
What Is a Firewall? Complete Guide for Businesses
Nearly 60 percent of organizations experience attempted cyber attacks every single week, making digital security a top concern for businesses of all sizes. With sensitive data constantly at risk, firewalls act as the first line of defense against network intrusions. Understanding how firewalls work, what sets each type apart, and why strong configuration matters helps companies protect their critical information in a rapidly changing threat landscape.
Key Takeaways
| Point | Details |
|---|---|
| Essential Role of Firewalls | Firewalls are critical for protecting networks from unauthorized access and cyber threats by controlling traffic based on security rules. |
| Types of Firewalls | Various types of firewalls, including next-generation and application layer firewalls, provide distinct security mechanisms and should be combined for robust protection. |
| Best Practices for Management | Effective firewall management includes regular audits, adhering to the principle of least privilege, and maintaining continuous monitoring to enhance security. |
| Limitations and Risks | Overreliance on perimeter defenses can create vulnerabilities; a defense-in-depth strategy utilizing multiple firewalls is necessary for comprehensive security. |
Firewall Definition and Core Concepts
Firewalls represent a critical security infrastructure designed to protect businesses from unauthorized network intrusions and potential cyber threats. According to SANS Institute, information security fundamentally involves protecting all forms of data, with firewalls serving as a key component in safeguarding digital information by controlling network traffic.
At its core, a firewall acts as a digital security barrier between trusted internal networks and potentially dangerous external networks like the internet.
As defined by DHET, firewalls are specialized security devices that monitor and control network traffic based on predetermined security rules, establishing a protective boundary that filters incoming and outgoing digital communication.
Firewalls operate through several sophisticated mechanisms:
- Packet Filtering: Examines data packets against predetermined security rules
- Stateful Inspection: Tracks active network connections and validates data packets
- Application Layer Filtering: Evaluates network traffic at the application protocol level
By implementing robust firewall strategies, businesses can achieve comprehensive network protection, preventing unauthorized access, blocking potential malware, and maintaining the integrity of their digital infrastructure. Understanding Network Security Fundamentals provides additional insights into developing a comprehensive cybersecurity approach that extends beyond basic firewall implementation.
Types of Firewalls and Key Differences
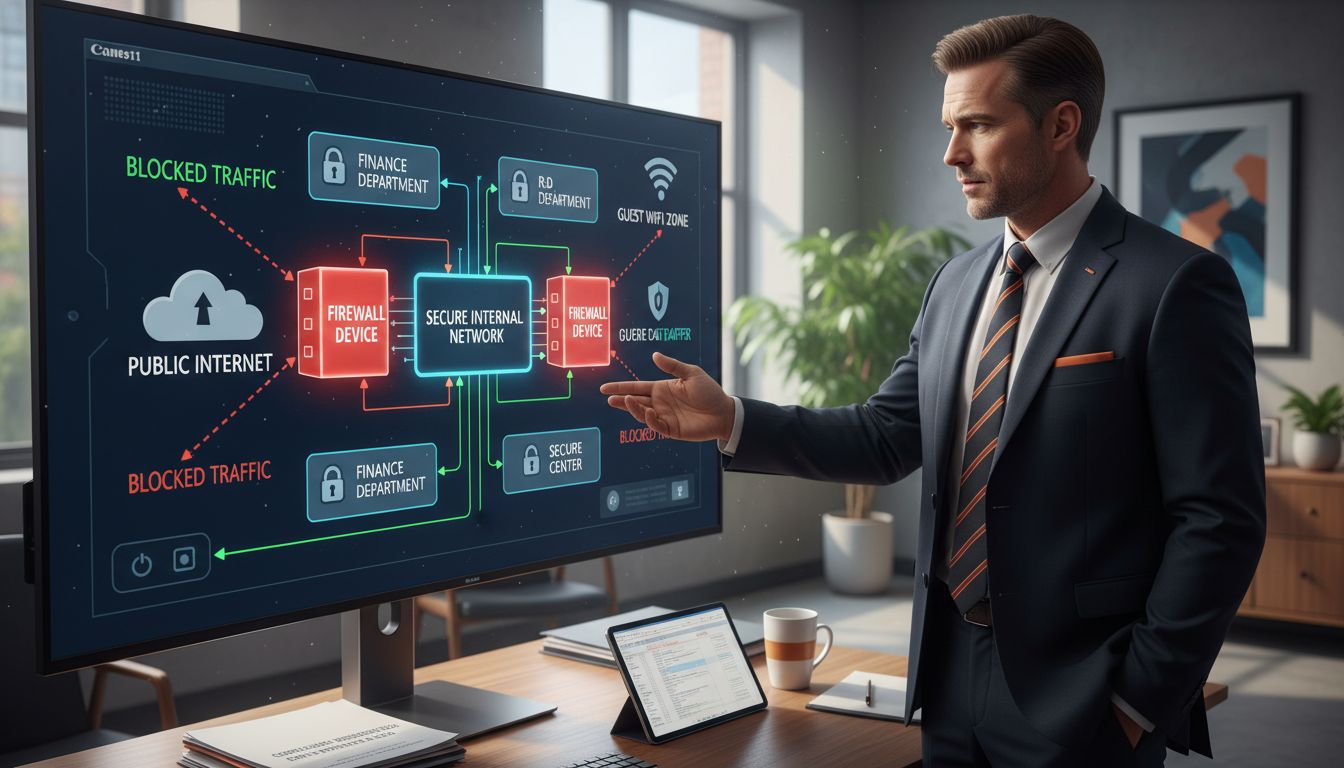
Firewall technologies have evolved significantly, offering businesses multiple layers of network protection. According to DHET, firewalls can be categorized into several distinct types, each operating at different layers of the OSI model and providing unique security mechanisms.
