
How to Create Strong Passwords for Enhanced Security
Everyone talks about password security, but hardly anyone does a proper check on their own habits. Take a guess how many people still use ‘123456’ or their birthday as a password. Over 80 percent of hacking breaches involve weak or stolen passwords. Sounds hectic right? The real shock is that most of these risks come from small mistakes that are easy to fix once you know what to look for. So the way you set up and manage your passwords could be the difference between peace of mind and a big financial headache.
Table of Contents
- Step 1: Assess Your Current Password Practices
- Step 2: Identify Key Password Requirements
- Step 3: Generate Complex Passwords Using Tools
- Step 4: Implement A Password Management System
- Step 5: Test And Verify Password Strength
Quick Summary
| Key Point | Explanation |
|---|---|
| 1. Conduct a password audit | Regularly assess passwords across all accounts to identify weaknesses and vulnerabilities. |
| 2. Establish strong password requirements | Set minimum standards like a minimum of 12 characters and a mix of character types to enhance security. |
| 3. Utilize password generation tools | Use reputable tools for creating complex passwords that are hard to guess or crack. |
| 4. Implement a password management system | Centralize password storage with strong encryption and features to ensure regular reviews and updates. |
| 5. Regularly test password strength | Use password assessment tools to verify the resilience of your passwords against potential cyber threats. |
Step 1: Assess Your Current Password Practices
Securing your digital landscape begins with a comprehensive evaluation of your existing password practices. Understanding your current approach is the critical first step in developing robust cybersecurity strategies. Most individuals and organizations unknowingly expose themselves to significant risks through weak or repetitive password management.
Start by conducting a thorough password audit across all your digital platforms and accounts. Open your password manager or review each account systematically. Look for patterns that compromise your security: Are you reusing passwords across multiple platforms? Do your passwords contain easily guessable personal information like birthdates, names, or sequential numbers? These are immediate red flags that signal vulnerability.
Carefully document each account’s current password strength. Learn more about password best practices to understand the specific weaknesses in your existing approach. Professional cybersecurity experts recommend assessing passwords based on several critical criteria:
- Length (minimum 12 characters)
- Complexity (mix of uppercase, lowercase, numbers, symbols)
- Uniqueness (different passwords for each account)
- Age (how long the current password has been in use)
Consider utilizing free online password strength checkers that provide detailed analysis without storing your actual passwords. These tools can generate instant feedback about potential vulnerabilities in your current password strategy. Pay special attention to high-risk accounts like financial services, email, and professional network platforms.
During this assessment, create a comprehensive spreadsheet or secure document tracking each account, its current password strength, and potential improvement areas. This systematic approach transforms an overwhelming task into a manageable process. Remember that password management is not a one-time activity but an ongoing security practice requiring regular review and updates.
By meticulously examining your current password practices, you establish a solid foundation for implementing more advanced security measures. The insights gained from this assessment will directly inform your strategy for creating stronger, more resilient passwords across all your digital platforms.
Step 2: Identify Key Password Requirements
Transitioning from assessing your current password practices, the next critical phase involves establishing comprehensive password requirements that create a robust defense against potential cyber threats. Understanding technical specifications and strategic design is crucial for developing passwords that are both secure and practical.
Begin by recognizing that modern password requirements extend far beyond simple complexity. Read our comprehensive guide on password security to gain deeper insights into creating truly resilient access credentials. Effective password requirements should encompass multiple layers of protection, balancing technical complexity with user manageability.
The fundamental framework for strong password creation involves several non-negotiable criteria. Passwords must be sufficiently long – professional cybersecurity experts recommend a minimum of 12 characters. This length provides exponential increases in computational difficulty for potential hackers attempting unauthorized access. Beyond length, include a diverse mix of character types: uppercase and lowercase letters, numbers, and special symbols. This diversity dramatically increases the potential combination possibilities, making your password substantially more challenging to compromise.
Carefully consider the unique characteristics that make a password truly strong. Avoid using personal information that could be easily discovered through social media or public records. Birthdays, family names, addresses, and predictable numerical sequences are strictly forbidden. Instead, develop passwords that appear completely random to external observers but remain memorable to you through strategic mental techniques.
