Privileged Access Management for Modern Businesses
Privileged access management might sound like just another layer of IT security, but the stakes are way higher than most think. One wrong move with a privileged account can cost a company millions, and insider threats account for over 60 percent of security incidents linked to privileged users. That seems scary enough, but the real surprise is that most businesses still overlook the simple steps that could close these massive gaps. Why are so many leaving the front door wide open while focusing on problems that matter far less?
Table of Contents
- Understanding Privileged Access Management Basics
- Key Risks And Challenges Facing Businesses
- Best Practices For Strong Access Control
- Choosing The Right Privileged Access Solution
Quick Summary
| Takeaway | Explanation |
|---|---|
| Implement least privilege access | Limit user permissions to only what is necessary for their roles, reducing potential risks significantly. |
| Utilize multi-factor authentication | Require multiple forms of verification to enhance security against unauthorized access attempts. |
| Conduct regular access reviews | Periodically audit permissions to ensure that access levels remain appropriate and necessary for users. |
| Adopt continuous monitoring practices | Track all activity involving privileged accounts to detect and respond to potential security incidents in real time. |
| Evaluate privileged access solutions carefully | Assess technology compatibility, security features, and operational needs before selecting management solutions to ensure effective protection. |
Understanding Privileged Access Management Basics
Privileged Access Management (PAM) represents a critical cybersecurity strategy that protects an organization’s most sensitive digital assets by controlling and monitoring access to critical systems and administrative accounts. At its core, PAM addresses the fundamental challenge of managing and securing accounts with elevated permissions that could potentially cause significant damage if compromised.
The Core Principles of Privileged Access Control
Privileged accounts represent a unique security challenge for modern businesses. These accounts typically belong to administrators, IT managers, and other key personnel who require extensive system access to perform their roles. According to the National Institute of Standards and Technology (NIST), privileged access management involves implementing robust security controls that govern how these high-level accounts are used and monitored.
The fundamental principles of PAM revolve around three key concepts: least privilege, access monitoring, and comprehensive authentication. Least privilege ensures that users are granted only the minimum level of access necessary to complete their specific job functions. This approach dramatically reduces the potential attack surface and minimizes the risk of unauthorized system modifications.
Risk Mitigation and Security Strategies
NIST Special Publication 800-171 provides comprehensive guidance on managing privileged accounts, emphasizing the importance of strict access controls. Organizations must implement multi-layered security strategies that include:
- Account Restriction: Limiting the number of privileged accounts and carefully defining their scope
- Continuous Monitoring: Tracking and recording all activities performed using privileged credentials
- Regular Access Reviews: Periodically auditing and validating the necessity of existing privileged access permissions
The critical nature of PAM becomes evident when considering the potential consequences of unauthorized access. A single compromised administrative account can provide cybercriminals with complete control over an organization’s IT infrastructure, potentially leading to data breaches, system disruptions, and significant financial losses.
Modern privileged access management goes beyond simple password protection. It involves sophisticated approaches that include real-time monitoring, automatic session recording, and advanced authentication mechanisms. These strategies ensure that even if credentials are somehow obtained, unauthorized users cannot easily exploit privileged accounts.
Businesses must recognize that privileged access management is not a one-time implementation but an ongoing process. As organizational structures change, technology evolves, and new security threats emerge, PAM strategies must remain dynamic and adaptive. This requires continuous assessment, updating of access protocols, and investment in advanced security technologies that can provide comprehensive protection against increasingly sophisticated cyber threats.
By adopting a comprehensive privileged access management approach, organizations can significantly reduce their cybersecurity risks, protect sensitive information, and maintain the integrity of their critical digital infrastructure.
Key Risks and Challenges Facing Businesses
Businesses today face increasingly complex cybersecurity challenges that require sophisticated privileged access management strategies. Understanding these risks is crucial for developing robust security frameworks that protect sensitive organizational assets and maintain operational integrity.
Insider Threats and Account Vulnerabilities
Research from ISACA reveals that insider threats represent a significant risk for organizations. Privileged accounts belonging to IT administrators and power users can become potential entry points for malicious activities. These accounts often have extensive system access, making them prime targets for both intentional and unintentional security breaches.
The complexity of modern IT environments introduces multiple vulnerabilities. Cloud services, remote work technologies, and increasingly distributed systems create additional challenges in managing and securing privileged access. Employees with elevated permissions might inadvertently expose critical systems through poor security practices, while malicious insiders could deliberately exploit their access rights.
