Understanding Information Security Standards
Information security standards shape the backbone of every organisation’s digital safety plan. Businesses that ignore these standards risk losing up to 7% of their annual revenue to data breaches. Most people assume these frameworks are all about complicated tech and endless policies. Actually, they turn security from a costly headache into a powerful tool that protects growth and builds real trust.
Table of Contents
- Defining Information Security Standards: What They Are
- The Importance Of Information Security Standards In Business
- How Information Security Standards Function In Practice
- Key Concepts And Frameworks Of Information Security Standards
Quick Summary
| Takeaway | Explanation |
|---|---|
| Information security standards provide structured frameworks. | These frameworks help organisations systematically manage and protect their digital assets from risks and vulnerabilities. |
| Proactive risk management is essential for security. | Information security standards enable organisations to identify and mitigate cybersecurity threats before they escalate. |
| Maintaining compliance with regulations is crucial. | Adhering to information security standards ensures alignment with legal requirements, reducing potential penalties and legal risks. |
| Investing in security builds customer trust. | Demonstrating strong security practices helps organisations maintain confidence among customers and stakeholders, enhancing long-term relationships. |
| Holistic security integrates people, processes, and technology. | Effective information security encompasses technical controls, procedural guidelines, and organisational frameworks to create comprehensive protection strategies. |
Defining Information Security Standards: What They Are
Information security standards represent foundational guidelines and protocols designed to protect an organisation’s digital assets, data infrastructure, and sensitive information from potential risks and vulnerabilities. These comprehensive frameworks establish systematic approaches for managing, securing, and maintaining technological ecosystems across various operational domains.
The Core Purpose of Information Security Standards
At their essence, information security standards provide a structured methodology for organisations to identify, assess, and mitigate potential cybersecurity threats. South African Government guidelines emphasise that these standards are not merely technical recommendations but critical strategic frameworks that enable businesses to:
- Establish consistent security protocols
- Protect critical digital infrastructure
- Create standardised risk management approaches
- Ensure regulatory compliance
Understanding the Fundamental Components
Information security standards typically encompass multiple dimensions of technological protection. These include:
Technical Controls: Specific technological mechanisms like encryption protocols, firewall configurations, and access management systems that directly prevent unauthorized data access.
Procedural Guidelines: Documented processes and workflows that outline how employees should interact with digital systems, manage sensitive information, and respond to potential security incidents.
Organisational Frameworks: Broader strategic approaches that define roles, responsibilities, and governance structures related to information security management.
By integrating these components, information security standards create a holistic approach to protecting digital assets. They transform cybersecurity from a reactive practice into a proactive, systematic discipline that anticipates and neutralizes potential threats before they can cause significant damage to an organisation’s technological infrastructure.
Below is a table that summarises the core components of information security standards, helping you quickly compare their features and organisational roles.
| Component | Description | Organisational Role |
|---|---|---|
| Technical Controls | Technological mechanisms like encryption, firewalls, and access management | Directly protect digital assets and data |
| Procedural Guidelines | Documented processes and workflows for staff interactions and incident response | Guide employee actions and ensure consistent practice |
| Organisational Frameworks | Strategic approaches defining roles, responsibilities, and governance structures | Assigns accountability and oversees security strategy |
The Importance of Information Security Standards in Business
Business environments increasingly depend on digital technologies, making information security standards not just a technical requirement but a critical strategic necessity. These standards serve as comprehensive frameworks that protect organisations from evolving cybersecurity threats while ensuring operational resilience and maintaining stakeholder trust.
Financial and Reputational Risk Management
University of Johannesburg research highlights that information security standards play a pivotal role in mitigating substantial financial and reputational risks. Organisations that fail to implement robust security protocols can experience:
- Significant financial losses from data breaches
- Potential legal liabilities and regulatory penalties
- Erosion of customer and investor confidence
- Long-term damage to brand reputation
Strategic Business Continuity Protection
Information security standards function as proactive defence mechanisms that safeguard critical business infrastructure. By establishing systematic approaches to identifying, assessing, and neutralizing potential vulnerabilities, these standards ensure:
Operational Resilience: Continuous protection of core business systems and data repositories against potential cyber threats.
Regulatory Compliance: Alignment with national and international cybersecurity regulations, reducing potential legal and financial risks.
Competitive Advantage: Demonstrating strong security practices can differentiate businesses in markets where data protection is increasingly valued by customers and partners.