Key verification criteria for password strength include:
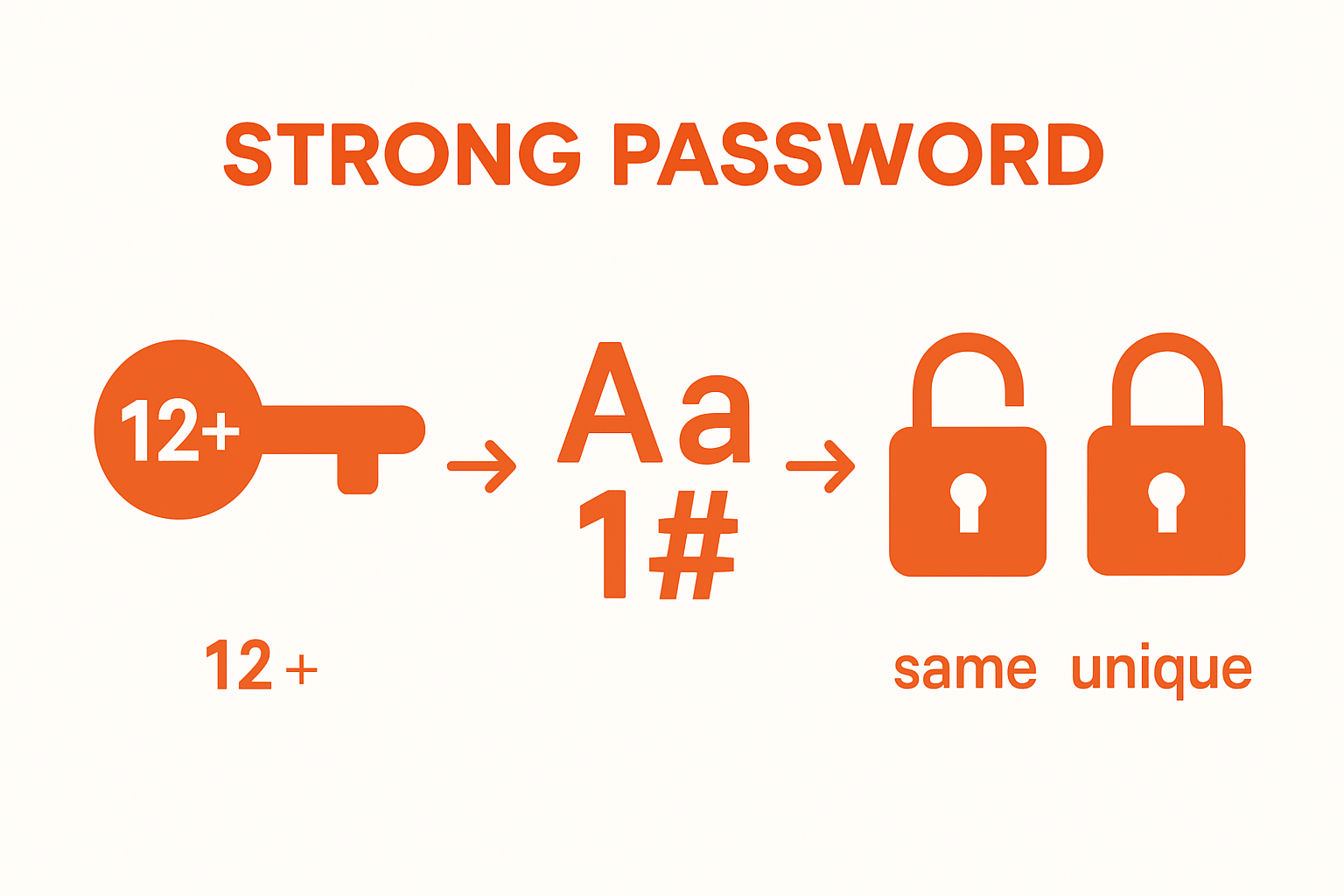
- Contains minimum 12 characters
- Includes at least one uppercase letter
- Includes at least one lowercase letter
- Incorporates numeric characters
- Features special symbols
- Avoids sequential or repetitive patterns
- Excludes personal identifiable information
Consider implementing a password generation strategy that transforms seemingly random elements into a personal mnemonic system. For instance, you might create a password based on a memorable phrase, using its first letters, interspersing numbers and symbols. This approach ensures complexity while maintaining a mental anchor that helps you remember the password without writing it down.
