Understanding the Future of Cloud Security
Cloud security used to be as simple as putting up firewalls and hoping for the best. Now things could not be more different. Artificial intelligence and predictive analytics are changing the way we defend digital assets, with modern systems capable of detecting threats before they even happen. Few people realise how far cloud security has come. The real surprise is it is not only keeping hackers out but also giving businesses a serious edge in the race for digital survival.
Table of Contents
- The Evolution Of Cloud Security: A Historical Perspective
- Why Cloud Security Is Crucial For Modern Businesses
- Key Trends Shaping The Future Of Cloud Security
- Understanding Emerging Technologies In Cloud Security
- Real-World Impacts Of Enhanced Cloud Security Measures
Quick Summary
| Takeaway | Explanation |
|---|---|
| Proactive security measures are essential | Modern cloud security must anticipate threats rather than simply respond to them. Organizations should implement strategies like zero trust and continuous monitoring. |
| Data breaches can devastate finances | Businesses face dire financial consequences from data theft, including loss of revenue, legal penalties, and reputational harm after security incidents. |
| Robust encryption safeguards sensitive information | Encryption is a crucial defense layer to protect intellectual property and customer data in cloud environments against unauthorized access and breaches. |
| Zero trust architecture enhances security posture | This approach verifies every access request, minimizing vulnerabilities and ensuring that trust is never assumed in network interactions. |
| AI-driven technologies are revolutionizing defense mechanisms | Artificial intelligence enables real-time threat detection and automated responses, allowing organizations to stay ahead of potential security risks. |
The Evolution of Cloud Security: A Historical Perspective
Cloud security has undergone a transformative journey from basic infrastructure protection to sophisticated, adaptive defence mechanisms. Understanding this historical progression provides critical insights into how organisations can safeguard their digital assets.
The Early Days of Cloud Computing Security
In the initial phase of cloud computing, security was viewed through a traditional lens of network perimeter defence. Businesses predominantly relied on firewall technologies and basic encryption methods to protect their digital environments. Research from the University of Pretoria revealed that early cloud adoption was significantly hindered by fundamental security concerns.
Key challenges during this period included:
- Limited understanding of cloud infrastructure vulnerabilities
- Inadequate authentication protocols
- Minimal data encryption standards
- Lack of standardised security frameworks
Emergence of Advanced Security Paradigms
As cloud technologies matured, security strategies evolved from reactive to proactive models. Organisations began implementing more sophisticated approaches such as zero trust architectures, multi factor authentication, and continuous monitoring systems. Comprehensive security now involves anticipating potential threats rather than simply responding to breaches.
This transformation was driven by several critical factors:
- Increasing complexity of cyber threats
- Regulatory compliance requirements
- Growing sophistication of malicious actors
- Expansion of distributed computing environments
Modern Cloud Security Landscape
Today’s cloud security represents a complex ecosystem of advanced technological solutions. Machine learning algorithms, artificial intelligence, and predictive analytics have become integral to identifying and mitigating potential security risks before they manifest. Research from the South African Computer Journal highlighted that trust and information security remain paramount concerns for organisations adopting cloud technologies.
The future of cloud security will continue to be shaped by ongoing technological innovations, emerging threat landscapes, and the persistent need to balance robust protection with operational flexibility.
To help clarify how cloud security has evolved, the table below compares the key characteristics of each major phase described in the article.
| Cloud Security Era | Main Features/Approaches | Key Challenges |
|---|---|---|
| Early Days | Perimeter defence, basic firewalls, limited encryption | Inadequate protocols, minimal encryption, unclear risks |
| Advanced Security Paradigms | Zero trust models, multi factor authentication, proactive monitoring | Complex threats, compliance demands, distributed environments |
| Modern Cloud Security Landscape | AI, machine learning, predictive analytics, adaptive systems | Maintaining trust, balancing flexibility and robust defence |
Why Cloud Security is Crucial for Modern Businesses
Cloud security has transitioned from a technical consideration to a fundamental business imperative. As organisations increasingly migrate their critical operations and sensitive data to cloud environments, understanding the strategic importance of robust security measures becomes paramount.
The Financial and Reputational Stakes
Data breaches represent far more than technical failures. They are potentially catastrophic events that can devastate an organisation’s financial stability and reputation. Research from the Cloud Security Alliance South Africa Chapter demonstrates that businesses facing significant security incidents can experience substantial financial losses, with some estimates suggesting recovery costs can exceed millions of rand.