Moreover, these standards create a structured environment where technological risks are systematically managed, allowing businesses to focus on growth and innovation with confidence in their digital infrastructure’s integrity. By transforming security from a reactive cost centre to a strategic business enabler, information security standards become fundamental to modern organisational success.
How Information Security Standards Function in Practice
Information security standards transform theoretical cybersecurity concepts into actionable, practical strategies that organisations can implement to protect their digital ecosystems. These frameworks are not abstract theoretical models but dynamic, adaptive mechanisms designed to address real-world technological challenges and emerging threat landscapes.
Implementation and Governance Mechanisms
Nelson Mandela University research emphasises that effective information security standards require comprehensive implementation strategies that go beyond technical configurations. Successful deployment involves:
- Creating clear organisational policies
- Establishing robust governance structures
- Developing continuous training programs
- Implementing regular monitoring and assessment protocols
Risk Assessment and Compliance Frameworks
Practical application of information security standards revolves around systematic risk management approaches. These frameworks enable organisations to:
Identify Vulnerabilities: Conduct thorough assessments of existing technological infrastructure and potential security gaps.
Develop Mitigation Strategies: Create targeted interventions that address specific security risks unique to the organisation’s operational context.
Establish Monitoring Systems: Implement continuous surveillance mechanisms that detect and respond to potential security incidents in real-time.
The practical implementation of information security standards requires a holistic approach that integrates technological solutions, human expertise, and adaptive management strategies. By treating security as a dynamic, evolving discipline rather than a static checklist, organisations can create resilient digital environments that effectively protect against sophisticated and emerging cybersecurity threats.

Key Concepts and Frameworks of Information Security Standards
Information security standards represent comprehensive ecosystems of guidelines, principles, and methodological approaches designed to protect organisational digital assets through structured, systematic frameworks. These intricate frameworks combine technological, procedural, and human elements to create holistic security strategies that adapt to evolving technological landscapes.
Fundamental Security Architecture Components
Socio-Technical Information Security research highlights that effective information security standards integrate multiple interdependent architectural components. These components encompass:
- Technical infrastructure protection mechanisms
- Human behaviour and awareness protocols
- Organizational governance structures
- Risk management and mitigation strategies
Primary Conceptual Frameworks
Information security standards typically revolve around several core conceptual frameworks that guide implementation and management:
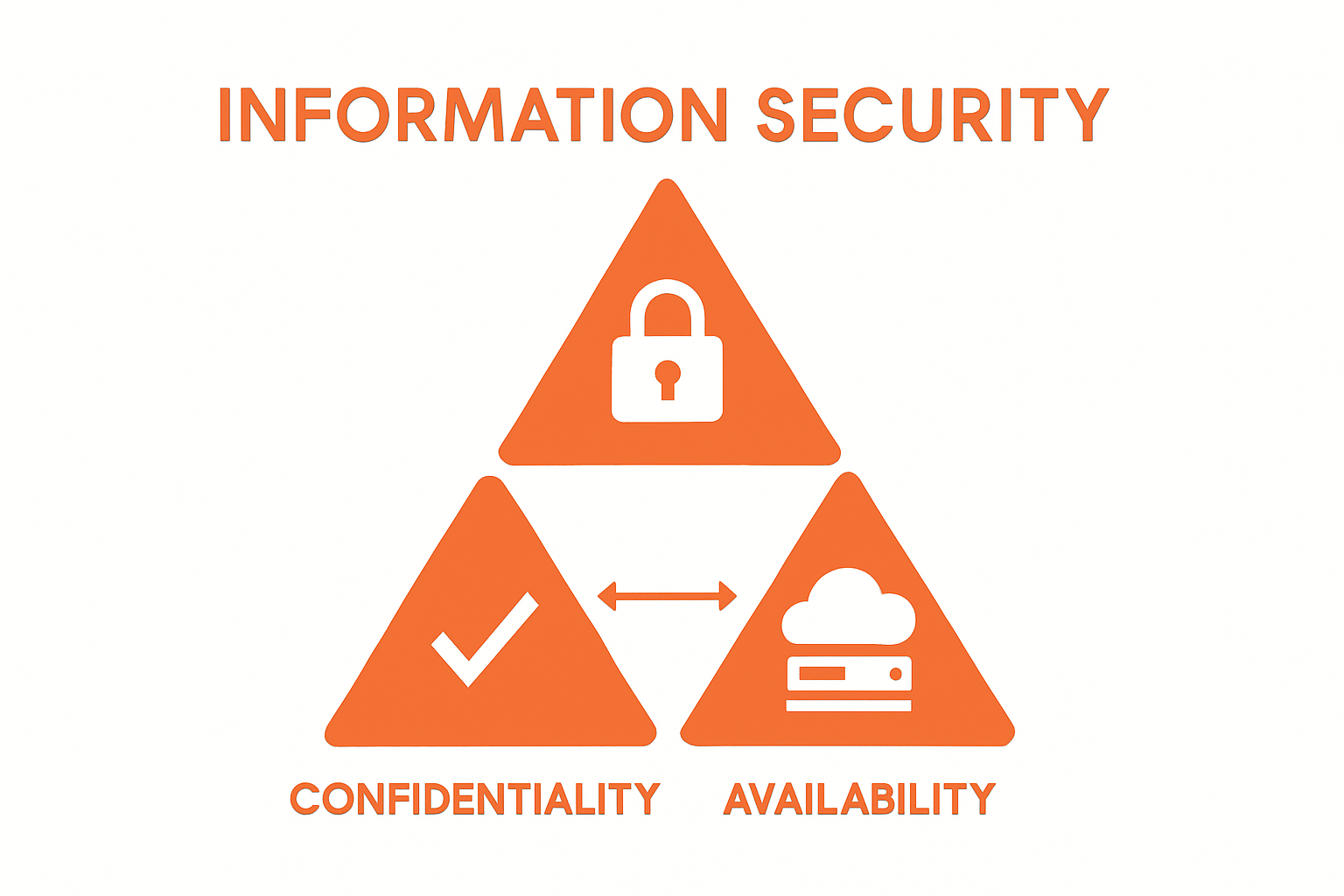
Confidentiality: Ensuring that sensitive information remains accessible only to authorized personnel through robust access control mechanisms.
Integrity: Maintaining the accuracy, consistency, and trustworthiness of data throughout its lifecycle, preventing unauthorized modifications.
Availability: Guaranteeing that information and critical systems remain accessible to authorized users when required, minimizing potential operational disruptions.
