Cybersecurity Best Practices for 2025: A Guide for SA Businesses
South African businesses are staring down a wave of new cyberattacks and digital threats, and the stakes have never been higher. The average cost of a data breach in 2024 has surged to R55 million, showing just how much is on the line for companies of every size. You might think that only the big corporates need to worry. But in truth, the smaller guys are just as much in the crosshairs—and most don’t realise how a few simple changes can be the difference between a normal workday and total chaos.
Table of Contents
- Understanding Today’s Cybersecurity Threats
- Core Cybersecurity Best Practices for 2025
- Building a Culture of Security Awareness
- Choosing the Right IT Management Solutions
Quick Summary
| Takeaway | Explanation |
|---|---|
| Focus on Multi-Layered Security | Implement a comprehensive security framework to protect against evolving threats effectively. |
| Emphasize Identity Management | Adopt strong authentication measures to safeguard sensitive information and access rights. |
| Adopt Adaptive Security Practices | Utilize AI and machine learning for real-time threat detection and response improvements. |
| Cultivate a Security-Aware Culture | Ensure all employees understand their role in maintaining cybersecurity and actively participate. |
| Implement Strategic IT Management Solutions | Choose IT management systems that are scalable and can evolve with technological advancements. |
Understanding Today’s Cybersecurity Threats
Cybersecurity threats continue to evolve at an unprecedented pace, presenting significant challenges for businesses across all sectors. The digital landscape is becoming increasingly complex, with sophisticated attackers developing more advanced techniques to breach organizational defenses.
The Escalating Threat Landscape
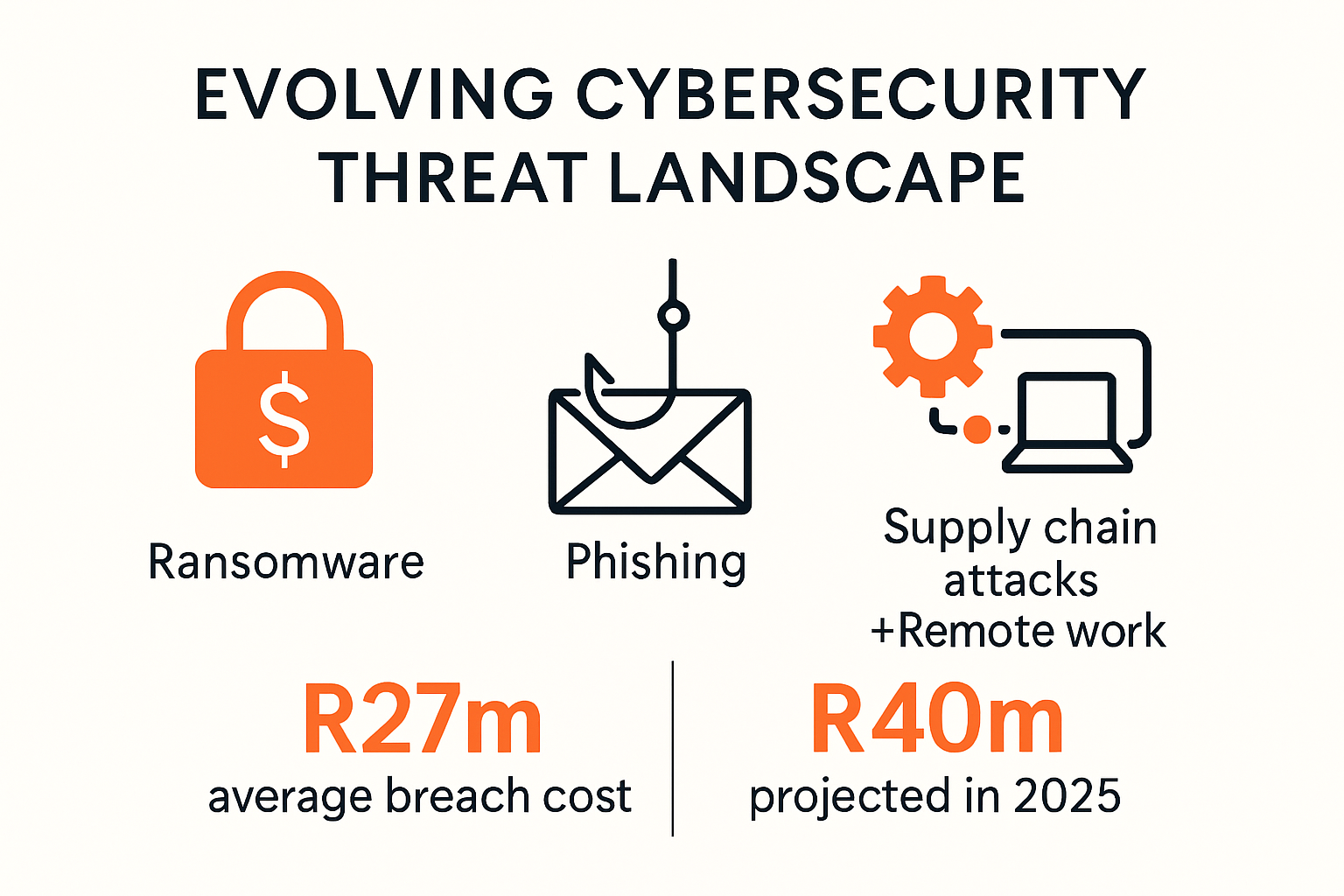
Modern cybersecurity threats have transformed from simple malware attacks to highly orchestrated, strategic operations. Research from IBM Security reveals that the average cost of a data breach in 2024 reached R55 million, demonstrating the substantial financial risks businesses face. Cybercriminals are no longer lone actors but often operate as organized networks with advanced technological capabilities.
Primary threat categories now include:
- Ransomware Evolution: Advanced ransomware attacks targeting critical infrastructure and business-sensitive systems
