Cyber Risk Assessment Process for Modern Businesses 2025
Cyber attacks are hitting businesses harder than ever and the costs keep climbing. Some estimates peg global cybercrime damages at over R150 trillion by 2025. You’d think most companies have their cyber risk assessment sorted by now, right? The reality is hardly anyone is keeping up with how fast threats are evolving. Even top companies miss out on hidden gaps that turn small slip-ups into business disasters.
Table of Contents
- Key Steps In The Cyber Risk Assessment Process
- Identifying And Prioritising Business Risks
- Implementing Solutions And Monitoring Progress
- Best Practices For Outsourced IT And Compliance
Quick Summary
| Takeaway | Explanation |
|---|---|
| Identify and classify assets clearly | A thorough inventory of information assets helps organizations understand their value and the impact of potential breaches. |
| Prioritize risks based on impact | Assess risks by their potential financial impact and likelihood, allowing for targeted resource allocation towards high-priority threats. |
| Implement dynamic risk management | Create an adaptive risk management framework that includes ongoing monitoring and regular reviews to stay ahead of emerging cybersecurity challenges. |
| Conduct thorough supplier assessments | Rigorous evaluation of outsourced IT partners ensures compliance and reduces cybersecurity vulnerabilities in supplier relationships. |
| Maintain continuous monitoring processes | Utilize advanced monitoring tools for real-time insights into cybersecurity postures, supporting proactive threat detection and response. |
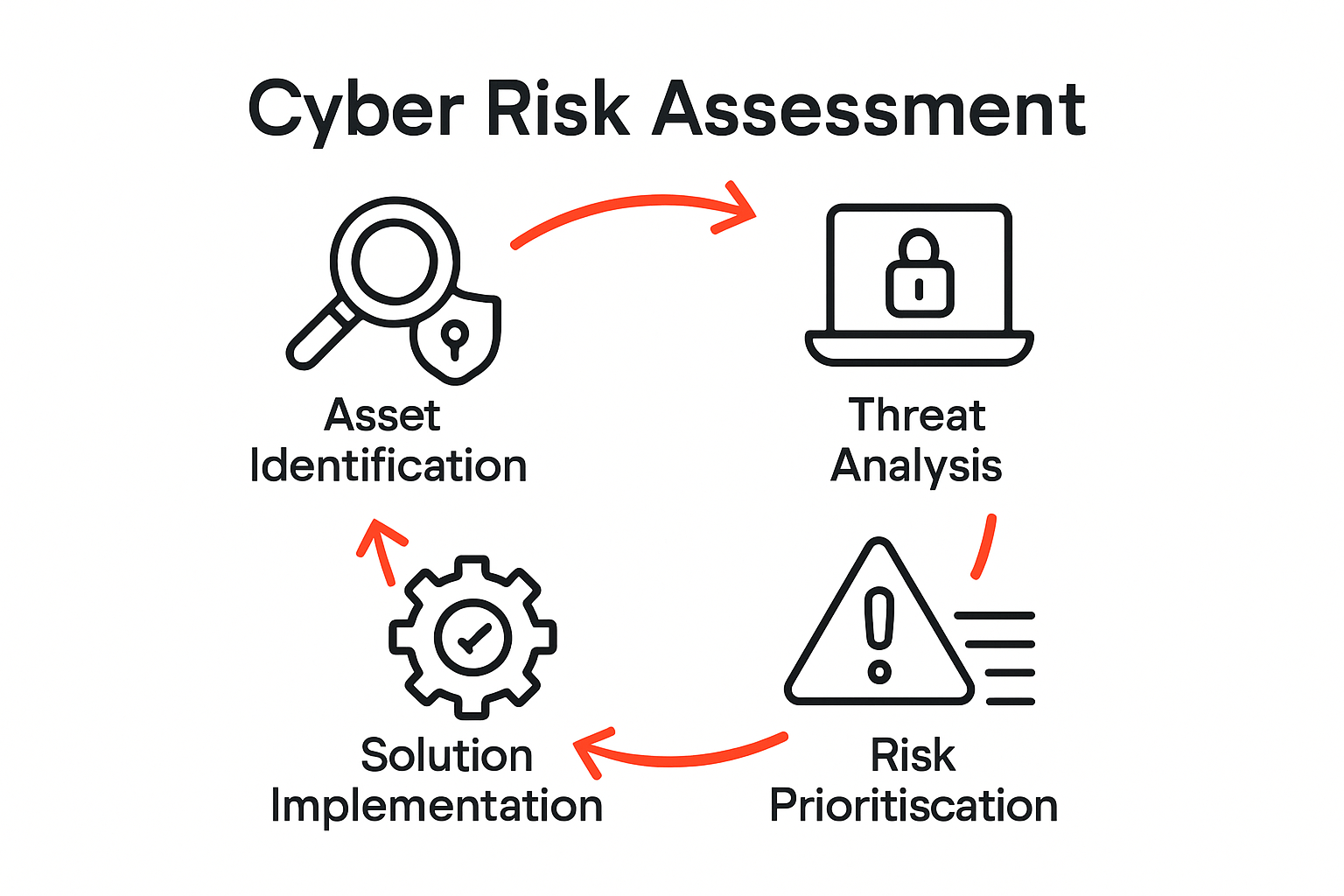
Key Steps in the Cyber Risk Assessment Process
A comprehensive cyber risk assessment process requires strategic planning and systematic execution. Modern businesses must adopt a proactive approach to identifying, evaluating, and mitigating potential cybersecurity threats. By understanding and implementing a structured methodology, organizations can effectively safeguard their digital assets and minimize potential vulnerabilities.