By meticulously establishing these password requirements, you transform your digital security from vulnerable to formidable. Each carefully constructed password becomes a sophisticated barrier protecting your sensitive digital assets against potential intrusion attempts.
Step 3: Generate Complex Passwords Using Tools
Now that you understand password requirements, the next strategic step involves leveraging sophisticated password generation tools to create truly robust digital credentials. Technology provides powerful solutions for generating unbreakable passwords that transcend human memory limitations and predictability patterns.
Learn more about advanced password security techniques and discover how professional-grade tools can transform your cybersecurity approach. Password generation tools eliminate human error by creating mathematically complex sequences that are virtually impossible to guess or crack through traditional methods.
Professional password managers offer comprehensive solutions that extend beyond simple generation. These tools create cryptographically secure passwords, store them encrypted, and can automatically populate login fields across multiple platforms. When selecting a password generation tool, prioritize solutions that offer randomization algorithms, which produce passwords with genuine unpredictability.
The process of generating complex passwords requires strategic thinking.
Begin by identifying a reputable password manager with strong encryption protocols. Many professional-grade tools provide customizable generation parameters, allowing you to specify exact character requirements. Set parameters that match your identified password requirements: minimum 12 characters, mixture of uppercase and lowercase letters, inclusion of numbers and special symbols, and absolute avoidance of personal information.
Consider the following key considerations when utilizing password generation tools:
- Select tools with zero-knowledge encryption
- Verify the tool’s reputation and security track record
- Ensure cross-platform compatibility
- Check for additional security features like two-factor authentication
- Confirm the tool provides secure password storage
Understand that password generation is not a one-time event but an ongoing security practice. Regularly regenerate passwords for critical accounts, especially after potential security incidents or periodic intervals. Most advanced password managers offer automatic password rotation features, systematically updating your credentials to maintain optimal security.
By embracing technological tools designed for password generation, you transform random character creation from a challenging task into a streamlined, secure process. These tools provide a scientifically robust approach to creating passwords that offer maximum protection against potential cyber threats.
Step 4: Implement a Password Management System
Transitioning from password generation to systematic management represents a critical evolution in your cybersecurity strategy. A robust password management system transforms scattered credentials into a centralized, secure ecosystem. This comprehensive approach eliminates the risk of forgotten passwords and significantly reduces vulnerability to potential breaches.
Explore our login security recommendations to understand the nuanced approach required for effective password management. Professional-grade password management systems offer more than simple storage – they provide encryption, cross-platform synchronization, and advanced security features that protect your digital identity.
Begin by selecting a password management solution that aligns with your specific security requirements. Enterprise-level tools provide advanced features like secure sharing, emergency access protocols, and comprehensive audit trails. For individual users, look for solutions offering end-to-end encryption, two-factor authentication, and compatibility across multiple devices and operating systems.
The implementation process requires methodical execution. Start by conducting a comprehensive digital credential inventory, cataloging every account across personal and professional platforms. This audit helps identify redundant or outdated accounts that might pose security risks. During migration, carefully transfer existing passwords into the new management system, ensuring each credential meets your established complexity standards.
Consider these critical implementation strategies:
- Choose a password manager with zero-knowledge encryption
- Enable two-factor authentication within the management system
- Conduct a complete password reset for high-risk accounts
- Establish a regular password rotation schedule
- Create a secure backup of your encrypted password database
Understand that implementing a password management system is not a one-time task but an ongoing security practice. Regularly update the management tool, review stored credentials, and remove unnecessary accounts. Most professional password managers offer automated security scanning features that can identify weak or compromised passwords, providing real-time recommendations for enhancement.
By systematically implementing a comprehensive password management system, you create a proactive defense mechanism that adapts to evolving digital security challenges.
 This approach transforms password management from a reactive task into a strategic, intelligent security protocol that protects your digital ecosystem with precision and sophistication.
This approach transforms password management from a reactive task into a strategic, intelligent security protocol that protects your digital ecosystem with precision and sophistication.