- Social Engineering: Sophisticated phishing techniques exploiting human psychology
- Supply Chain Vulnerabilities: Attacks targeting interconnected business networks
Emerging Attack Vectors
The proliferation of remote work and cloud technologies has dramatically expanded potential entry points for cybercriminals. Gartner’s Cybersecurity Forecast indicates that by 2025, 75% of security breaches will result from inadequate management of digital identities and access rights. This statistic underscores the critical need for comprehensive identity and access management strategies.
Businesses must recognize that cybersecurity is no longer just an IT problem but a fundamental business risk management issue. Threat actors are increasingly targeting small and medium enterprises, viewing them as easier targets with potentially weaker security infrastructures.
Strategic Threat Intelligence
Successful cybersecurity defense requires continuous monitoring, proactive threat intelligence, and adaptive security frameworks. Organizations need to move beyond reactive approaches and develop predictive capabilities that anticipate and mitigate potential security incidents before they occur.
This involves implementing robust threat detection strategies that leverage advanced technologies like artificial intelligence and machine learning to identify and respond to potential security breaches in real time. The goal is not just prevention but rapid detection and mitigation.
Understanding these evolving threats is the first critical step in developing a comprehensive cybersecurity strategy that protects an organization’s digital assets, reputation, and operational continuity.
To help clarify the primary threat categories faced by South African businesses, here is a summary table:
| Threat Category | Description | Example Target |
|---|---|---|
| Ransomware Evolution | Advanced ransomware attacking key infrastructure and systems | Financial, healthcare |
| Social Engineering | Sophisticated phishing exploiting human psychology | Employees (all sectors) |
| Supply Chain Vulnerabilities | Attacks targeting interconnected business networks | SMEs, B2B enterprises |
Core Cybersecurity Best Practices for 2025
As cybersecurity threats become increasingly sophisticated, organizations must adopt comprehensive and proactive defense strategies. The core cybersecurity best practices for 2025 focus on holistic protection, adaptive technologies, and strategic risk management.