Complex Authentication and Identity Management Challenges
A comprehensive study analyzing cybersecurity professionals’ insights identified several critical challenges in identity and access management. Organizations struggle with multiple complex issues, including:
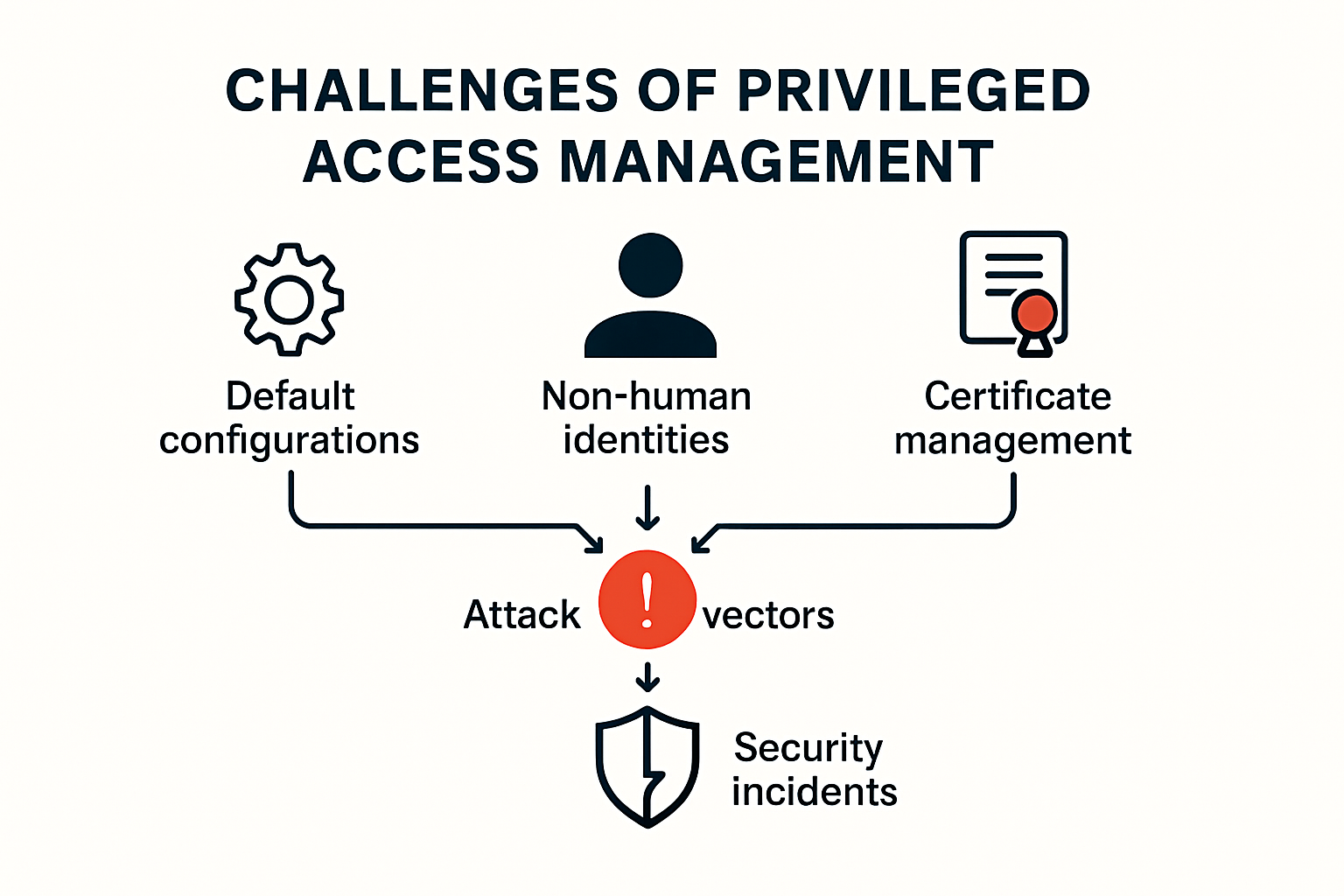
To provide clearer insight into common challenges with authentication and identity management in privileged access environments, the following table summarises key issues highlighted in the article.
| Challenge | Description |
|---|---|
| Default Configuration Vulnerabilities | Insecure default system settings expose organisations to risk |
| Non-human Identity Management | Difficulty in tracking and controlling service accounts |
| Certificate Management Weaknesses | Inadequate tracking and rotation of authentication credentials |
| API Security Limitations | Poor configuration of application programming interfaces |
- Default Configuration Vulnerabilities: Many systems come with insecure default settings
- Non-human Identity Management: Difficulties in tracking and controlling service accounts
- Certificate Management Weaknesses: Inadequate tracking and rotation of authentication credentials
- API Security Limitations: Poor configuration of application programming interfaces
According to the National Institute of Standards and Technology (NIST), privileged accounts are prime targets for malicious actors. These accounts can potentially provide complete system access, enabling data theft, espionage, and infrastructure sabotage if compromised.