Network Layer Firewalls represent the most basic type of firewall, filtering traffic based on source and destination IP addresses, ports, and protocols. These firewalls operate at the network level, creating fundamental barriers against unauthorized access. Transport Layer Firewalls add an additional level of security by examining connection states and tracking active network sessions, enabling more granular traffic control.
More advanced firewall types include:
- Application Layer Firewalls: Inspect traffic at the application protocol level
- Context-Aware Firewalls: Analyze traffic context and user behavior patterns
- Next-Generation Firewalls: Combine multiple filtering techniques with advanced threat detection
As SANS Institute recommends, implementing multiple firewalls within a network can significantly enhance security through a defense-in-depth strategy. By strategically segmenting network zones and employing different firewall types, businesses can create robust, multi-layered protection against sophisticated cyber threats.

 For more comprehensive insights, 8 Types Of Network Security You Should Know provides an in-depth exploration of advanced network security approaches.
For more comprehensive insights, 8 Types Of Network Security You Should Know provides an in-depth exploration of advanced network security approaches.
How Firewalls Work in Business Networks
Firewalls serve as critical guardians of business network infrastructure, creating strategic barriers that control and monitor digital communication. According to SANS Institute, firewalls are strategically deployed across network enforcement boundaries to monitor and restrict traffic, ensuring only authorized communications occur between different network segments.
Network Traffic Inspection forms the core mechanism of firewall operations. These sophisticated systems continuously analyze incoming and outgoing data packets, comparing them against predefined security rules and configurations. By examining multiple parameters such as source IP addresses, destination ports, protocol types, and packet contents, firewalls can make real-time decisions about whether to allow or block specific network communications.
Key operational strategies for firewall management include:
- Rule Configuration: Establishing precise access control parameters
- Traffic Segmentation: Dividing network into secure zones
- Continuous Monitoring: Tracking and logging network interactions
- Threat Detection: Identifying potential security breaches
As SANS Institute emphasizes, effective firewall management requires implementing robust change control processes. This means systematically reviewing and approving any configuration modifications to maintain network integrity and security. For businesses seeking deeper insights, How to Keep Your Company’s Network Secure offers comprehensive strategies for comprehensive network protection.
Firewall Benefits and Real-World Use Cases
Firewalls are essential security tools that provide critical protection across various business environments and industries. According to SANS Institute, deploying internal firewalls creates a robust defense-in-depth strategy by segmenting networks and effectively controlling traffic between different organizational segments, thereby mitigating potential security threats.