Key financial risks include:
- Direct monetary losses from data theft
- Regulatory compliance penalties
- Potential legal liability
- Long-term reputation damage
- Customer trust erosion
Protecting Critical Business Assets
Modern businesses operate in a digital ecosystem where data represents their most valuable asset. Cloud security is not merely about preventing unauthorized access but creating a comprehensive defence mechanism that safeguards intellectual property, customer information, and operational intelligence. This protection encompasses multiple layers of technological and procedural safeguards designed to prevent, detect, and respond to potential security threats.
Critical protection domains include:
- Encryption of sensitive data
- Access control management
- Continuous threat monitoring
- Incident response planning
- Regulatory compliance adherence
Strategic Business Resilience
Effective cloud security transcends traditional defensive strategies. It enables businesses to leverage cloud technologies confidently, supporting innovation, scalability, and competitive advantage. By implementing robust security frameworks, organisations can mitigate risks while maintaining the agility required in rapidly evolving digital markets.
The future of business success will be intrinsically linked to an organisation’s ability to secure its digital infrastructure, making cloud security not just a technical requirement but a strategic business enabler.
Key Trends Shaping the Future of Cloud Security
Cloud security is rapidly evolving, driven by technological advancements, emerging threats, and the dynamic needs of modern organisations. Understanding these transformative trends is crucial for businesses seeking to maintain robust digital defences and strategic technological resilience.
Artificial Intelligence and Predictive Security
Artificial intelligence is revolutionising cloud security by enabling proactive threat detection and intelligent risk management. Machine learning algorithms can now analyse massive datasets, identifying potential vulnerabilities and anomalous behaviour patterns with unprecedented speed and accuracy. Research from the University of Johannesburg underscores the critical role of advanced technological skills in developing sophisticated security solutions.
Key AI-driven security capabilities include:

- Real-time threat detection
- Automated incident response
- Predictive vulnerability assessment
- Intelligent access management
- Continuous learning and adaptation
Zero Trust Architecture and Enhanced Authentication
Traditional perimeter-based security models are becoming obsolete.
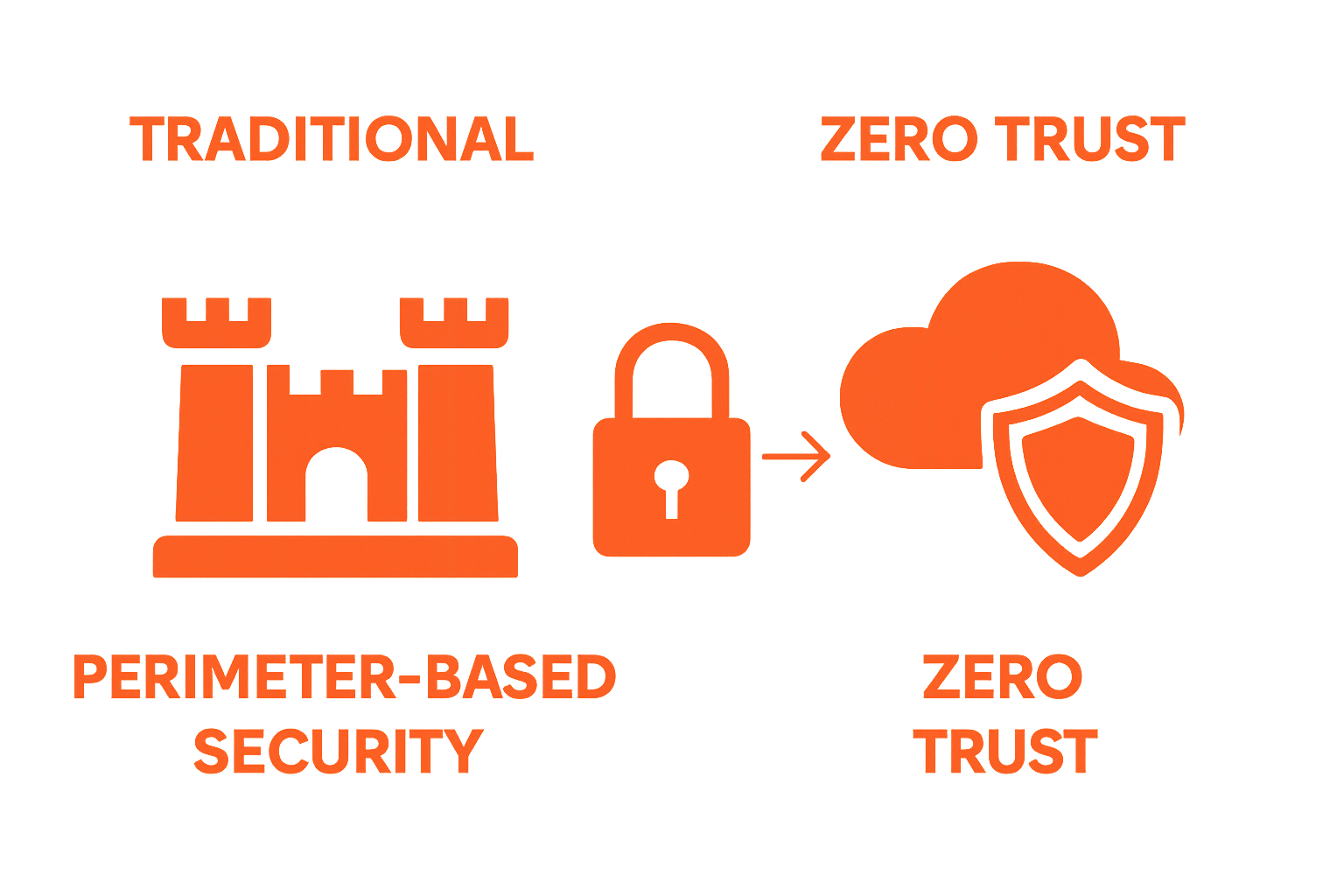 Zero trust architecture represents a fundamental shift, assuming no inherent trust within or outside organisational networks. Every access request is continuously verified, authenticated, and monitored, regardless of its origin. This approach significantly reduces potential attack surfaces and enhances overall security posture.
Zero trust architecture represents a fundamental shift, assuming no inherent trust within or outside organisational networks. Every access request is continuously verified, authenticated, and monitored, regardless of its origin. This approach significantly reduces potential attack surfaces and enhances overall security posture.