The rapid digital transformation across industries has exponentially increased the complexity of access management. Organizations must now protect against sophisticated threats that can emerge from multiple vectors – external hackers, insider threats, and systemic vulnerabilities. Traditional security models that rely solely on perimeter defense are no longer sufficient.
Moreover, regulatory requirements continue to evolve, placing additional pressure on businesses to implement comprehensive privileged access management solutions. Compliance is no longer just about meeting minimum standards but about creating resilient, adaptive security frameworks that can respond to emerging threats in real-time.
Businesses must adopt a proactive approach to privileged access management. This involves continuous monitoring, regular access reviews, implementing multi-factor authentication, and creating clear, enforceable policies that limit unnecessary privileges. The goal is not just prevention but creating a dynamic security ecosystem that can quickly detect, respond to, and mitigate potential security incidents.
The financial and reputational risks of failing to address these challenges are substantial. A single compromised privileged account can lead to devastating consequences, including significant financial losses, regulatory penalties, and irreparable damage to organizational reputation and customer trust.
Best Practices for Strong Access Control
Implementing robust access control mechanisms represents a critical strategy for protecting organizational digital assets and mitigating potential security vulnerabilities. Effective access control goes beyond simple password protection, requiring a comprehensive and strategic approach to managing user permissions and system interactions.
Implementing Least Privilege Principles
According to NIST Special Publication 800-171, organizations must develop rigorous access control strategies that limit user permissions to the absolute minimum required for performing specific job functions. The least privilege principle ensures that employees and systems have only the precise level of access necessary to complete their designated tasks, dramatically reducing potential attack surfaces.
Key implementation strategies for least privilege include:
- Role-Based Access Control: Designing permission sets that align precisely with job responsibilities
- Granular Permission Mapping: Creating detailed access profiles for different organizational roles
- Regular Permission Audits: Continuously reviewing and adjusting user access rights
Multi-Factor Authentication and Advanced Verification
Modern access control strategies demand sophisticated authentication mechanisms that extend far beyond traditional username and password combinations. Multi-factor authentication represents a critical defense mechanism, requiring users to provide multiple verification credentials before gaining system access.
Effective multi-factor authentication typically incorporates:
- Biometric Verification: Utilizing fingerprint, facial recognition, or retinal scan technologies
- Hardware Tokens: Requiring physical security devices for additional authentication
- Contextual Access Evaluation: Analyzing login attempts based on location, device, and historical usage patterns
Organizations must develop adaptive authentication frameworks that can dynamically assess risk and adjust verification requirements in real-time. This approach allows for more nuanced access control that can respond to changing threat landscapes and individual user behaviors.
The complexity of modern technological environments demands a holistic approach to access control. This involves not just technological solutions but also comprehensive policy development, continuous employee training, and proactive security monitoring. Companies must create a culture of security awareness where every team member understands their role in maintaining robust access management protocols.
Implementing strong access control is not a one-time event but an ongoing process of assessment, refinement, and adaptation. As technological landscapes evolve and new security threats emerge, organizations must remain vigilant and responsive, continuously updating their access management strategies to address emerging challenges.
Successful access control requires a balanced approach that maintains stringent security standards while preserving operational efficiency. By developing sophisticated, intelligent access management frameworks, businesses can protect their critical digital infrastructure without unnecessarily hindering productivity or creating excessive friction in daily operational processes.
Ultimately, strong access control is about creating a resilient, adaptive security ecosystem that can dynamically respond to potential threats while enabling authorized users to perform their essential functions with minimal disruption.
Choosing the Right Privileged Access Solution
Selecting an appropriate privileged access management solution requires a strategic approach that goes beyond basic security features. Organizations must carefully evaluate their unique technological landscape, security requirements, and operational constraints to identify a solution that provides comprehensive protection and seamless integration.
Evaluating Solution Capabilities and Compatibility
The National Cybersecurity Center of Excellence (NCCoE) emphasizes the importance of selecting a privileged access management solution that can effectively monitor, audit, and control critical system access. Businesses must look beyond surface-level features and consider solutions that offer comprehensive security capabilities aligned with their specific organizational needs.
