IT Infrastructure Overview 2025: Guide for Mid-Sized Businesses
IT infrastructure is turning into the backbone of every mid-sized business fighting to stay ahead. These days, businesses are migrating to flexible setups, but most don’t realise that AI-driven automation is set to transform almost 70% of business processes by 2025. So while everyone’s busy chasing the latest hardware or debating over cloud storage, the real edge goes to those who know how to combine smarter tech with adaptable strategies.
Table of Contents
- Core Components Of IT Infrastructure
- Modern IT Trends Shaping 2025
- Key Security And Compliance Essentials
- Choosing Between In-House And Outsourced IT
Quick Summary
| Takeaway | Explanation |
|---|---|
| Invest in AI for efficiency | Leverage AI to automate processes, enhancing operational efficiency and reducing human error. |
| Adopt hybrid cloud models | Use hybrid cloud systems for improved flexibility, security, and resource management across your IT operations. |
| Implement Zero Trust security | Shift to a Zero Trust model for security, continuously verifying all access attempts to mitigate risks. |
| Develop adaptive compliance strategies | Stay ahead of regulations by continuously monitoring and adapting compliance procedures for evolving standards. |
| Evaluate in-house vs outsourcing | Assess the balance of maintaining internal IT versus outsourcing for innovative solutions and cost savings. |
Core Components of IT Infrastructure
Building a robust IT infrastructure requires understanding its fundamental components that work together to support business operations and technological capabilities. Modern organizations rely on a complex ecosystem of hardware, software, and network technologies to maintain competitive advantage and operational efficiency.
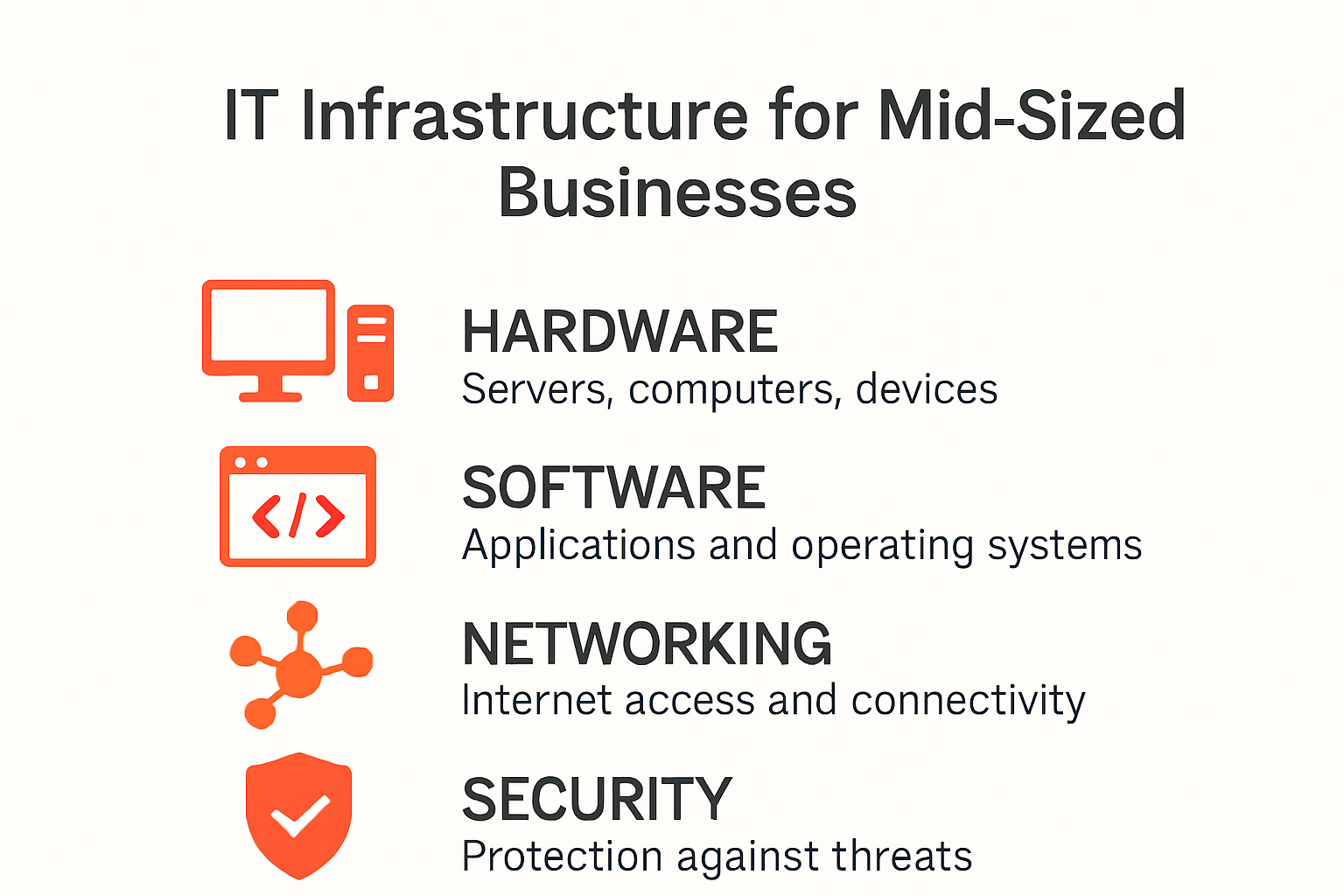
Hardware Infrastructure
The physical foundation of IT infrastructure starts with critical hardware components that form the backbone of technological capabilities. Servers represent the core processing units that handle computational tasks, data storage, and application hosting. According to IEEE Computer Society, enterprise-grade servers now support increasingly sophisticated workloads with advanced processing capabilities.
Servers are complemented by network equipment like routers, switches, and firewalls that enable seamless communication and secure data transmission. Research from MIT Technology Review indicates that mid-sized businesses are investing heavily in modular network infrastructure that can scale dynamically with organizational growth.
Software and Networking Components
Software infrastructure represents the digital layer that enables businesses to run applications, manage data, and support critical operational processes. Operating systems, middleware, and enterprise applications form the software ecosystem that connects different technological components. Virtual infrastructure technologies like containerization and cloud platforms have revolutionized how businesses deploy and manage their IT resources.