Practical use cases demonstrate the versatility of firewall technologies across different sectors. In industrial control systems, firewalls play a pivotal role in protecting sensitive infrastructure. As SANS Institute highlights, these systems control network communication into and out of critical networks, blocking unauthorized access and ensuring operational security for complex technological ecosystems.
Key benefits of firewall implementation include:
- Data Protection: Preventing unauthorized data access
- Network Segmentation: Creating secure digital boundaries
- Threat Mitigation: Blocking potential cyber attacks
- Compliance Support: Meeting regulatory security requirements
- Performance Optimization: Managing network traffic efficiently
Businesses across various domains leverage firewall technologies to safeguard their digital assets. From financial institutions protecting sensitive transaction data to engineering firms securing intellectual property, firewalls represent a crucial line of defense. For deeper insights into maintaining robust network security, Network Security: Everything You Need to Know provides comprehensive strategies for modern organizations.
Risks, Limitations, and Best Practices
Firewall technologies, while essential, are not infallible security solutions. According to SANS Institute, improper firewall management can introduce significant risks, highlighting the critical importance of implementing structured change control processes that systematically review and approve all network configuration modifications.
One of the most significant limitations is the false sense of security that can emerge from overreliance on perimeter defenses. As SANS Institute emphasizes, depending solely on perimeter firewalls is insufficient for comprehensive network protection. Businesses must adopt a defense-in-depth strategy that involves deploying multiple firewalls across different network segments to effectively mitigate potential threats.
Key best practices for firewall management include:
- Regular Configuration Audits: Consistently reviewing and updating firewall rules
- Principle of Least Privilege: Restricting network access to only essential requirements
- Continuous Monitoring: Tracking network traffic and potential anomalies
- Timely Patch Management: Keeping firewall software updated
- Comprehensive Logging: Maintaining detailed records of network interactions
For businesses seeking to strengthen their cybersecurity posture, a proactive approach is crucial. By understanding potential vulnerabilities and implementing robust management strategies, organizations can significantly enhance their network protection. Understanding the IT Risk Assessment Process offers deeper insights into developing comprehensive security frameworks that go beyond traditional firewall implementations.
Strengthen Your Network Security with Expert Firewall Management
Understanding firewalls is crucial because they form the first line of defence against cyber threats that can disrupt your business operations. The article highlights common challenges like managing firewall rules, preventing unauthorized access, and implementing a defence-in-depth strategy to protect sensitive data. If you feel overwhelmed by the complexity of firewall configurations or worry about gaps in your network security, you are not alone.
At Techtron we specialise in tailored IT solutions that go beyond just installing firewalls. Our comprehensive network security services include ongoing monitoring, precise rule configuration, and strategic segmentation to keep your business protected and compliant. With expertise in managing these crucial barriers, we reduce your risk and ease your technical burden so you can focus on what matters most.
Ready to take the next step towards robust cybersecurity? Discover how our fully managed IT services combine proactive firewall management with expert support to safeguard your business today. Don’t wait for a breach to happen – visit Techtron now and secure your digital future with confidence.
Frequently Asked Questions
What is a firewall and how does it work?
Firewalls are security devices that protect networks by monitoring and controlling incoming and outgoing traffic based on pre-established security rules. They create a barrier between trusted internal networks and potential external threats, filtering communications to prevent unauthorized access.
What are the different types of firewalls?
Firewalls can be categorized into several types, including Network Layer Firewalls, Transport Layer Firewalls, Application Layer Firewalls, Context-Aware Firewalls, and Next-Generation Firewalls. Each type operates at different layers of the OSI model and offers specific security features.
How can businesses effectively manage their firewalls?
Effective firewall management involves several strategies, including regular configuration audits, implementing the principle of least privilege for access, continuous traffic monitoring, timely updates and patch management, and maintaining comprehensive log records of network interactions.
What are the main benefits of using firewalls in a business environment?
Firewalls provide essential benefits such as data protection from unauthorized access, network segmentation for secure boundaries, threat mitigation against cyber attacks, compliance support for regulatory requirements, and performance optimization for efficient network traffic management.