Critical zero trust principles involve:
- Strict identity verification
- Least privilege access controls
- Continuous monitoring and validation
- Micro-segmentation of network resources
- Dynamic risk-based authentication
Regulatory Compliance and Integrated Security Frameworks
Cloud security is increasingly intertwined with complex regulatory requirements. Organisations must develop comprehensive security strategies that not only protect digital assets but also ensure compliance with evolving data protection regulations. Integrated security frameworks that combine technological solutions with robust governance mechanisms will become standard practice.
The future of cloud security will demand holistic approaches that balance technological innovation, regulatory compliance, and organisational resilience. As cyber threats become more sophisticated, businesses must continuously adapt their security strategies to protect their most valuable digital assets.
Understanding Emerging Technologies in Cloud Security
Emerging technologies are rapidly transforming cloud security, offering unprecedented capabilities to protect digital infrastructure against sophisticated cyber threats. As organisations navigate increasingly complex technological landscapes, understanding these innovative solutions becomes crucial for maintaining robust digital defences.
Quantum Computing and Cryptographic Resilience
Quantum computing represents a paradigm shift in computational capabilities, presenting both revolutionary opportunities and significant security challenges**. While quantum technologies can potentially break traditional encryption methods, they simultaneously enable development of advanced cryptographic techniques**. Research from the University of Pretoria highlights the transformative potential of emerging technologies in financial and technological sectors.
Key quantum security implications include:
- Advanced encryption methodologies
- Enhanced threat detection capabilities
- Unprecedented computational processing
- Complex mathematical modelling
- Next generation cryptographic frameworks
Blockchain and Distributed Security Architectures
Blockchain technologies offer decentralised security models that fundamentally challenge traditional centralized protection strategies. By creating immutable, transparent transaction records, blockchain enables unprecedented levels of data integrity and authentication. These distributed architectures provide robust mechanisms for verifying and securing digital interactions across complex network environments.
Critical blockchain security characteristics involve:
- Decentralized trust mechanisms
- Transparent transaction tracking
- Immutable record keeping
- Reduced single point of failure risks
- Enhanced authentication protocols
Artificial Intelligence and Predictive Defence Mechanisms
Artificial intelligence continues to revolutionize cloud security by enabling dynamic, intelligent threat response systems. Machine learning algorithms can now analyse complex behavioural patterns, predict potential vulnerabilities, and autonomously respond to emerging security challenges. read more about emerging security technologies to understand how these innovations are reshaping digital defence strategies.