Networking components extend beyond physical hardware, encompassing complex systems that facilitate data transmission, communication protocols, and security mechanisms. Virtualization technologies now allow businesses to create flexible, software-defined networks that can adapt quickly to changing technological requirements. These technologies provide enhanced scalability, reducing infrastructure costs and improving operational responsiveness.
Security and Management Infrastructure
Cybersecurity infrastructure has become a critical component of modern IT systems. Businesses must implement comprehensive security frameworks that protect against evolving digital threats. This includes intrusion detection systems, encryption technologies, access management platforms, and continuous monitoring tools.
Management infrastructure involves tools and processes that enable organizations to monitor, maintain, and optimize their technological resources. Configuration management systems help businesses track hardware and software assets, manage updates, and ensure consistent performance across complex IT environments. These systems provide real-time insights into infrastructure health, enabling proactive maintenance and strategic technology planning.
By understanding and strategically implementing these core IT infrastructure components, mid-sized businesses can build resilient, scalable technological ecosystems that support growth and innovation. The key lies in creating an integrated approach that balances hardware capabilities, software flexibility, and robust security mechanisms.
Below, the table summarises the core components of modern IT infrastructure mentioned above and the primary functions they serve within an organisation:
| Component | Key Functions |
|---|---|
| Hardware (Servers, Network Gear) | Processing tasks, data storage, enabling communications, and application hosting |
| Software (OS, Middleware, Apps) | Running business applications, data management, operational process support |
| Networking (Physical & Virtual) | Data transmission, connection of systems, implementing communication protocols |
| Security Infrastructure | Intrusion detection, encryption, access management, proactive monitoring |
| Management Tools (Config Systems) | Asset tracking, system updates, performance monitoring, maintaining infrastructure health |
Modern IT Trends Shaping 2025
The technological landscape is rapidly evolving, presenting mid-sized businesses with unprecedented opportunities and challenges in IT infrastructure development. As we approach 2025, several transformative trends are reshaping how organizations approach technology strategy and implementation.
Artificial Intelligence and Automation
Artificial Intelligence (AI) is no longer a futuristic concept but a practical tool for businesses seeking operational efficiency. According to Gartner Research, AI-driven automation is expected to transform nearly 70% of business processes by 2025. Machine learning algorithms are now capable of predictive maintenance, intelligent resource allocation, and advanced cybersecurity threat detection.
Businesses are increasingly leveraging AI to optimize complex IT infrastructure management. Intelligent automation enables real-time monitoring, automatic system updates, and proactive problem resolution. These technologies reduce human error, minimize downtime, and create more resilient technological ecosystems.

