Understanding IT Risk Management Strategies for Businesses
Every business relies on technology to keep things running smoothly and protect their valuable data. Yet, while most companies install firewalls and update passwords, there’s a bigger challenge lurking in the shadows. According to PwC, organisations that neglect robust IT risk management can face financial losses worth millions of rand. So the real surprise is this: it’s not just about stopping cybercriminals or ticking compliance boxes. True IT risk management turns digital threats into a strategic lever that can keep your business one step ahead.
Table of Contents
- What Are IT Risk Management Strategies And Their Purpose?
- Why IT Risk Management Matters For Businesses
- Key Concepts Behind IT Risk Management Strategies
- How IT Risk Management Strategies Function In Practice
- Real-World Contexts Of IT Risk Management Strategies
Quick Summary
| Takeaway | Explanation |
|---|---|
| Proactive risk management is essential. | Identifying and addressing technological threats before they escalate is key to maintaining operational effectiveness. |
| Compliance is mandatory for businesses. | Organizations must adhere to regulations like the King Code to protect digital assets and ensure information integrity. |
| Continuous monitoring enhances resilience. | Ongoing assessments and real-time threat detection support organizations in adapting to evolving risks. |
| Tailored strategies are industry-specific. | Different sectors face unique challenges, necessitating customized IT risk management approaches to effectively mitigate risks. |
| Invest in employee training on security. | Regular training ensures staff are informed about the latest cybersecurity protocols and aware of potential risks. |
What are IT Risk Management Strategies and Their Purpose?
IT risk management strategies represent a systematic approach businesses use to identify, assess, mitigate, and monitor potential technology-related risks that could compromise operational effectiveness, financial stability, and organizational security. These comprehensive strategies aim to protect an organization’s digital infrastructure, data assets, and technological investments from potential threats and vulnerabilities.
Understanding Core Risk Management Principles
At its fundamental level, IT risk management involves a proactive methodology for recognizing potential technological challenges before they transform into significant operational disruptions. Organizations develop these strategies by conducting thorough risk assessments that evaluate potential weaknesses across their technological ecosystems.