Identifying and Classifying Information Assets
The initial phase of the cyber risk assessment process involves meticulously identifying and categorizing an organization’s information assets. According to EC-Council, this step is crucial for understanding the scope and value of digital resources. Organizations must create a comprehensive inventory of hardware, software, data repositories, network infrastructure, and cloud-based systems.
Classification helps prioritize assets based on their criticality and sensitivity. Businesses should evaluate each asset’s potential impact if compromised, considering factors such as financial value, regulatory compliance requirements, and operational significance. This systematic approach enables security teams to allocate resources more effectively and develop targeted protection strategies.

Analyzing Threats and Implementing Mitigation Strategies
Once assets are identified, the next critical step involves thoroughly analyzing potential threats and vulnerabilities. Security Boulevard recommends a comprehensive threat identification process that examines internal and external risk factors. This includes evaluating potential cybersecurity risks such as malware infections, phishing attacks, unauthorized access attempts, and system vulnerabilities.
The analysis should involve detailed risk prioritization, considering the likelihood and potential impact of each identified threat. Organizations must develop targeted mitigation strategies that address specific vulnerabilities, implementing controls such as multi-factor authentication, encryption protocols, network segmentation, and robust access management procedures. The goal is to create a dynamic defense mechanism that adapts to evolving cybersecurity challenges.
Continuous Monitoring and Risk Review
Cybersecurity is not a one-time activity but an ongoing process requiring continuous monitoring and periodic reassessment. According to ISO/IEC 27005, organizations must establish mechanisms for regular risk evaluation and control effectiveness tracking. This involves implementing advanced monitoring tools, conducting periodic vulnerability assessments, and maintaining an adaptive security framework.
Effective continuous monitoring includes real-time threat detection, log analysis, security information and event management (SIEM) systems, and regular penetration testing. By maintaining a proactive stance, businesses can quickly identify and respond to emerging threats, minimizing potential damage and maintaining robust cybersecurity postures.
The cyber risk assessment process is a dynamic and complex undertaking that requires strategic thinking, technical expertise, and a commitment to ongoing improvement. Businesses that invest time and resources in developing comprehensive risk management frameworks will be better positioned to protect their digital assets and maintain operational resilience in an increasingly challenging cybersecurity environment.
Here’s a table summarising the core steps of the cyber risk assessment process and the key focus for each:
| Step | Key Focus |
|---|---|
| Identify & Classify Assets | Inventory all digital and physical information assets, assess value and criticality |
| Analyse Threats & Vulnerabilities | Identify internal/external threats, examine likelihood and potential impact |
| Implement Mitigation Strategies | Apply controls (MFA, encryption, segmentation) based on risk analysis |
| Continuous Monitoring & Review | Use monitoring tools, conduct ongoing assessments, adapt defences as threats evolve |
Identifying and Prioritising Business Risks
Effective cybersecurity risk management begins with a strategic approach to identifying and prioritizing potential business risks. Organizations must develop a comprehensive framework that goes beyond traditional security measures, integrating risk assessment into broader business strategy and operational planning.
Comprehensive Risk Landscape Assessment
Modern businesses face a complex and dynamic risk environment that requires sophisticated identification techniques. According to NIST, enterprise risk management demands a holistic approach that connects cybersecurity risks directly to organizational objectives. This process involves mapping potential vulnerabilities across multiple dimensions, including technological infrastructure, human factors, regulatory compliance, and strategic business operations.
