing Core Network Security Best Practices
- Advanced Protection Strategies For Sensitive Data
- Training Staff And Building A Secure Culture
Quick Summary
| Takeaway | Explanation |
|---|---|
| Understand emerging network threats | Recognizing threats like ransomware and insider breaches is crucial for effective security. |
| Implement zero trust architecture | This framework assumes no inherent trust and requires continuous verification of access requests. |
| Prioritize advanced employee training | Comprehensive security programs help employees identify and respond to potential threats effectively. |
| Establish strong authentication methods | Multi-factor authentication and role-based access control enhance protection against unauthorized access. |
| Create a culture of security awareness | Engaging employees in security processes fosters commitment to protecting organizational assets. |
Understanding Key Network Security Risks
Network security risks represent complex challenges that can devastate businesses through data breaches, financial losses, and reputation damage. Understanding these risks is the first critical step in developing robust defensive strategies that protect an organisation’s digital infrastructure.
Emerging Threat Landscapes
Modern network security risks have evolved far beyond traditional firewall protections. According to Financial Times, cybercriminals are increasingly deploying sophisticated attack methodologies that exploit technological vulnerabilities and human psychological weaknesses.
The primary network security risks businesses currently face include:
- Ransomware Attacks: Malicious software encrypting critical business data and demanding financial payment
- Social Engineering Tactics: Manipulative strategies designed to trick employees into revealing sensitive information
- Insider Threats: Potential security breaches originating from within the organisation
To help you quickly scan the types of network security risks facing businesses today, the table below summarises the main threats discussed in this section, along with a brief description of each.
| Threat Type | Description |
|---|---|
| Ransomware Attacks | Malicious software encrypting business data for ransom |
| Social Engineering Tactics | Tactics tricking employees into revealing information |
| Insider Threats | Security breaches from within the organisation |
| Unpatched Software Systems | Outdated, vulnerable software in the network |
| Weak Authentication Mechanisms | Poor or outdated login and verification processes |
| Inadequate Network Segmentation | Lack of secure zones within network infrastructure |
| Poorly Configured Cloud Infrastructure | Cloud setup errors opening up security gaps |
Complex Technological Vulnerabilities
TechRadar research highlights that organisations must move beyond traditional compliance-driven security models. Modern network security requires a proactive “Secure by Design” approach that anticipates and mitigates potential risks before they manifest.
Key technological vulnerabilities include:
- Unpatched software systems
- Weak authentication mechanisms
- Inadequate network segmentation
- Poorly configured cloud infrastructure
Human Factor in Network Security
While technological solutions are critical, human behaviour remains the most unpredictable network security risk. Employees can inadvertently compromise network security through:
- Clicking on phishing emails
- Using weak passwords
- Connecting to unsecured networks
- Sharing sensitive information without proper verification
Addressing these human-centric risks requires comprehensive cybersecurity training, implementing zero-trust security models, and creating a culture of security awareness within the organisation.
By understanding these complex network security risks, businesses can develop nuanced strategies that protect their digital assets, maintain operational continuity, and safeguard their most valuable resource: information.
Implementing Core Network Security Best Practices
Implementing robust network security best practices requires a strategic and comprehensive approach that goes beyond basic technological interventions. Organisations must develop multi-layered strategies that address technological infrastructure, human factors, and ongoing risk management.
Foundational Security Architecture
According to the National Institute of Standards and Technology (NIST) Cybersecurity Framework, establishing a robust security architecture begins with comprehensive asset identification and risk assessment. This process involves mapping critical network resources, understanding potential vulnerabilities, and developing targeted mitigation strategies.
Key components of a strong security architecture include:
- Network Segmentation: Dividing network infrastructure into controlled, secure zones
- Access Control Frameworks: Implementing strict authentication and authorization protocols
- Continuous Monitoring Systems: Establishing real-time threat detection mechanisms
Advanced Authentication and Access Management
Modern network security demands sophisticated authentication approaches that move beyond traditional username and password models. Multi-factor authentication represents a critical defense mechanism against unauthorized access attempts.
Effective authentication strategies encompass:
- Biometric verification techniques
- Hardware security tokens
- Role-based access control systems
- Adaptive authentication mechanisms that assess risk in real-time
Proactive Threat Prevention and Response
Successful network security is not just about prevention but also about developing agile response capabilities. Organisations must create comprehensive incident response plans that enable rapid detection, containment, and recovery from potential security breaches.
Essential threat prevention and response elements include:
- Regular vulnerability scanning and penetration testing
- Automated threat intelligence gathering
- Comprehensive employee cybersecurity training programs
- Defined incident response workflows
- Regular backup and disaster recovery protocols
By integrating these network security best practices, organisations can create resilient digital environments that protect critical assets, maintain operational continuity, and adapt to evolving cyber threats. The key lies in developing a holistic, proactive approach that combines technological solutions with strategic human-centric interventions.
Advanced Protection Strategies for Sensitive Data
Protecting sensitive data requires sophisticated strategies that go beyond traditional security measures. Modern organisations must implement comprehensive approaches that anticipate and mitigate complex digital threats while maintaining operational efficiency.