The primary objectives of IT risk management strategies include:
- Protecting critical business information and digital assets
- Ensuring continuous operational resilience
- Maintaining regulatory compliance and data protection standards
- Minimizing potential financial losses from technological failures
- Safeguarding organizational reputation against cybersecurity incidents
Strategic Risk Assessment Framework
Effective IT risk management requires a structured framework that systematically evaluates potential technological vulnerabilities. According to Gartner Research, organizations must implement comprehensive risk assessment processes that include continuous monitoring, real-time threat detection, and adaptive response mechanisms.
This framework typically involves multiple interconnected stages: risk identification, risk analysis, risk evaluation, risk treatment, and ongoing risk monitoring.
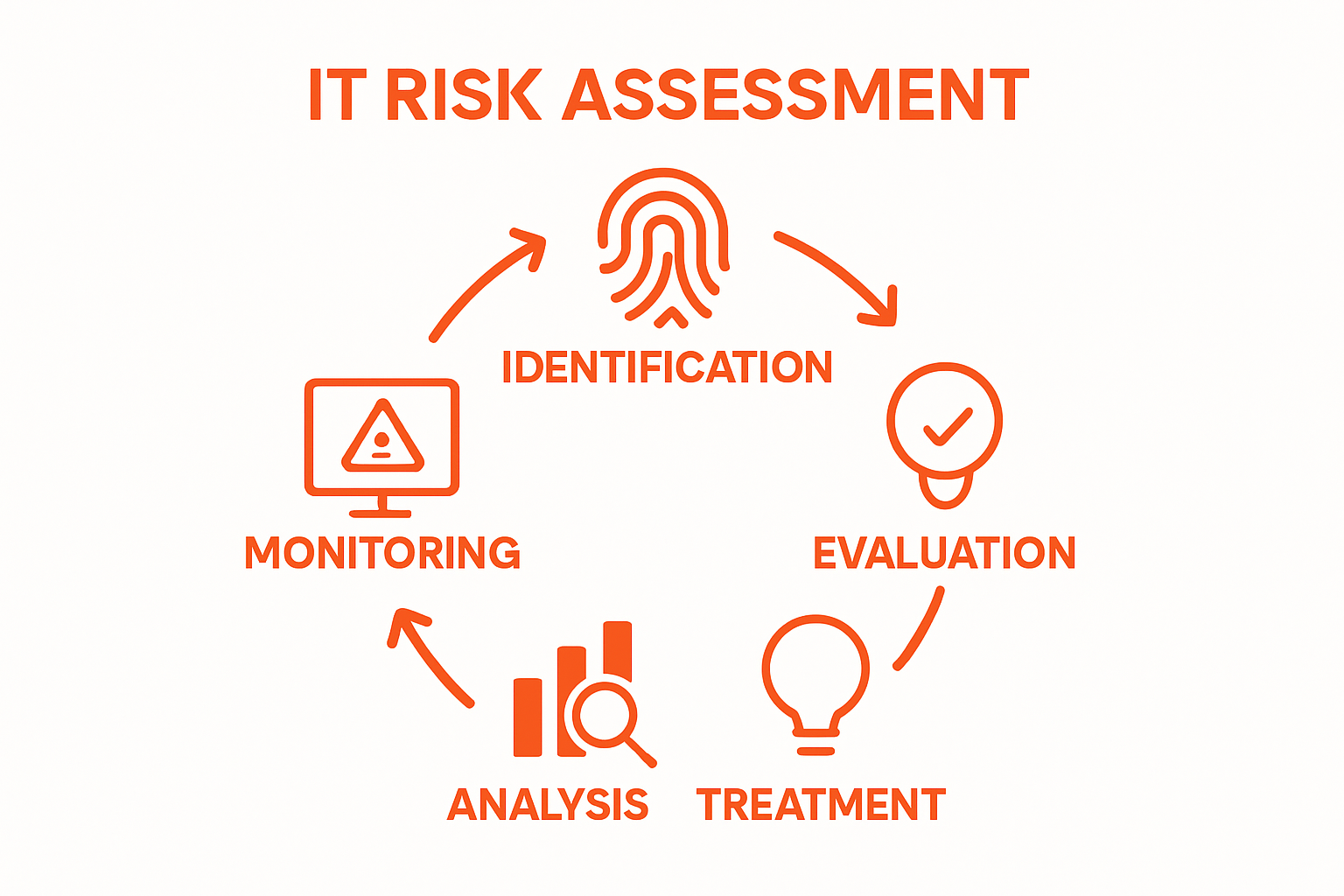 By adopting a holistic approach, businesses can develop resilient technological infrastructure capable of anticipating and neutralizing potential digital threats before they escalate into significant operational challenges.
By adopting a holistic approach, businesses can develop resilient technological infrastructure capable of anticipating and neutralizing potential digital threats before they escalate into significant operational challenges.
The ultimate purpose of IT risk management strategies extends beyond mere technical compliance. These strategies represent a critical business philosophy that integrates technological safeguarding with strategic organizational objectives, ensuring that digital resources remain secure, efficient, and aligned with broader business goals.
Why IT Risk Management Matters for Businesses
IT risk management has transformed from a technical afterthought to a critical strategic priority for businesses across diverse sectors. As technological ecosystems become increasingly complex and interconnected, organizations must recognize that effective risk management is not merely a defensive mechanism but a fundamental driver of sustainable business performance.
Financial and Operational Implications
The financial consequences of inadequate IT risk management can be devastating. According to PwC’s Global Economic Crime and Fraud Survey, organizations that fail to implement robust technological risk strategies face potential financial losses that can reach millions of rand in direct and indirect costs.