Key evaluation criteria should include:
When selecting a privileged access management solution, it is crucial to compare features and capabilities for optimal fit. The table below provides a concise comparison of key evaluation criteria discussed in this article.
| Evaluation Criteria | Importance | Example Capability |
|---|---|---|
| Comprehensive Monitoring | High | Real-time tracking of account actions |
| Advanced Authentication | Essential | Multi-factor verification mechanisms |
| Detailed Auditing | Critical | Logging and reporting privileged access |
| Scalability | Important for growth | Adapts to changing infrastructure |
| Dynamic Risk Assessment | Supports Zero Trust approach | Context-based evaluation of requests |
- Comprehensive Monitoring: Real-time tracking of privileged account activities
- Advanced Authentication: Multi-factor verification mechanisms
- Detailed Auditing: Comprehensive logging and reporting capabilities
- Scalability: Ability to adapt to organizational growth and changing infrastructure
Zero Trust and Context-Based Access Control
According to the Cybersecurity and Infrastructure Security Agency (CISA), modern privileged access solutions should incorporate context-based access control (CBAC) principles. This approach goes beyond traditional static permission models, dynamically evaluating access requests based on multiple contextual factors such as user identity, device attributes, and environmental conditions.
Effective solutions should provide:
- Dynamic Risk Assessment: Continuous evaluation of access requests
- Granular Permission Management: Precise control over user access levels
- Adaptive Authentication: Flexible verification mechanisms that respond to changing risk scenarios
NIST’s Interagency Report 7657 highlights the critical importance of implementing robust privilege management strategies that extend beyond traditional security approaches. Organizations must seek solutions that offer not just technological protection but also comprehensive governance frameworks.
The selection process should involve a thorough assessment of existing technological infrastructure, potential integration challenges, and long-term security objectives. This requires collaboration between IT security teams, operational managers, and senior leadership to ensure the chosen solution meets both immediate and strategic organizational needs.
Businesses must also consider the total cost of ownership, including implementation complexity, ongoing maintenance requirements, and potential performance impacts. A solution that appears cost-effective initially might introduce significant operational inefficiencies or require extensive customization.
Training and organizational readiness represent additional critical considerations. The most advanced privileged access management solution will prove ineffective without proper implementation, employee training, and a culture of security awareness. Organizations must invest in comprehensive training programs that help employees understand the importance of privileged access management and their role in maintaining security protocols.
Ultimately, choosing the right privileged access solution is about finding a balance between robust security capabilities, operational efficiency, and organizational adaptability. It requires a holistic approach that considers technological, human, and strategic factors to create a comprehensive security ecosystem that can effectively protect critical digital assets.

Frequently Asked Questions
What is Privileged Access Management (PAM)?
Privileged Access Management (PAM) is a cybersecurity strategy that controls and monitors access to critical systems and administrative accounts, protecting an organization’s sensitive digital assets from unauthorized access and potential breaches.
Why is implementing least privilege access important?
Implementing least privilege access is crucial because it limits user permissions to only what is necessary for their specific job functions, significantly reducing the attack surface and minimizing the risks of unauthorized system modifications.
How can multi-factor authentication enhance security in PAM?
Multi-factor authentication enhances security by requiring users to provide multiple forms of verification before gaining access to privileged accounts, making it more difficult for unauthorized individuals to exploit access even if they obtain a password.
What are some best practices for strong access control in organizations?
Best practices for strong access control include implementing least privilege principles, conducting regular access reviews, utilizing multi-factor authentication, adopting continuous monitoring, and evaluating privileged access solutions carefully to ensure comprehensive security and compliance.
Take Control of Privileged Access with Trusted Business IT Support
Are you struggling to manage privileged access and worried about insider threats or costly security gaps? The article highlights that many South African firms still expose themselves to risk by overlooking least privilege principles, multi-factor authentication, and ongoing monitoring. It is often one overlooked privileged account or improper access review that exposes your whole business to real dangers like data breaches, compliance penalties, or reputational damage. This level of IT risk is especially pronounced for professional service firms and mid-sized organisations juggling complex networks and evolving technology.
With Techtron, you gain a managed IT partner deeply experienced in proactive privileged access management, continuous monitoring, and full-stack security solutions. We help you eliminate unnecessary exposures, build strict access policies, and streamline verification, so your people only access what they need and your business is always compliant. Take the next step for peace of mind. Discover how our cybersecurity services can help you strengthen privileged access controls and support your IT goals. Visit https://techtron.co.za today to speak with specialists who understand the unique risks facing your business and are ready to build your secure future now.