These conceptual frameworks serve as foundational principles that transform abstract security concepts into actionable strategies.
The table below compares the core conceptual frameworks underpinning information security standards, clarifying how each principle supports organisational protection and resilience.
| Concept | Focus Area | Purpose |
|---|---|---|
| Confidentiality | Restricting access to sensitive information | Ensure only authorised people can view or use critical data |
| Integrity | Ensuring data accuracy, consistency, and trustworthiness | Prevent unauthorised modification or corruption of information |
| Availability | Maintaining access to information and systems for authorised users | Ensure data and systems are accessible when needed |
 By understanding and implementing these core components, organisations can develop comprehensive information security approaches that proactively address potential vulnerabilities while maintaining operational efficiency and technological resilience.
By understanding and implementing these core components, organisations can develop comprehensive information security approaches that proactively address potential vulnerabilities while maintaining operational efficiency and technological resilience.
Transform Your Information Security Standards Into Tangible Protection
Understanding information security standards is only the first step. The real challenge is implementing these strategies effectively to shield your business from financial risk, compliance headaches and reputational harm. As detailed in this article, establishing consistent protocols, managing technical controls and ensuring your team follows procedural guidelines are critical steps—but they can be overwhelming for busy mid-sized companies and professional service firms.
Let Techtron step in as your trusted IT partner. Our managed IT services are designed to bridge the gap between theory and action:
- Dedicated cybersecurity and network protection
- Reliable data backup and disaster recovery solutions
- Expertise in regulatory compliance
- Proactive monitoring and rapid response
Your digital security deserves expert attention. Visit Techtron’s solutions today to discover how our team can help you implement robust information security standards that reduce risk and keep your business moving forward. Take action now to put proven frameworks and specialist support in place before threats impact your bottom line.
Frequently Asked Questions
What are information security standards?
Information security standards are guidelines and protocols designed to protect an organisation’s digital assets and sensitive information from risks and vulnerabilities. They provide a systematic approach for managing and securing technological ecosystems.
Why are information security standards important for businesses?
Information security standards are crucial for businesses as they protect against cybersecurity threats, help in risk management, ensure regulatory compliance, and maintain operational resilience while safeguarding brand reputation.
What components make up information security standards?
Information security standards consist of technical controls (like encryption and firewalls), procedural guidelines (workflow documentation for employee interactions), and organisational frameworks (defining roles, responsibilities, and governance structures).
How are information security standards implemented in an organization?
Implementation involves creating clear organisational policies, establishing governance structures, developing training programs for staff, and putting in place regular monitoring and assessment protocols to identify and mitigate vulnerabilities.