The potential impacts include:
- Significant monetary losses from data breaches
- Operational disruptions leading to productivity decline
- Reputational damage and loss of customer trust
- Potential legal and regulatory penalties
- Increased insurance and compliance costs
Regulatory Compliance and Governance
In the South African business landscape, IT risk management is not optional but a mandatory requirement. The King Code on Corporate Governance and the Electronic Communications and Transactions Act mandate that organizations develop comprehensive frameworks to protect digital assets and ensure information integrity.
Businesses must demonstrate a proactive approach to technological risk management, which involves:
- Implementing systematic risk assessment processes
- Developing clear cybersecurity policies
- Maintaining detailed documentation of risk mitigation strategies
- Regular staff training on technological security protocols
- Continuous monitoring and updating of risk management frameworks
By prioritizing IT risk management, businesses can transform potential vulnerabilities into strategic opportunities for enhanced operational resilience, building a technological infrastructure that not only protects against threats but also supports sustainable growth and innovation.
Key Concepts Behind IT Risk Management Strategies
IT risk management strategies are built upon a sophisticated framework of interconnected concepts that enable organizations to systematically address technological vulnerabilities and potential operational disruptions. These strategies represent a sophisticated approach to understanding, evaluating, and mitigating potential risks within an organization’s technological ecosystem.
The following table summarises the primary categories of IT risks commonly faced by organisations, providing concise definitions for each to clarify their distinct focuses within risk management.
| IT Risk Category | Definition |
|---|---|
| Technological infrastructure risks | Risks arising from failures or weaknesses in hardware, software, or network architecture |
| Cybersecurity vulnerabilities | Threats involving unauthorised access, malware, or cyberattacks on digital assets |
| Data privacy and protection risks | Risks of data breaches, loss, or non-compliance impacting sensitive or personal information |
| Compliance and regulatory risks | Risks of failing to meet legal, industry, or national standards for technology management |
| Operational continuity risks | Threats to ongoing business processes, including downtime or loss of critical services |
Risk Identification and Classification
Risk identification forms the foundational element of effective IT risk management. This process involves comprehensively mapping an organization’s technological infrastructure to uncover potential vulnerabilities, threats, and potential points of failure. According to ISACA’s Risk IT Framework, organizations must develop a structured approach to categorizing risks based on their potential impact and likelihood of occurrence.
The primary categories of IT risks typically include:
- Technological infrastructure risks
- Cybersecurity vulnerabilities
- Data privacy and protection risks
- Compliance and regulatory risks
- Operational continuity risks
Risk Assessment and Quantification
Once risks are identified, organizations must develop a robust methodology for assessing and quantifying their potential impact. This involves creating a systematic approach that evaluates risks based on multiple dimensions, including financial implications, operational disruption potential, and long-term strategic consequences.
Key considerations in risk assessment include:
- Probability of risk occurrence
- Potential financial and operational impact
- Speed of potential threat escalation
- Existing mitigation capabilities
- Potential recovery and restoration strategies
By developing a nuanced understanding of these key concepts, businesses can transform IT risk management from a defensive mechanism into a strategic enabler of organizational resilience and technological innovation.
 The goal is not merely to prevent potential threats but to create a dynamic, adaptive framework that supports continuous organizational growth and technological advancement.
The goal is not merely to prevent potential threats but to create a dynamic, adaptive framework that supports continuous organizational growth and technological advancement.
How IT Risk Management Strategies Function in Practice
IT risk management strategies transform theoretical frameworks into actionable operational practices that systematically protect an organization’s technological infrastructure. These strategies move beyond abstract concepts, providing concrete mechanisms for identifying, analyzing, and responding to potential technological vulnerabilities.
Practical Implementation Frameworks
Practical implementation requires a structured approach that translates risk management principles into tangible organizational processes. According to the International Organization for Standardization (ISO) 31000 Risk Management Guidelines, organizations must develop comprehensive frameworks that integrate risk management into every operational decision and technological investment.
Key components of practical implementation include:
- Establishing clear governance structures
- Defining precise risk management roles and responsibilities
- Creating transparent communication channels
- Developing adaptive response protocols
- Implementing continuous monitoring mechanisms
Risk Mitigation and Response Strategies
Effective risk management goes beyond identification, focusing on developing robust mitigation and response strategies. This involves creating multiple layers of technological defense that can quickly detect, contain, and neutralize potential threats before they escalate into significant operational disruptions.