Zero Trust Architecture Implementation
According to NIST Special Publication 800-207, Zero Trust Architecture represents a revolutionary approach to data protection. This strategy fundamentally challenges traditional network security models by assuming no inherent trust within or outside an organisation’s network perimeter.
Key principles of Zero Trust Architecture include:
- Continuous Verification: Authenticating every access request in real-time
- Least Privilege Access: Restricting user permissions to minimum required levels
- Micro-segmentation: Creating granular network zones to limit potential breach impacts
- Dynamic Risk Assessment: Continuously evaluating access requests based on contextual factors
The table below offers a side-by-side comparison of traditional network security approaches with Zero Trust Architecture, highlighting their key differences as discussed in the article.
| Feature | Traditional Security | Zero Trust Architecture |
|---|---|---|
| Assumption of Trust | Trust inside the perimeter | No inherent trust |
| Access Verification | Initial login only | Continuous verification |
| Access Levels | Often broad privileges | Least privilege access |
| Network Segmentation | Basic or limited | Micro-segmentation |
| Risk Assessment | Periodic | Ongoing, dynamic |
Advanced Data Encryption Techniques
NIST Special Publication 800-53 recommends sophisticated encryption strategies that protect sensitive information across multiple dimensions. Modern encryption goes beyond simple data scrambling to create comprehensive protection mechanisms.
Advanced encryption strategies encompass:
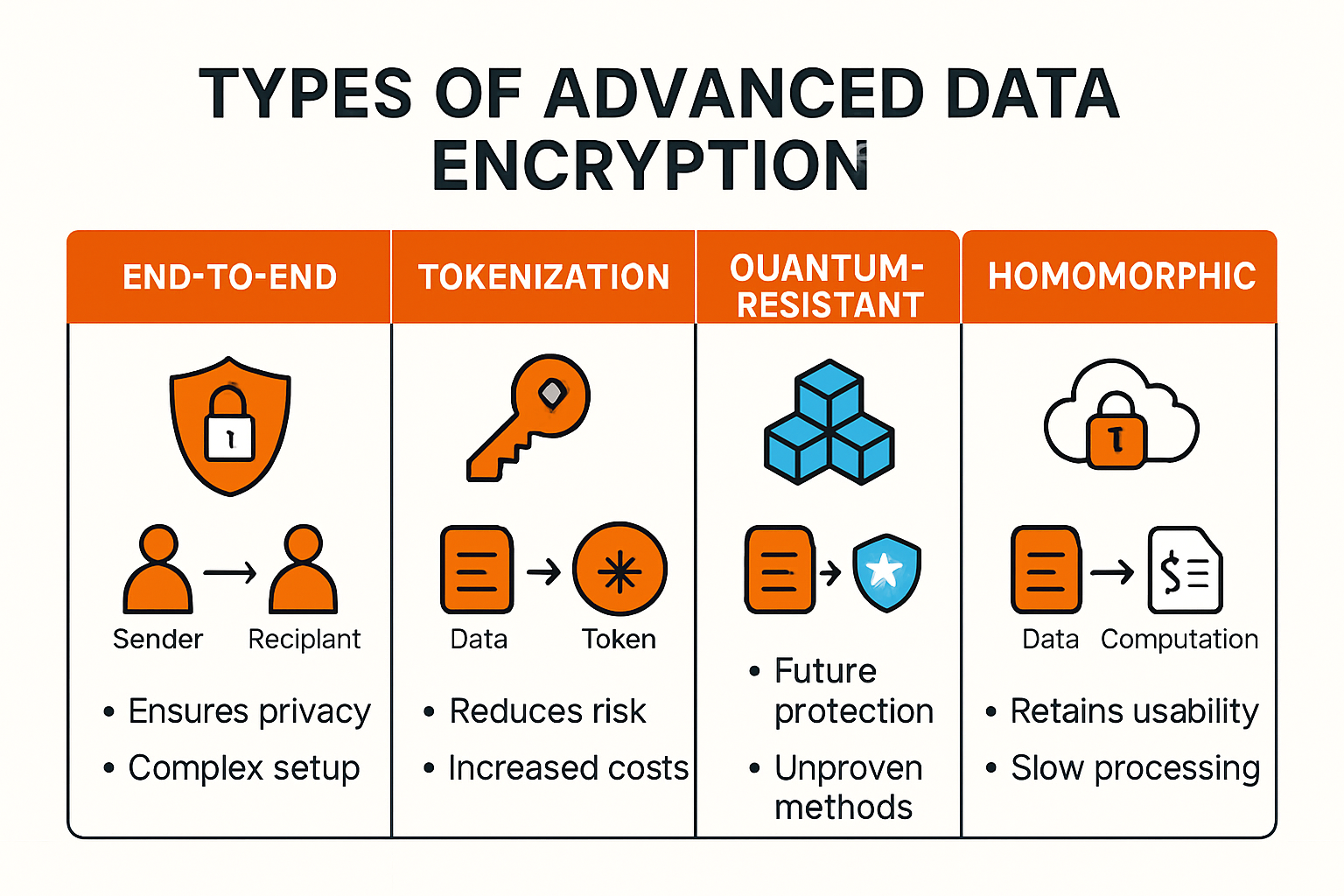
- End-to-end encryption for communication channels
- Tokenization of sensitive data elements
- Quantum-resistant encryption algorithms
- Homomorphic encryption enabling computational work on encrypted data
Intelligent Threat Detection and Response
Sensitive data protection requires proactive and intelligent monitoring systems that can detect, predict, and neutralize potential security threats before they cause significant damage. This approach combines advanced technological tools with strategic human oversight.
