
Understanding What is SaaS Security: Key Concepts Explained
Businesses across South Africa are moving more of their operations to the cloud, relying on SaaS tools to keep everything running. It all sounds convenient right? But cyber criminals are not taking a break. Research shows that cybercriminals continually develop more sophisticated methods to slip past the defences of these cloud platforms. What most people miss is that password protection is just the tip of the iceberg and real SaaS security means building a multi-layered shield that adapts as quickly as the threats do.
Table of Contents
- Defining SaaS Security: What It Is And Its Importance
- The Role Of Data Protection In SaaS Security
- Understanding Threats To SaaS Applications
- Key Concepts And Strategies In SaaS Security
- Real-World Implications Of Strong SaaS Security
Quick Summary
| Takeaway | Explanation |
|---|---|
| SaaS security is essential for cloud applications | Protects sensitive data and mitigates risks associated with unauthorized access and cyber threats. |
| Data protection underpins SaaS security | Encompasses strategies like encryption, access controls, and continuous monitoring to safeguard information. |
| Adopt a multi-layered security architecture | Integrates various protective measures to defend against diverse cyber threats effectively. |
| Drive compliance and risk management | Align security strategies with legal standards and proactively address vulnerabilities to enhance operational integrity. |
| Strong security enhances business reputation | Protects against financial losses and builds customer trust, supporting successful digital transformation initiatives. |
Defining SaaS Security: What It Is and Its Importance
SaaS security represents a comprehensive approach to protecting cloud-based software applications and the sensitive data they manage. Unlike traditional software security models, SaaS security focuses on safeguarding applications delivered over the internet, addressing unique challenges presented by cloud computing environments.
Understanding the Core Concept
At its fundamental level, SaaS security involves implementing robust protective measures to secure software applications hosted and delivered through cloud platforms. These security strategies protect against unauthorized access, data breaches, and potential cyber threats that could compromise an organization’s digital infrastructure.
Key aspects of SaaS security include:
- Protecting user authentication mechanisms
- Encrypting data during transmission and storage
- Managing access controls and user permissions
- Monitoring and detecting potential security incidents
- Ensuring compliance with industry regulations
Importance for Modern Businesses
According to research from the University of Pretoria, cloud computing adoption requires comprehensive security strategies. For businesses leveraging cloud-based applications, robust SaaS security is not optional but essential. It helps organizations mitigate risks, protect sensitive information, and maintain operational continuity.
Businesses must recognize that SaaS security extends beyond simple password protection. It encompasses a holistic approach to digital risk management, integrating multiple layers of security controls to create a resilient defense mechanism against evolving cyber threats. By prioritizing SaaS security, organizations can confidently embrace digital transformation while minimizing potential vulnerabilities in their technology ecosystems.
The Role of Data Protection in SaaS Security
Data protection is the critical foundation of effective SaaS security, serving as a comprehensive shield that safeguards an organization’s most valuable digital assets. As cloud-based applications become increasingly central to business operations, understanding and implementing robust data protection strategies has become paramount.
Fundamental Data Protection Principles
Data protection in SaaS security encompasses a multi-layered approach to preventing unauthorized access, maintaining data integrity, and ensuring confidentiality. This involves implementing sophisticated mechanisms that go beyond traditional security measures.
Key data protection principles include:
- Encrypting sensitive information at rest and in transit
- Implementing robust authentication and authorization protocols
- Creating granular access control frameworks
- Establishing comprehensive data backup and recovery systems
- Continuously monitoring and auditing data access patterns
Strategic Compliance and Risk Management
According to South Africa’s National Data and Cloud Policy, data protection is not just a technical requirement but a strategic imperative. Organizations must develop comprehensive data protection strategies that align with legal requirements, industry standards, and emerging cybersecurity threats.
Effective data protection in SaaS security requires a proactive approach that anticipates potential vulnerabilities. This means continuously updating security protocols, conducting regular risk assessments, and maintaining a dynamic defense mechanism against evolving cyber threats. By prioritizing data protection, businesses can create a resilient security environment that safeguards critical information and maintains operational integrity.
Understanding Threats to SaaS Applications
SaaS applications represent critical digital infrastructure that faces an increasingly complex landscape of cybersecurity threats. These cloud-based platforms are continuously targeted by sophisticated attackers seeking to exploit vulnerabilities and compromise sensitive organizational data.
Types of Cybersecurity Threats
Modern SaaS applications encounter a diverse range of security challenges that can potentially compromise entire organizational networks. These threats are constantly evolving, requiring dynamic and proactive security strategies.
Key cybersecurity threats include:
- Phishing and social engineering attacks
- Unauthorized access through compromised credentials
- Malware and ransomware infiltrations
- Data breaches and information theft
- Distributed denial of service (DDoS) attacks
Vulnerability Landscape
According to research in the African Journal of Information and Communication, cybersecurity awareness remains a significant challenge in digital environments. Cybercriminals continuously develop more sophisticated methods to penetrate SaaS application defenses, exploiting human error, technical vulnerabilities, and complex interconnected systems.