The risk identification process should encompass both internal and external threat vectors. This includes analyzing potential cybersecurity challenges such as data breaches, system vulnerabilities, third-party vendor risks, emerging technological threats, and potential compliance gaps. Organizations must conduct thorough assessments that consider the unique characteristics of their industry, technological ecosystem, and specific operational context.
Risk Prioritization and Strategic Alignment
KPMG’s 2025 Cybersecurity Considerations emphasizes the critical importance of aligning cybersecurity risk management with broader business objectives. Prioritization is not merely about identifying risks but understanding their potential impact on organizational performance, financial stability, and strategic goals.
Effective risk prioritization involves a systematic approach that evaluates risks based on multiple criteria. Key factors include potential financial impact, likelihood of occurrence, potential disruption to business operations, reputational damage, and regulatory consequences. Organizations should develop a sophisticated risk scoring mechanism that allows for nuanced assessment and targeted resource allocation.
Implementing Dynamic Risk Management Frameworks
As outlined by ISO/IEC 27005, successful risk management requires a dynamic and adaptive framework. This approach goes beyond static risk assessment, creating a continuous process of identification, evaluation, and mitigation. Organizations must establish robust mechanisms for ongoing risk monitoring, including regular vulnerability assessments, threat intelligence gathering, and periodic strategic reviews.
The most effective risk management strategies incorporate advanced technologies such as artificial intelligence and machine learning to enhance threat detection and predictive analysis. These tools enable businesses to move from reactive to proactive risk management, anticipating potential challenges before they materialize.
Successful risk identification and prioritization is not a one-time exercise but a continuous, evolving process. Businesses must cultivate a culture of risk awareness, integrating cybersecurity considerations into every level of organizational strategy. By developing a comprehensive, adaptive approach to risk management, organizations can transform potential vulnerabilities into strategic opportunities for enhanced resilience and competitive advantage.
Here’s a comparison table outlining key factors for risk prioritization discussed in this section:
| Factor | Description |
|---|---|
| Financial Impact | Potential cost or revenue loss from a risk event |
| Likelihood | Probability of the risk materialising |
| Business Disruption | Degree to which normal operations would be affected |
| Reputational Damage | Impact on public trust and organisational image |
| Regulatory Consequences | Possible legal or compliance implications |
Implementing Solutions and Monitoring Progress
Implementing cybersecurity solutions and establishing robust monitoring mechanisms are critical components of an effective risk management strategy. Organizations must develop comprehensive approaches that transform identified risks into actionable mitigation strategies while maintaining continuous oversight and adaptability.
Strategic Solution Implementation
Successful cybersecurity solution implementation requires a multi-layered and nuanced approach that goes beyond standard technical controls. Businesses must develop tailored strategies that address specific organizational vulnerabilities while maintaining flexibility and scalability. This involves selecting and deploying advanced security technologies, developing comprehensive policy frameworks, and creating integrated defense mechanisms that protect critical digital assets.
Key implementation strategies include deploying multi-factor authentication systems, implementing advanced endpoint protection platforms, establishing secure network segmentation, and developing robust encryption protocols. Organizations should prioritize solutions that provide comprehensive coverage while remaining adaptable to evolving technological landscapes.
Continuous Monitoring and Performance Tracking
According to CMS Cyber Risk Management Plan, effective monitoring requires sophisticated dashboards and reporting mechanisms that provide real-time insights into organizational cybersecurity postures. These tools enable businesses to track security performance, identify potential vulnerabilities, and respond proactively to emerging threats.
Continuous monitoring involves implementing advanced security information and event management (SIEM) systems, conducting regular vulnerability assessments, and maintaining comprehensive log analysis capabilities. Organizations must develop metrics and key performance indicators that provide meaningful insights into their security effectiveness, allowing for data-driven decision-making and ongoing risk management.
Adaptive Risk Management and Improvement
Cybersecurity is a dynamic field requiring constant evolution and refinement. Successful organizations view their risk management strategies as living frameworks that must be regularly reassessed and updated. This involves establishing feedback loops that capture lessons learned from security incidents, technological changes, and emerging threat landscapes.
Periodic comprehensive reviews should examine the effectiveness of implemented solutions, identify potential gaps, and develop strategies for continuous improvement. This might include conducting regular penetration testing, engaging external cybersecurity experts for independent assessments, and maintaining a culture of ongoing learning and adaptation.
The ultimate goal of implementing solutions and monitoring progress is not merely to achieve temporary security but to create a resilient, adaptive organizational approach to cybersecurity. By developing comprehensive strategies that combine advanced technologies, strategic planning, and continuous improvement, businesses can transform potential vulnerabilities into opportunities for enhanced digital resilience and operational excellence.