Step 5: Test and Verify Password Strength
After generating and implementing complex passwords, the critical final step involves rigorous testing and verification to ensure your digital credentials provide maximum security. Verification is not a passive process but an active security strategy that demands meticulous examination of each password’s resilience against potential cyber threats.
Explore our comprehensive login security guidelines to understand the nuanced approach required for thorough password validation. Professional cybersecurity experts recommend multiple verification techniques that go beyond basic complexity checks.
Begin by utilizing online password strength assessment tools that provide sophisticated analysis. These platforms simulate various hacking scenarios, measuring your password’s resistance to computational attacks. Look for tools that offer detailed breakdowns of password complexity, including entropy calculations, potential vulnerability points, and estimated time required to crack the password through brute-force methods.
Understand that password verification extends beyond algorithmic testing. Manually review each generated password against established security criteria. Confirm that the password meets all previously defined requirements: minimum length of 12 characters, mixture of character types, absence of personal information, and lack of predictable patterns. This hands-on approach ensures that automated generation tools have not inadvertently created passwords with subtle weaknesses.
Below is a checklist table summarising essential password strength requirements to make it easy to verify if your passwords meet best practice recommendations.
| Password Requirement | Description |
|---|---|
| Minimum Length | At least 12 characters |
| Uppercase Letter | Includes at least one uppercase (capital) letter |
| Lowercase Letter | Includes at least one lowercase letter |
| Numeric Character | Contains at least one number |
| Special Symbol | Features at least one special symbol (e.g. !, @, #, etc.) |
| No Predictable Patterns | Avoids sequential or repetitive patterns |
| No Personal Information | Excludes any personal or easily discovered information |
Consider these critical verification strategies:
- Use multiple password strength checkers for comprehensive assessment
- Test passwords against known dictionary attack databases
- Verify cross-platform compatibility
- Check for unexpected character substitution vulnerabilities
- Confirm password uniqueness across different accounts
Implement a systematic rotation strategy that periodically tests and refreshes passwords. Most professional password managers offer built-in security scanning features that continuously monitor your credentials for potential compromises. These tools can automatically detect if a password has been exposed in previous data breaches, providing real-time recommendations for immediate replacement.
Remember that password verification is an ongoing process, not a one-time checkpoint. Cybersecurity landscapes evolve rapidly, and what constitutes a strong password today might become vulnerable tomorrow. Regular testing, combined with a proactive approach to password management, creates a dynamic defense mechanism that adapts to emerging digital threats. By treating password verification as a continuous, strategic practice, you transform your digital security from reactive protection to intelligent, anticipatory safeguarding.
Move Beyond Passwords: Secure Your Business with Expert IT Solutions
You have learnt how complex passwords and rigorous management protect your business from escalating cyber risks. But are you truly protected if your entire IT environment remains vulnerable or if password management becomes overwhelming as your team grows? Many companies struggle to ensure every user follows best practice, putting sensitive data at risk through reused or weak passwords, forgotten credentials, or inconsistent security policies. Protecting your passwords is only one part of the larger cybersecurity puzzle.
Imagine the peace of mind when every layer of your IT network, cloud platform and workstation is secured by professionals. At Techtron, we offer comprehensive cybersecurity and managed IT support tailored for South African businesses like yours. Want more than just password tips and DIY management? Discover how our proactive solutions keep your systems compliant and safe while giving you more time to focus on what matters most. Strengthen your defences and secure your digital assets now with a partner who treats your business as their own. Visit Techtron today to get started.
Frequently Asked Questions
How can I assess the strength of my current passwords?
You can assess your current passwords by conducting a password audit. This includes checking each password for length, complexity, uniqueness, and age. You can also utilize online password strength checkers to identify vulnerabilities without storing your actual passwords.
What are the key requirements for creating strong passwords?
Strong passwords should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and special symbols. Avoid using easily guessable personal information and predictable patterns.
How can I generate complex passwords easily?
You can use password generation tools provided by reputable password managers. These tools create cryptographically secure passwords based on your specified parameters (like length and character type) and eliminate human error in the password creation process.
What steps should I take to manage my passwords securely?
Implement a password management system that encrypts and securely stores your passwords. Conduct regular reviews, update stored passwords, and enable two-factor authentication. Additionally, set a schedule for password rotation to maintain optimal security.