The convergence of these emerging technologies signals a profound transformation in cloud security paradigms. Organisations must remain agile, continuously adapting their technological frameworks to leverage these innovative protective mechanisms effectively.
Real-World Impacts of Enhanced Cloud Security Measures
Cloud security measures are no longer abstract technological concepts but critical mechanisms that directly influence organisational resilience, economic stability, and national infrastructure protection.
The following table summarises the benefits of enhanced cloud security measures in terms of both economic/operational resilience and national infrastructure protection, as outlined in the article.
| Impact Area | Benefits Provided |
|---|---|
| Economic & Operational | Prevents major financial losses, safeguards reputation, maintains operational continuity, protects information assets, sustains customer trust |
| National Infrastructure | Secures government digital systems, protects economic framework, reduces cyber warfare risks, safeguards citizen data, ensures digital sovereignty |
Economic and Operational Resilience
Enhanced cloud security measures directly contribute to organisational economic stability and operational continuity. By implementing comprehensive security frameworks, businesses can mitigate potentially catastrophic financial risks associated with data breaches and cyber incidents. Research from the University of Johannesburg highlights the critical importance of developing advanced cybersecurity capabilities.
Key economic protection benefits include:
- Prevention of substantial financial losses
- Maintenance of business reputation
- Continuous operational functionality
- Protection of intellectual property
- Preservation of customer trust
National Infrastructure and Strategic Security
Cloud security measures extend beyond individual organisational boundaries, playing a crucial role in protecting national digital infrastructure. Sophisticated security technologies serve as critical defence mechanisms against potential cyber threats that could compromise strategic economic and governmental systems. By implementing robust security protocols, nations can safeguard their critical digital ecosystems against increasingly complex cyber risks.
Strategic security implications encompass:
- Protection of government digital systems
- Preservation of national economic infrastructure
- Mitigation of potential cyber warfare risks
- Safeguarding sensitive citizen information
- Maintaining technological sovereignty
Digital Transformation and Competitive Advantage
Organisations with advanced cloud security capabilities gain significant competitive advantages in rapidly evolving digital markets. Robust security frameworks enable businesses to confidently embrace digital transformation, exploring innovative technologies without compromising their operational integrity. This approach transforms security from a defensive mechanism to a strategic enabler of technological innovation.
Cloud security has transcended its traditional role as a protective measure, emerging as a fundamental driver of organisational resilience, economic stability, and technological progress. As digital ecosystems become increasingly complex, comprehensive security strategies will become essential for sustainable business success.
Future-Proof Your Business Security with Trusted IT Leadership
The risks around cloud security highlighted in our article point to real threats facing South African firms today. With cyber attacks growing ever more advanced and the cost of a breach potentially crippling for your reputation and bottom line, you need more than good intentions. You need an IT partner who lives and breathes proactive protection, mastering the new essentials like zero trust architecture, continuous threat monitoring and AI-driven defence strategies.
If your business is ready to embrace emerging cloud technologies while keeping all vulnerabilities firmly under control, talk to a support team that understands both the innovation and the risks. Explore how Techtron’s proven managed IT services empower mid-sized engineering, financial and professional companies to secure their cloud, protect their assets and remain fully compliant. Do not leave your organisation’s future exposed. Connect with us now at Techtron to secure a safer digital tomorrow tailored to your operational needs.
Frequently Asked Questions
What is the current state of cloud security?
The current state of cloud security involves a complex ecosystem with advanced technologies such as AI, machine learning, and predictive analytics that are used to identify and mitigate potential security risks proactively.
Why is cloud security important for modern businesses?
Cloud security is crucial as it protects critical business assets, secures sensitive data, prevents financial losses from data breaches, and enhances overall operational resilience, making it fundamental for sustainable success.
How is artificial intelligence impacting cloud security?
Artificial intelligence impacts cloud security by enabling proactive threat detection, real-time monitoring, and automated incident response, significantly improving the ability to manage risks and vulnerabilities.
What are the key trends shaping the future of cloud security?
Key trends shaping the future of cloud security include the adoption of zero trust architecture, advancements in AI-driven security solutions, and the integration of regulatory compliance within security frameworks.