
Cybersecurity Best Practices 2025: Complete Guide
Cybercrime is predicted to cost the world over $10.5 trillion annually by 2025, making digital safety more urgent than ever. With attackers rapidly adopting artificial intelligence and other advanced technologies, businesses and individuals face growing risks each day. Staying protected now means understanding the most recent best practices, emerging threats, and critical controls that truly keep your information safe in a shifting online world.
Key Takeaways
| Point | Details |
|---|---|
| Proactive Cybersecurity Strategies | Organizations must adopt adaptive and continuous cybersecurity measures addressing both human behaviors and technological vulnerabilities. |
| Emerging Threat Trends | Awareness of AI-enhanced attacks and ransomware-as-a-service is vital for developing effective defensive strategies. |
| Compliance as a Priority | Cybersecurity compliance should be viewed as a strategic investment in organizational risk management rather than a technical obligation. |
| Holistic Risk Management | Organizations should integrate human-centric strategies to mitigate human error and enhance overall cybersecurity posture. |
Defining Cybersecurity Best Practices in 2025
Cybersecurity best practices in 2025 represent a comprehensive approach to protecting digital assets, systems, and networks from sophisticated cyber threats. As digital transformation accelerates, organizations must adopt proactive and adaptive strategies that go beyond traditional defensive mechanisms. According to Government of South Africa, vigilance and responsible online behavior are critical in mitigating emerging cyber risks.
Cybersecurity best practices now encompass a holistic framework that integrates technology, human awareness, and strategic risk management. Key components include robust risk assessment, continuous monitoring, employee training, and implementing multi-layered security protocols. Cybersecurity Hub emphasizes the importance of developing comprehensive guidelines that address both technical vulnerabilities and human factors.
The evolving cybersecurity landscape demands a dynamic approach characterized by:
- Continuous threat intelligence gathering
- Advanced threat detection mechanisms
- Regular security infrastructure updates
- Comprehensive incident response planning
- Proactive vulnerability management
Effective cybersecurity in 2025 requires organizations to view security not as a static solution, but as an ongoing, adaptive process that anticipates and neutralizes potential threats before they can cause significant damage.
Emerging Threats and Attack Trends
Cyber threats continue to evolve at an unprecedented pace, presenting increasingly sophisticated challenges for organizations and individuals alike. Firm reports highlight a significant rise in advanced attack methodologies, with ransomware, AI-powered phishing, and credential theft emerging as primary concerns in the cybersecurity landscape.
The technological battleground has dramatically transformed, with cybercriminals leveraging artificial intelligence and machine learning to create more complex and adaptive attack strategies. According to University of Johannesburg, there has been a staggering 44% increase in cyberattacks in 2024, underscoring the urgent need for robust defensive mechanisms.
Key emerging threat trends include:
- Artificial Intelligence-Enhanced Attacks: Cybercriminals using AI to create more sophisticated phishing techniques
- Ransomware-as-a-Service: Increased accessibility of malicious software for non-technical threat actors
- Supply Chain Vulnerabilities: Targeting interconnected business ecosystems
- Advanced Persistent Threats: Long-term targeted attacks with complex infiltration strategies
- Deepfake Social Engineering: Manipulating digital identities to bypass security protocols
Understanding these emerging threats requires a proactive, adaptive approach that anticipates potential vulnerabilities and develops comprehensive defensive strategies before attacks can materialize.
Essential Controls and Security Technologies
In 2025, cybersecurity controls represent a critical line of defense against increasingly sophisticated digital threats. Government of South Africa emphasizes the strategic importance of implementing robust information system protections that build national digital resilience and strengthen overall security infrastructure.
Comprehensive security technologies now require a multi-layered approach that integrates advanced technological solutions with strategic human-centric controls.
IMAGE:descriptive_key_1] [Cybersecurity Hub recommends implementing critical security mechanisms that address potential vulnerabilities across technological and human domains.