Cloud and Hybrid Infrastructure Models
Cloud computing continues to revolutionize IT infrastructure, offering unprecedented flexibility and scalability. According to the U.S. Government Accountability Office, hybrid cloud environments are becoming the standard for mid-sized businesses seeking balanced technological approaches. These models combine public cloud services with private infrastructure, providing organizations with enhanced security and customization options.
Hybrid infrastructure allows businesses to distribute workloads strategically, balancing performance, cost, and compliance requirements. Multi-cloud strategies are emerging as a sophisticated approach, enabling companies to leverage different cloud providers’ strengths while maintaining operational redundancy.
Zero Trust Security Architecture
Cybersecurity is undergoing a fundamental transformation with the adoption of Zero Trust security models. Traditional perimeter-based security approaches are becoming obsolete as remote work and distributed systems become more prevalent. Zero Trust principles assume no inherent trust, requiring continuous verification for every user, device, and network connection.
Implementing Zero Trust architecture involves comprehensive identity management, microsegmentation, and continuous authentication mechanisms. This approach significantly reduces potential security vulnerabilities by treating every access attempt as potentially suspicious, regardless of its origin. Mid-sized businesses can enhance their security posture by adopting these advanced protective strategies.
These emerging trends demonstrate that IT infrastructure is becoming more intelligent, flexible, and secure. Successful organizations will be those that can adapt quickly, integrate advanced technologies strategically, and maintain a forward-looking technological perspective. The future of IT infrastructure is not about replacing existing systems but about creating more responsive, intelligent, and resilient technological ecosystems.
Key Security and Compliance Essentials
In the rapidly evolving digital ecosystem, security and compliance have become critical priorities for mid-sized businesses. Protecting sensitive data, maintaining regulatory standards, and defending against sophisticated cyber threats require a comprehensive and strategic approach to IT infrastructure management.
Regulatory Compliance Frameworks
Navigating the complex landscape of regulatory requirements demands a proactive and structured approach. According to National Institute of Standards and Technology, organizations must implement robust frameworks that address multiple dimensions of data protection and operational standards. Different industries have specific compliance mandates that businesses must carefully address.
Key regulatory frameworks such as GDPR, HIPAA, and PCI DSS establish minimum security standards that organizations must meet. Compliance management involves continuous monitoring, documentation, and implementation of specific security protocols. These frameworks are not static but evolve with emerging technological and threat landscapes, requiring businesses to maintain adaptive compliance strategies.
The following table summarises key regulatory compliance frameworks and their primary focus as highlighted in this section:
| Framework | Industry/Application | Main Focus |
|---|---|---|
| GDPR | General (EU data protection) | Data privacy, personal data rights |
| HIPAA | Healthcare (mainly USA) | Patient health information security |
| PCI DSS | Payment processing/financial | Credit card data protection |
Comprehensive Cybersecurity Strategies
Cybersecurity has transitioned from a technical consideration to a critical business imperative. Cybersecurity Ventures reports that global cybercrime damages are projected to reach astronomical figures, underscoring the urgent need for robust defensive mechanisms. Mid-sized businesses must develop multi-layered security approaches that go beyond traditional perimeter defenses.
A comprehensive cybersecurity strategy encompasses several critical elements. Threat detection systems utilize advanced machine learning algorithms to identify and neutralize potential security breaches in real-time. Endpoint protection, network segmentation, and continuous vulnerability assessments form integral components of a holistic security infrastructure. Employee training and awareness programs are equally crucial, as human factors remain a significant vulnerability in cybersecurity.
Data Protection and Privacy Measures
Protecting sensitive organizational and customer data requires sophisticated encryption technologies and rigorous access management protocols. Encryption at rest and in transit ensures that even if data is intercepted, it remains unreadable to unauthorized parties. Implementing strong authentication mechanisms, such as multi-factor authentication and biometric verification, adds additional layers of security.
Privacy considerations extend beyond technical implementations. Organizations must develop clear data governance policies that outline how information is collected, stored, processed, and protected. This includes creating transparent data handling procedures, maintaining detailed audit trails, and establishing clear protocols for data retention and deletion.
Security and compliance are not destination points but continuous journeys of adaptation and improvement. Successful organizations recognize that robust IT infrastructure security requires ongoing investment, continuous learning, and a proactive approach to emerging technological challenges. By integrating comprehensive security strategies, maintaining regulatory compliance, and fostering a culture of digital resilience, mid-sized businesses can effectively protect their most valuable digital assets.