Multi-Layered Security Approach
Cybersecurity research from Deloitte emphasizes the critical importance of implementing a multi-layered security framework. This approach moves beyond traditional perimeter defenses to create a comprehensive protection strategy. Key components include endpoint protection, network segmentation, advanced threat detection, and continuous monitoring.
Critical elements of a multi-layered security strategy involve:
- Zero Trust Architecture: Implementing strict access controls that verify every user and device
- Advanced Encryption: Protecting data at rest and in transit
- Continuous Vulnerability Assessment: Regular security audits and penetration testing
Identity and Access Management
Modern cybersecurity demands robust identity management. Gartner’s Identity Management Report highlights that by 2025, 80% of organizations will implement strong authentication mechanisms. This includes multi-factor authentication, biometric verification, and sophisticated access control protocols.
Businesses must develop comprehensive identity management strategies that:
- Eliminate password-based authentication
- Implement real-time access monitoring
- Create granular access controls based on user roles
- Develop rapid user access revocation processes
Adaptive Security and Continuous Learning
Cybersecurity is no longer a static defense but a dynamic, evolving discipline. Organizations need to embrace emerging security technologies that leverage artificial intelligence and machine learning for predictive threat detection. This approach allows businesses to anticipate and mitigate potential security risks before they materialize.
Key adaptive security practices include:
- Implementing AI-driven threat intelligence
- Developing real-time incident response protocols
- Creating automated security update mechanisms
- Investing in continuous employee cybersecurity training
The most effective cybersecurity strategy combines technological solutions with human expertise. Organizations must foster a culture of security awareness, ensuring that every team member understands their role in maintaining robust digital defenses. This holistic approach transforms cybersecurity from a technical challenge to a fundamental business strategy.
Building a Culture of Security Awareness
Cybersecurity is no longer exclusively a technical challenge but a comprehensive organizational responsibility that requires active participation from every team member. Creating a robust security awareness culture transforms employees from potential vulnerability points into proactive defenders of organizational digital assets.
Foundational Security Education
Research from the National Institute of Standards and Technology emphasizes that effective security awareness goes beyond periodic training sessions. Organizations must integrate cybersecurity principles into daily operational practices, making security an inherent part of workplace behavior.
Key components of foundational security education include:
- Continuous Learning: Regular and engaging cybersecurity training modules
- Practical Scenarios: Real-world simulation of potential security threats
- Role-Specific Training: Customized learning paths based on job responsibilities

Developing Personal Responsibility
ISACA’s cybersecurity insights highlight the importance of individual accountability in maintaining organizational security. Employees must understand that cybersecurity is not just an IT department’s responsibility but a shared organizational commitment.
Strategies to foster personal responsibility include:
- Creating clear communication channels for reporting potential security incidents
- Recognizing and rewarding proactive security behaviors
- Implementing transparent consequences for security policy violations
Strategic Awareness Implementation
TechTarget’s cybersecurity culture framework suggests a holistic approach to security awareness that transcends traditional training methods. This involves creating an environment where security considerations are integrated into every business decision and technological interaction.
Effective implementation requires:
- Executive leadership visibly championing security initiatives
- Cross-departmental collaboration in developing security strategies
- Regular assessment and adaptation of security awareness programs
Businesses must view security awareness as an ongoing journey, not a destination. By cultivating a proactive, informed, and engaged workforce, organizations can significantly reduce their vulnerability to cyber threats. The goal is to create an environment where every employee becomes a knowledgeable and vigilant guardian of the organization’s digital ecosystem.
To summarise approaches for building a strong security awareness culture, here’s a process overview:
| Step | Key Activities |
|---|---|
| Foundational Security Education | Ongoing training, real-world simulations, role resource |
| Personal Responsibility | Clear reporting, reward positive behaviours, enforce rules |
| Strategic Implementation | Leadership buy-in, cross-team collaboration, assess regularly |
Choosing the Right IT Management Solutions
Selecting appropriate IT management solutions is a critical strategic decision that directly impacts an organization’s cybersecurity posture, operational efficiency, and long-term technological resilience. In 2025, businesses must look beyond traditional IT support models and embrace comprehensive, adaptive solutions that align with evolving digital landscapes.