Comprehensive threat detection strategies include:
- Machine learning-powered anomaly detection
- Automated incident response workflows
- Real-time threat intelligence integration
- Predictive risk modeling
- Comprehensive logging and forensic capabilities
By implementing these advanced protection strategies, organisations can create robust defensive frameworks that safeguard sensitive data against increasingly sophisticated cyber threats. The key lies in adopting a dynamic, adaptive approach that combines technological innovation with strategic risk management.
Training Staff and Building a Secure Culture
Building a robust network security strategy extends far beyond technological solutions. The human element remains the most critical and often most vulnerable component of an organisation’s cybersecurity infrastructure. Developing a comprehensive security culture requires strategic, ongoing employee education and engagement.
Comprehensive Security Awareness Programs
According to SANS Institute research, effective security awareness programs are fundamental in transforming employee behaviour and reducing organisational risk. These programs must move beyond traditional compliance training to create genuine understanding and proactive security mindsets.
Key elements of effective security awareness training include:
- Interactive Learning Modules: Engaging, scenario-based training that simulates real-world security challenges
- Continuous Education: Regular updates addressing emerging cyber threats
- Practical Skill Development: Teaching employees concrete actions to identify and mitigate security risks
- Personalised Learning Paths: Tailoring training to different roles and technological expertise levels
Psychological Approaches to Security Behaviour
Transforming security from a perceived administrative burden to a shared organisational responsibility requires understanding human psychology. Successful security culture initiatives focus on motivation, empowerment, and creating positive reinforcement mechanisms.
Effective psychological strategies include:
- Gamification of security training
- Recognition programs for security-conscious behaviour
- Transparent communication about organisational security goals
- Creating a blame-free reporting environment for potential security incidents
- Developing emotional intelligence around cybersecurity risks
Practical Implementation and Measurement
Building a secure culture demands more than theoretical training. Organisations must implement structured approaches to measure, reinforce, and continuously improve security awareness and behaviour.
Practical implementation strategies encompass:
- Regular phishing simulation exercises
- Detailed performance tracking of security awareness metrics
- Incident response drills that test employee readiness
- Feedback mechanisms for improving training programs
- Leadership demonstration of security commitment
By treating security culture as a dynamic, evolving process, organisations can transform employees from potential security vulnerabilities into active defenders of digital assets. The goal is not simply compliance, but creating a shared commitment to protecting organisational information and technological infrastructure.
Successful security culture development recognises that technology provides the framework, but human understanding and commitment provide the true defensive capability. Continuous learning, empowerment, and strategic engagement remain the most powerful tools in building resilient organisational security.

Frequently Asked Questions
What are the key network security risks for modern businesses?
Understanding the key network security risks includes threats like ransomware attacks, social engineering tactics, insider threats, unpatched software systems, and weak authentication mechanisms. Recognizing these risks is vital for implementing effective security measures.
How can businesses implement a Zero Trust Architecture?
To implement Zero Trust Architecture, businesses should focus on continuous verification of access requests, applying the principle of least privilege access, and using micro-segmentation for their networks. This requires ongoing risk assessments to adapt to potential threats.
Why is employee training essential for network security?
Employee training is crucial for network security because human behaviour remains one of the most unpredictable risks. Comprehensive security awareness programmes help employees recognize and respond to potential threats, minimizing human errors that could lead to breaches.
What advanced authentication methods should businesses consider?
Businesses should consider implementing multi-factor authentication, biometric verification, role-based access control systems, and adaptive authentication mechanisms that assess risk in real-time. These methods enhance protection against unauthorized access.
Take Control of Your Network Security with Managed IT Expertise
If reading about insider threats, ransomware, and the limits of traditional security has you rethinking your current defences, you are not alone. The risks highlighted in this article show how just one simple error or an outdated system can cost your business not only money but also your reputation. Businesses like yours need a proven approach that combines advanced tools, zero trust models, ongoing staff training, and proactive threat detection, just as described in the best practices above.
At Techtron, we turn these best practices into everyday reality. Our managed IT and cybersecurity solutions are designed to protect your network and critical data, while reducing your technical burdens and compliance headaches. Discover the benefits of our tailor-made IT management for professional service firms and growing organisations by visiting our Cloud Solutions page. Ready to transform your network security from a weak link into your business’s greatest strength? Visit https://techtron.co.za today to connect with our team and take the next step towards real protection, expert support, and peace of mind.