Choosing Between In-House and Outsourced IT
Mid-sized businesses face a critical strategic decision when determining their IT infrastructure management approach. The choice between maintaining an in-house IT team or partnering with an outsourced IT service provider can significantly impact technological capabilities, operational efficiency, and overall business performance.
Cost and Resource Considerations
Financial implications play a crucial role in IT infrastructure strategy. According to Future Business Journal, organizations can achieve cost savings ranging from 10% to 50% through strategic IT outsourcing. In-house IT teams require substantial investments in recruitment, training, equipment, and continuous skill development.
Operational expenses extend beyond direct salary costs. Businesses must consider infrastructure investments, ongoing training, technology upgrades, and maintaining competitive compensation packages to retain top technological talent. Outsourced IT services offer a more predictable cost structure, allowing businesses to convert fixed technology expenses into scalable operational expenditures.
Strategic Expertise and Innovation
Modern IT outsourcing transcends traditional cost-reduction models. Research from Arxiv highlights that contemporary outsourcing strategies focus on leveraging external expertise to drive innovation and competitive advantage. Specialized IT service providers bring comprehensive knowledge across multiple technological domains, offering insights and capabilities that might be challenging for in-house teams to develop independently.
Outsourced IT partners provide access to cutting-edge technologies, advanced security frameworks, and industry best practices. They can rapidly adapt to emerging technological trends, ensuring businesses remain technologically agile. Technological flexibility becomes a key strategic asset, enabling organizations to scale resources dynamically based on evolving business requirements.
Hybrid IT Management Approaches
Recognizing the complexities of IT infrastructure management, many organizations are adopting hybrid models that blend in-house capabilities with external expertise. Systematic literature review research indicates that businesses increasingly explore backsourcing strategies to optimize control, quality, and technological capabilities.
Hybrid approaches allow businesses to maintain core technological competencies internally while leveraging specialized external resources for complex or rapidly evolving technological domains. This model provides a balanced strategy that combines the benefits of institutional knowledge with specialized external expertise. Organizations can strategically allocate technological responsibilities, ensuring optimal resource utilization and maintaining technological adaptability.
Choosing between in-house and outsourced IT is not a binary decision but a nuanced strategic consideration. Successful businesses will approach this choice by comprehensively evaluating their unique technological requirements, organizational culture, financial constraints, and long-term strategic objectives. The goal is not to select a universal solution but to develop a tailored IT management approach that aligns seamlessly with the organization’s specific needs and growth trajectory.
Frequently Asked Questions
What are the core components of IT infrastructure for mid-sized businesses?
The core components include hardware such as servers and network equipment, software for application management, and security infrastructure to protect against cyber threats. Effective integration of these elements is crucial for operational efficiency.
How will AI-driven automation impact business processes by 2025?
AI-driven automation is expected to transform nearly 70% of business processes by 2025, enhancing operational efficiency, reducing human error, and enabling real-time monitoring of IT systems, thus streamlining overall business functions.
What are hybrid cloud models, and why should mid-sized businesses adopt them?
Hybrid cloud models combine public and private cloud services, offering improved flexibility, security, and cost management. They allow businesses to strategically distribute workloads according to performance and compliance requirements.
What does Zero Trust security architecture mean for my business?
Zero Trust security architecture is a security model that requires continuous verification for every user and device trying to access network resources. This approach enhances security by treating every access attempt as potentially untrustworthy, regardless of its origin.
Ready for 2025? Secure and Transform Your IT Infrastructure Now
Your business should not let outdated technology or manual processes put your operations at risk. The article highlighted how AI-driven automation, Zero Trust security and hybrid cloud models are shaping the new age of IT for mid-sized firms. If you are worried about managing compliance, IT security or adapting quickly enough to outpace threats, you are not alone. Many South African engineering and financial businesses are wrestling with these exact challenges every day.

You deserve peace of mind with infrastructure and security designed for where your business is heading, not just where you are now. Take the first step and see how Techtron’s expert managed IT services can deliver:
- Automated, proactive support that keeps your tech one step ahead
- Enterprise-level cybersecurity including Zero Trust principles
- Cloud solutions purpose-built for teams of 80 to 300 staff
Let us help you cut complexity and cost while boosting your resilience. Visit our main page now to book a personalised consultation. Your future-ready IT starts today.