Organizations must adopt a comprehensive approach to threat management, which involves continuous monitoring, regular security assessments, employee training, and implementing multi-layered defense mechanisms.
Below is a table summarising key cybersecurity threats faced by SaaS applications, offering a concise reference for understanding the primary risks.
| Threat Type | Description |
|---|---|
| Phishing and Social Engineering | Tricking users into revealing sensitive information or credentials via deceptive tactics |
| Compromised Credentials | Gaining unauthorised access through stolen or leaked usernames and passwords |
| Malware and Ransomware | Malicious software infections aimed at disrupting, stealing, or holding data for ransom |
| Data Breaches and Information Theft | Unauthorised extraction or exposure of confidential organisational data |
| Distributed Denial of Service (DDoS) | Overwhelming cloud services to cause disruption or downtime |
| Understanding the dynamic nature of these threats is crucial for developing resilient SaaS security strategies that can adapt to emerging cybersecurity challenges. |
Key Concepts and Strategies in SaaS Security
SaaS security represents a sophisticated approach to protecting cloud-based software applications, requiring comprehensive strategies that address complex digital vulnerabilities. Organizations must develop robust frameworks that anticipate and mitigate potential security risks across multiple dimensions.
Core Security Architecture
Effective SaaS security architecture involves creating multiple layers of protection that work synergistically to defend against potential breaches. This multilayered approach ensures that even if one security mechanism fails, additional safeguards remain active.
Key architectural components include:
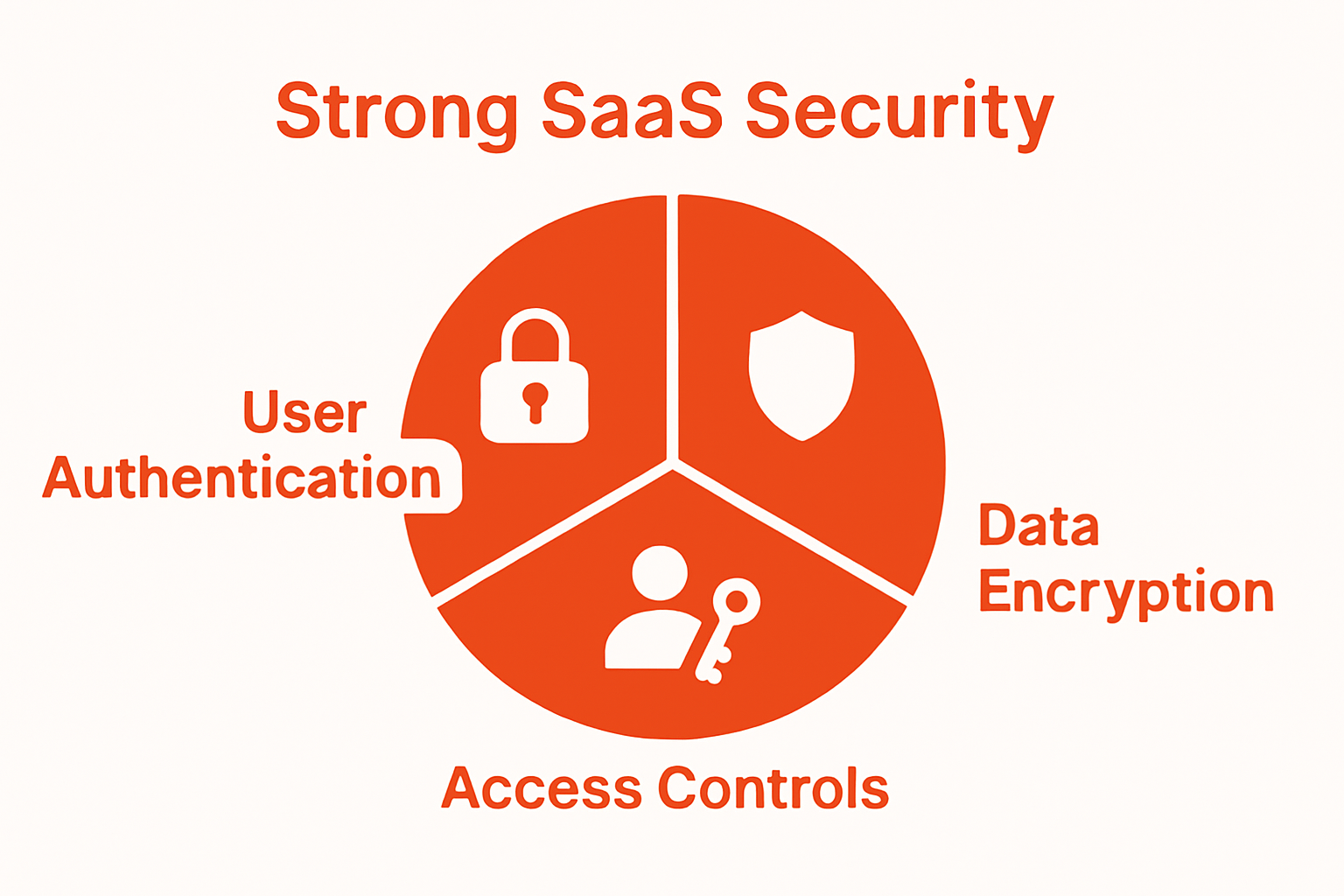
- Identity and access management systems
- Advanced encryption protocols
- Real-time threat monitoring mechanisms
- Comprehensive user authentication frameworks
- Automated security response systems
Strategic Security Implementation
According to research from the State Security Agency, security strategies must be dynamic and adaptive. Organizations need to move beyond static defense mechanisms and develop flexible security frameworks that can rapidly respond to emerging technological challenges.