Key essential controls and security technologies include:
Here’s a comparison of key cybersecurity controls and technologies in 2025:
| Control/Technology | Primary Function | Key Benefits |
|---|---|---|
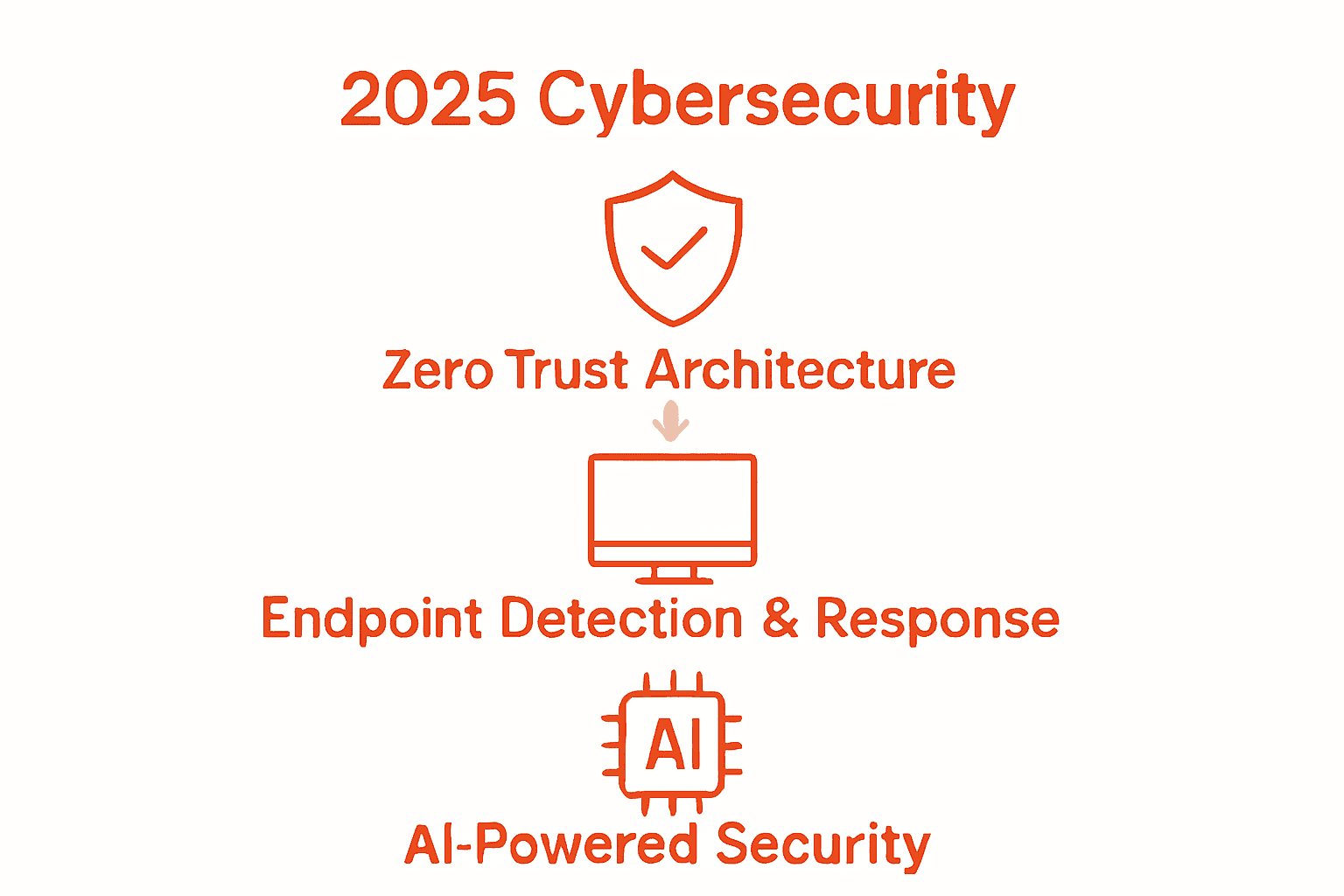
| Zero Trust Architecture | Continuous access verification | Prevents unauthorised access |
| Endpoint Detection & Response | Real-time monitoring & response | Immediate threat mitigation |
| Multi-Factor Authentication (MFA) | Sophisticated identity verification | Reduces risk of credential theft |
| AI-Powered Security Systems | Predictive detection & automation | Detects advanced threats quickly |
| Encrypted Communication Protocols | Secure data transmission | Protects sensitive information |
| Cloud Security Posture Management | Guarding cloud infrastructure | Ensures cloud compliance & safety |
- Zero Trust Architecture: Continuous verification for all network access points
- Advanced Endpoint Detection and Response (EDR): Real-time threat monitoring and immediate incident response
- Multi-Factor Authentication (MFA): Sophisticated identity verification processes
- Artificial Intelligence-Powered Security Systems: Predictive threat detection and automated response mechanisms
- Encrypted Communication Protocols: Securing data transmission across networks
- Cloud Security Posture Management: Comprehensive protection for distributed cloud infrastructure
Successful implementation of these technologies requires a holistic approach that balances technological sophistication with practical, adaptable security strategies tailored to an organization’s specific risk landscape.
Compliance Requirements for South African Firms
Cybersecurity compliance has become a critical priority for South African organizations in 2025, requiring a comprehensive approach to protecting digital infrastructure and sensitive information. State Security Agency is actively finalizing consolidated assessments to establish robust regulatory frameworks that address emerging digital threats and organizational vulnerabilities.
The compliance landscape now demands a holistic strategy that integrates legal, technological, and operational safeguards. Government of South Africa emphasizes the shared responsibility of cybersecurity, highlighting that compliance is no longer just a technical requirement but a fundamental aspect of organizational risk management.