Best Practices for Outsourced IT and Compliance
Outsourced IT management requires a strategic approach to cybersecurity and compliance that goes beyond traditional vendor relationships. Modern businesses must develop comprehensive frameworks that ensure robust protection, regulatory adherence, and seamless operational integration when engaging external technology partners.
Supplier Risk Management and Due Diligence
Effective outsourced IT governance begins with rigorous supplier selection and continuous risk assessment. According to the Australian Cyber Security Centre, organizations must implement comprehensive cyber supply chain risk management activities during the earliest stages of procurement. This involves thorough evaluation of potential technology partners, examining their security protocols, compliance certifications, and historical performance in managing digital risks.
Businesses should develop detailed supplier relationship management policies that include comprehensive background checks, ongoing performance monitoring, and clear contractual expectations regarding cybersecurity standards. Creating an approved supplier list helps ensure that critical applications, IT equipment, and services are sourced from trusted providers with proven track records of security and reliability.
Compliance and Security Framework Alignment
The U.S. Department of Labor emphasizes the critical importance of conducting annual risk assessments and independent security audits. Organizations must ensure that outsourced IT partners align with their specific regulatory requirements and maintain transparent reporting mechanisms. This involves developing clear information security roles and responsibilities, with senior executive oversight to guarantee comprehensive compliance management.
Key compliance considerations include data protection regulations, industry-specific security standards, and international cybersecurity frameworks. Organizations should explore service agreement options that provide flexible yet robust protection mechanisms, allowing for adaptive security strategies that can evolve with changing technological and regulatory landscapes.
Continuous Monitoring and Performance Evaluation
Successful outsourced IT management requires establishing robust monitoring and evaluation processes. Organizations must implement comprehensive performance tracking mechanisms that go beyond traditional service level agreements. This includes regular security assessments, vulnerability testing, and detailed reporting frameworks that provide real-time insights into the effectiveness of external IT partnerships.
Effective monitoring strategies should incorporate advanced technological tools that enable continuous visibility into system performance, security incidents, and potential compliance gaps. Regular independent audits and penetration testing can provide additional layers of assurance, helping organizations identify and address potential vulnerabilities before they become critical risks.
Navigating the complex landscape of outsourced IT and compliance demands a proactive, strategic approach. By developing comprehensive supplier management frameworks, maintaining rigorous compliance standards, and establishing continuous monitoring mechanisms, businesses can transform potential technological vulnerabilities into opportunities for enhanced operational efficiency and security.
Frequently Asked Questions
What is a cyber risk assessment process?
A cyber risk assessment process is a structured methodology that businesses use to identify, evaluate, and mitigate potential cybersecurity threats to their digital assets. It involves steps like classifying information assets, analyzing threats, implementing mitigation strategies, and maintaining continuous monitoring.
Why is it important for businesses to conduct a cyber risk assessment?
Conducting a cyber risk assessment is crucial for businesses to understand their vulnerabilities, prioritize risks, and allocate resources effectively. This proactive approach helps in safeguarding digital assets and minimizing the impact of potential cyber threats.
What are key steps in the cyber risk assessment process?
The key steps in the cyber risk assessment process include identifying and classifying information assets, analyzing threats and vulnerabilities, implementing mitigation strategies, and engaging in continuous monitoring and risk review to adapt to emerging challenges.
How often should businesses conduct a cyber risk assessment?
Businesses should conduct cyber risk assessments regularly, ideally at least annually, and also whenever there are significant changes to the IT environment or business operations. Continuous monitoring and periodic reviews ensure that organizations stay ahead of evolving threats.
Strengthen Your Cyber Risk Strategy with Trusted IT Experts
Modern risks require more than quick fixes. In the article above, you discovered how complex and relentless cyber threats have become, with hidden gaps and constant change posing real danger to business resilience. If you feel anxious about tracking and managing continuously evolving risks, you are not alone. Many companies struggle to keep up with proactive asset classification, threat mitigation and ongoing monitoring. These are not just tick-box activities. They demand specialised systems and experience to protect your digital environment and meet compliance demands, especially as your organisation grows.
At Techtron, our focus is on removing the technical burdens holding you back. With enterprise-grade cybersecurity and managed IT support, we design smart frameworks for asset protection, vulnerability assessment and seamless compliance. If your business needs to secure Microsoft 365, Azure, or your on-premises network, our team can help you implement dynamic risk management, advanced monitoring and tailored recovery solutions. Ready to transform your cyber risk concerns into confidence? Visit Techtron today to safeguard your information assets, reduce uncertainty and propel your business forward. The right step now could prevent tomorrow’s costly setback.