Successful SaaS security implementation requires a holistic approach that combines technological solutions with human expertise. This means integrating advanced technical controls with ongoing employee training, creating a comprehensive security ecosystem that addresses both technological vulnerabilities and potential human error.
To clarify the core security measures discussed, the table below outlines foundational components of SaaS security architecture and their primary functions in protecting cloud-based applications.
| Security Component | Primary Function |
|---|---|
| Identity and Access Management | Controls user identification and regulates system privileges |
| Encryption Protocols | Secures data during transmission and storage |
| Threat Monitoring Mechanisms | Detects and alerts on abnormal or malicious activities |
| Authentication Frameworks | Verifies and manages user access |
| Automated Security Response | Initiates prompt actions to counteract detected threats |
| By adopting a proactive and integrated security strategy, businesses can significantly reduce their risk exposure and maintain the integrity of their cloud-based applications. |
Real-World Implications of Strong SaaS Security
Strong SaaS security goes far beyond technical configurations, directly impacting an organization’s reputation, financial stability, and operational resilience. In an increasingly digital business landscape, the consequences of security vulnerabilities can be profound and far-reaching.
Business Continuity and Trust
Effective SaaS security serves as a critical foundation for maintaining customer confidence and ensuring uninterrupted business operations. Organizations that demonstrate robust security practices create a competitive advantage by signaling reliability and commitment to protecting sensitive information.
Key business implications of strong security include:
- Protecting organizational reputation
- Maintaining customer and stakeholder trust
- Preventing financial losses from potential breaches
- Ensuring regulatory compliance
- Enabling smooth digital transformation
Economic and Operational Impact
According to research from the University of Johannesburg, cybersecurity capabilities are increasingly becoming a critical business differentiator. A single security breach can result in substantial financial losses, legal complications, and long-term reputational damage.
Beyond immediate financial consequences, strong SaaS security enables organizations to innovate with confidence, explore new digital opportunities, and maintain a competitive edge in rapidly evolving technological landscapes. By prioritizing comprehensive security strategies, businesses can transform potential vulnerabilities into strategic advantages, fostering a culture of digital resilience and proactive risk management.
Ready to Strengthen Your SaaS Security and Digital Protection?
The article has shown just how complex SaaS security can be for businesses like yours. From data breaches and ransomware to managing user access and ensuring compliance, the risks are real and the stakes are high. If you are concerned about safeguarding sensitive information or feel unsure whether your current approach gives you enough protection, now is the time to address these gaps. Many professional firms worry about operational continuity and reputation when facing growing security threats. You need a solution that goes beyond standard protections and fits modern business needs.
At Techtron, we help South African organisations take control of their SaaS and digital security with proactive managed IT support. With our expertise in backup, disaster recovery, and robust cybersecurity strategies, we empower engineering, financial, and mid-sized firms to defend against evolving threats while meeting compliance requirements. Discover how our cloud solutions and expert guidance can help you get ahead of risks. Visit our fully managed IT services page for more details or get in touch directly to secure your digital environment today. Stop wondering if you are protected and start building a stronger IT future now.
Frequently Asked Questions
What is SaaS security?
SaaS security is a comprehensive approach to protecting cloud-based software applications and the sensitive data they manage. It involves implementing effective measures against unauthorized access, data breaches, and cyber threats unique to cloud environments.
Why is SaaS security important for businesses?
SaaS security is crucial for businesses as it helps mitigate risks, protect sensitive information, and ensure operational continuity. Robust security practices enhance customer trust and prevent financial losses associated with data breaches.
What are the key principles of data protection in SaaS security?
Key principles include encrypting sensitive information during transmission and storage, implementing strong authentication and authorization protocols, enforcing granular access controls, and ensuring comprehensive data backup and recovery systems are in place.
What types of threats do SaaS applications face?
SaaS applications are vulnerable to a range of cyber threats, including phishing attacks, unauthorized access through compromised credentials, malware infiltrations, data breaches, and DDoS attacks. Continuous monitoring and adaptive security strategies are essential to mitigate these risks.
Recommended
- Vendor Security Audit Services 2024 and Cybersecurity Compliance | TECHTRON
- Cybersecurity in South Africa | TECHTRON
- 4 changes in the cybersecurity insurance market | TECHTRON
- What to choose – service agreements or ad hoc | TECHTRON
- The different formats & mistakes made when writing or answering security questionnaires