Key compliance requirements for South African firms include:
- Protection of Personal Information Act (POPIA) compliance
- Mandatory Cybersecurity Risk Assessments: Annual comprehensive evaluations
- Data Breach Notification Protocols: Immediate reporting mechanisms
- Employee Cybersecurity Training Programs: Mandatory digital literacy initiatives
- Third-Party Vendor Security Evaluations: Comprehensive supply chain risk management
- Incident Response and Recovery Planning: Detailed strategic frameworks
Successful compliance requires organizations to view these requirements not as bureaucratic obligations, but as strategic investments in their long-term digital resilience and organizational integrity.
Managing Human Error and Insider Risks
Human error remains the most significant vulnerability in cybersecurity strategies, representing a critical point of potential breach for organizations. Firm Research highlights that end-users consistently represent the first potential point of failure in cybersecurity measures, underscoring the importance of developing robust cyber awareness and defensive behavioral patterns.
Government of South Africa emphasizes the critical role of responsible online behavior and public awareness in mitigating cyber risks. Organizations must move beyond traditional technical controls to create comprehensive strategies that address the human element of cybersecurity.
Key strategies for managing human error and insider risks include:
- Continuous Security Awareness Training: Regular, engaging educational programs
- Psychological Risk Profiling: Understanding individual behavioral vulnerabilities
- Zero Trust User Authentication: Implementing strict identity verification protocols
- Simulated Phishing Exercises: Practical training to recognize potential threats
- Adaptive Access Controls: Dynamic permissions based on user behavior
- Incident Reporting Mechanisms: Transparent and supportive reporting cultures
Successful risk management requires a holistic approach that combines technological solutions with human-centric strategies, transforming employees from potential security liabilities into active defenders of organizational digital infrastructure.
Common Implementation Mistakes to Avoid
Cybersecurity implementation requires meticulous attention to detail and a proactive approach to identifying potential vulnerabilities. Firm Research warns that neglecting critical security fundamentals like timely software updates and robust authentication mechanisms can expose organizations to significant cyber risks.
University of Johannesburg News highlights the critical shortage of skilled cybersecurity professionals as a fundamental challenge that can lead to substantial implementation errors. Organizations must recognize that effective cybersecurity is not just about technological solutions, but also about building comprehensive, strategic capabilities.
Common implementation mistakes organizations must actively avoid include:
- Reactive Instead of Proactive Security: Waiting for breaches to occur before taking action
- Inadequate Staff Training: Failing to create a culture of cybersecurity awareness
- Overlooking Regular Software Patching: Leaving systems vulnerable to known exploits
- Insufficient Access Control Mechanisms: Implementing overly permissive user privileges
- Neglecting Comprehensive Backup Strategies: Not maintaining robust data recovery plans
- Poor Vendor Security Assessment: Failing to evaluate third-party security risks
Successful cybersecurity implementation demands a holistic, forward-thinking approach that anticipates potential vulnerabilities and creates robust, adaptive defense mechanisms across technological and human domains.
Secure Your Business Future with Expert Cybersecurity Support
Facing ever-evolving cyber threats in 2025 means you cannot afford to rely on outdated or reactive security measures. From combating AI-powered phishing attacks to managing insider risks and ensuring compliance with South African regulations such as POPIA, businesses must adopt proactive, layered cybersecurity strategies that safeguard critical data and maintain operational continuity. The challenges of implementing Zero Trust architectures, real-time endpoint detection, and continuous employee training can overwhelm internal teams and expose your firm to costly breaches.
At Techtron Managed IT Services, we understand the weight of these challenges on professional service firms ranging from engineering to financial sectors. Our comprehensive cybersecurity solutions are designed to reduce your technical burden while providing adaptive protections like advanced threat detection, multi-factor authentication, and ongoing risk assessments tailored to your business needs. Don’t wait for cyber threats to disrupt your operations or damage your reputation. Discover how our proactive IT management and security services can fortify your digital infrastructure today.
Take the first step toward resilient cybersecurity. Visit Techtron now to learn how we help companies like yours transform vulnerabilities into strengths with expert support and trusted IT strategies.
Frequently Asked Questions
What are the key components of cybersecurity best practices in 2025?
Cybersecurity best practices in 2025 encompass a holistic approach that includes robust risk assessment, continuous monitoring, employee training, and implementing multi-layered security protocols.
How can organizations mitigate emerging cyber threats?
Organizations can mitigate emerging cyber threats by adopting proactive strategies such as continuous threat intelligence gathering, advanced threat detection mechanisms, regular security infrastructure updates, and comprehensive incident response planning.
What are the most significant emerging threats in cybersecurity?
Significant emerging threats include AI-enhanced attacks, ransomware-as-a-service, supply chain vulnerabilities, advanced persistent threats, and deepfake social engineering methods.
What common mistakes should organizations avoid when implementing cybersecurity measures?
Organizations should avoid common mistakes such as being reactive instead of proactive, inadequate staff training, overlooking regular software patching, having insufficient access control mechanisms, and neglecting comprehensive backup strategies.