Strategic Solution Assessment
NIST Special Publication 800-171 provides comprehensive guidelines for evaluating IT management solutions, emphasizing the importance of selecting tools that meet rigorous security and performance standards. Organizations must conduct thorough assessments that go beyond surface-level capabilities.
Key evaluation criteria include:
- Scalability: Solution’s ability to grow with organizational needs
- Integration Capabilities: Seamless compatibility with existing technological infrastructure
- Security Compliance: Alignment with industry-specific regulatory requirements
- Advanced Threat Protection: Robust mechanisms for detecting and mitigating potential security risks
Managed vs. Co-Managed IT Services
Businesses face a critical decision in determining the most appropriate IT management approach. Research from Gartner indicates that by 2025, 65% of organizations will leverage hybrid IT management models that combine internal expertise with external specialized support.
Considerations for choosing between managed and co-managed services include:
- Assessing internal technological capabilities
- Understanding specific organizational security requirements
- Evaluating budget constraints and potential cost efficiencies
- Determining desired level of direct technological control
Future-Proofing IT Management Strategies
Modern IT management solutions must be adaptive and forward-looking. Our guide on service agreements highlights the importance of selecting flexible solutions that can rapidly respond to emerging technological challenges.
Essential future-proofing strategies involve:
- Implementing solutions with robust artificial intelligence and machine learning capabilities
- Developing agile technological frameworks
- Creating comprehensive disaster recovery and business continuity plans
- Establishing continuous monitoring and adaptive security protocols
The most effective IT management solutions transcend traditional technical support. They represent strategic partnerships that enable businesses to navigate complex digital ecosystems, protect critical assets, and maintain competitive advantage. Organizations must view these solutions as dynamic, evolving tools that require continuous assessment, refinement, and alignment with broader business objectives.
Frequently Asked Questions
What are the main cybersecurity threats facing South African businesses in 2025?
Cyber South African businesses face threats such as advanced ransomware attacks, social engineering techniques like phishing, and vulnerabilities within supply chains. These threats have evolved significantly, targeting both large corporates and smaller enterprises.
How can businesses implement a multi-layered security approach?
To implement a multi-layered security approach, businesses should adopt a zero trust architecture, use advanced encryption methods, and conduct continuous vulnerability assessments. This creates comprehensive protection against evolving cyber threats.
Why is identity and access management crucial for cybersecurity?
Identity and access management (IAM) is crucial because it ensures that only authorized users have access to sensitive information and resources. Implementing strong authentication methods, such as multi-factor authentication, reduces the risk of unauthorized access to critical systems.
What role does employee training play in improving cybersecurity?
Employee training plays a vital role in building a culture of security awareness within an organization. Continuous education and practical simulations help employees understand their responsibilities in maintaining cybersecurity, thereby reducing vulnerabilities associated with human error.
Take Charge of Your Cybersecurity Future with Expert Support
When you read about the latest cyber threats and see the rising cost of data breaches in South Africa, it’s clear that businesses can no longer take a wait-and-see approach. The article shows how gaps in identity management, weak multi-layered security, and lack of ongoing employee awareness can turn a simple mistake into a disaster. If you recognise your own challenges in monitoring sophisticated risks or building a culture of security, you’re not alone. Many firms struggle to keep up, especially without a dedicated IT partner.
Why risk your reputation and hard-earned growth? Let Techtron help you build the advanced, adaptive defences your business needs. Our managed and co-managed IT services deliver the proactive security, network protection, and cloud expertise highlighted in this guide. Find out how our approach to IT management solutions can close your security gaps, reduce your technical burden, and give you peace of mind. Visit https://techtron.co.za today to speak to our team and secure your place ahead of emerging cyber threats.