Primary mitigation approaches encompass:
- Technical controls like firewalls and encryption
- Regular security awareness training
- Comprehensive backup and disaster recovery systems
- Periodic vulnerability assessments
- Incident response planning
By integrating these practical strategies, organizations can transform IT risk management from a reactive defensive mechanism into a proactive, strategic tool that supports technological resilience and sustainable business growth. The ultimate goal is creating an adaptive technological ecosystem capable of anticipating, responding to, and neutralizing potential risks with minimal operational interruption.
Real-World Contexts of IT Risk Management Strategies
IT risk management strategies transcend theoretical frameworks, finding critical application across diverse industries where technological vulnerabilities can significantly impact organizational performance. Real-world implementations demonstrate how sophisticated risk management approaches protect businesses from complex digital threats and operational disruptions.
Industry-Specific Risk Management Approaches
Different sectors require tailored IT risk management strategies that address unique technological challenges and regulatory requirements. Financial institutions, for instance, demand more rigorous risk management protocols compared to other industries due to the sensitive nature of their digital assets.
Key industry-specific considerations include:
- Banking sector: Stringent transaction security protocols
- Healthcare: Patient data protection and compliance requirements
- Manufacturing: Protecting industrial control systems
- Retail: Securing customer payment infrastructure
- Government: Defending critical national infrastructure
Technological Adaptation and Contextual Implementation
According to Deloitte’s Global Risk Management Survey, successful risk management strategies require continuous adaptation to emerging technological landscapes. Organizations must develop flexible frameworks that can quickly respond to evolving digital threats and technological innovations.
Effective contextual implementation involves:
- Regular technological infrastructure assessments
- Continuous staff training and awareness programs
- Dynamic risk assessment methodologies
- Scalable security infrastructure
- Integrated multi-layered defense mechanisms
By understanding and implementing context-specific IT risk management strategies, businesses can transform potential technological vulnerabilities into opportunities for enhanced operational resilience, creating robust digital ecosystems that support sustainable growth and innovation.
Secure Your Business with Tailored IT Risk Management
Facing growing digital threats and worried about the real impact on your business? You have just learned in the article how a single vulnerability can disrupt operations, compromise data, and damage your reputation. Many businesses struggle to adapt frameworks like ISO 31000 or sustain the ongoing monitoring and proactive governance required to meet South African regulatory standards. The pressure to protect digital assets and maintain compliance can leave your team stretched and your business exposed.
Let us handle your IT risk management so you can focus on growth. At Techtron Managed IT Services, our expert team supports professional firms and mid-sized companies with robust cybersecurity, disaster recovery, and resilient cloud solutions, all driven by the very frameworks discussed above. Curious how a co-managed or fully managed approach can radically strengthen your organisation’s risk posture? Visit our home page to explore our full offering and contact us today for a personalised assessment. Act now to make your company’s digital future secure and compliant before the next risk becomes reality.
Frequently Asked Questions
What are IT risk management strategies?
IT risk management strategies are systematic approaches that businesses use to identify, assess, mitigate, and monitor potential technology-related risks that could impact operational effectiveness, financial stability, and organizational security.
Why is IT risk management important for businesses?
IT risk management is crucial for businesses as it helps protect digital assets, ensures continuous operational resilience, maintains regulatory compliance, minimizes financial losses from technological failures, and safeguards organizational reputation against cybersecurity incidents.
What are the key components of an effective IT risk management framework?
An effective IT risk management framework includes risk identification, risk analysis, risk evaluation, risk treatment, and ongoing risk monitoring to systematically address potential technological vulnerabilities.
How can organizations implement IT risk management strategies in practice?
Organizations can implement IT risk management strategies by establishing governance structures, defining roles and responsibilities, creating communication channels, developing response protocols, and continuously monitoring their technological landscape.