Understanding Mobile Device Security Policies for Businesses
Mobile device security policies sound like dry paperwork but they shape the very backbone of every modern business. Most people think it is all about passwords and locked screens yet almost every major breach in the past five years involved an unsecured mobile device. The real surprise is that these policies are not just about stopping hackers but about keeping your business running smoothly while dodging financial and reputational pitfalls.
Table of Contents
- Defining Mobile Device Security Policies: Key Concepts
- The Importance of Mobile Device Security in Businesses
- How Mobile Device Security Policies Work: Framework and Components
- Real-World Impact of Mobile Device Security Policies
- Emerging Trends in Mobile Device Security for Professionals
Quick Summary
| Takeaway | Explanation |
|---|---|
| Implement robust device authentication | Ensure that all users verify their identities effectively to access systems securely. |
| Prioritize data encryption | Protect sensitive information on mobile devices by encrypting data at rest and in transit. |
| Conduct regular risk assessments | Regularly evaluate access and security vulnerabilities to enhance policy effectiveness and adapt to new threats. |
| Establish clear incident response protocols | Prepare structured procedures to address security breaches swiftly and effectively. |
| Adopt advanced authentication technologies | Use biometrics and multi-factor systems for stronger user verification and security. |
Defining Mobile Device Security Policies: Key Concepts
Mobile device security policies represent a comprehensive framework designed to protect organizational digital assets and sensitive information across mobile computing platforms. These strategic guidelines establish critical protocols for managing smartphones, tablets, laptops, and other portable devices used within professional environments.
Understanding Core Security Policy Components
Effective mobile device security policies encompass multiple interconnected dimensions that address technological, operational, and human factors. These policies go beyond simple technical restrictions, creating a holistic approach to safeguarding organizational data.
Key foundational components include:
To clarify the foundational building blocks of a mobile device security policy, the following table defines the core components and their roles in a business environment:
| Security Policy Component | Definition/Role |
|---|---|
| Device Authentication | Ensures only authorised users can access devices and organisational systems |
| Data Encryption | Protects sensitive business information stored and transmitted via mobile devices |
| Remote Management Capabilities | Allows administrators to control, track, and potentially wipe devices remotely |
| Acceptable Use Guidelines | Outlines acceptable behaviours and activities regarding device and data usage |
| Incident Response Protocols | Establishes procedures for responding to and mitigating security breaches |
| Employee Training | Provides ongoing education to reduce human error and raise security awareness |
- Device Authentication: Establishing robust methods for verifying user identity before system access
- Data Encryption: Protecting information stored and transmitted through mobile platforms
- Remote Management Capabilities: Enabling administrators to control, track, and if necessary, wipe devices remotely
According to NIST Guidelines, mobile device security policies must address the entire technological ecosystem, recognizing that modern workplaces increasingly rely on portable computing solutions.
Risk Management and Policy Implementation
Implementing mobile device security policies requires a nuanced understanding of potential vulnerabilities. Organizations must balance operational flexibility with stringent protective measures. Comprehensive policies integrate technical controls, employee training, and clear procedural guidelines.
This approach involves:
- Conducting regular risk assessments
- Developing clear acceptable use guidelines
- Creating incident response protocols
- Maintaining ongoing employee education programs
By establishing proactive mobile device security policies, businesses can significantly reduce potential cybersecurity threats while maintaining productive technological environments.

The Importance of Mobile Device Security in Businesses
Mobile device security has transformed from an optional consideration to a critical business imperative in the contemporary digital landscape. As organizations increasingly depend on mobile technologies for daily operations, understanding the strategic significance of robust security measures becomes paramount.
Digital Threat Landscape and Business Vulnerabilities
Modern businesses face an unprecedented array of cybersecurity challenges directly linked to mobile device usage. Unsecured mobile devices represent significant entry points for potential cyber attacks, enabling malicious actors to exploit organizational networks through seemingly innocuous technological endpoints.
Key vulnerabilities include:
- Unauthorized data access through compromised devices
- Potential information leakage from unprotected communication channels
- Risk of sensitive corporate information being exposed through personal device usage
According to NIST’s Mobile Device Security Guidelines, organizations must adopt comprehensive strategies that address both technological and human factors in mobile security management.
Strategic Implications of Comprehensive Mobile Security
Effective mobile device security extends beyond technical protections. It represents a holistic approach to safeguarding organizational intellectual property, maintaining regulatory compliance, and preserving operational integrity.
Businesses implementing robust mobile security frameworks can expect:
- Enhanced protection of confidential corporate information
- Reduced risk of financial losses from potential data breaches
- Improved employee productivity through secure, reliable mobile infrastructure
By recognizing mobile device security as a strategic business function rather than a mere technical requirement, organizations can transform potential vulnerabilities into opportunities for strengthened digital resilience.
How Mobile Device Security Policies Work: Framework and Components
Mobile device security policies function as sophisticated technological frameworks designed to protect organizational digital infrastructure through systematic risk management and strategic control mechanisms. These intricate systems integrate multiple layers of technical and procedural safeguards to mitigate potential cybersecurity vulnerabilities.
Architectural Design of Security Policy Frameworks
Security policy frameworks operate as comprehensive governance structures that establish clear protocols for device usage, data protection, and access management. These frameworks transcend simple technical configurations, creating holistic approaches that address human behavior, technological limitations, and organizational risk tolerance.
Key architectural components include:
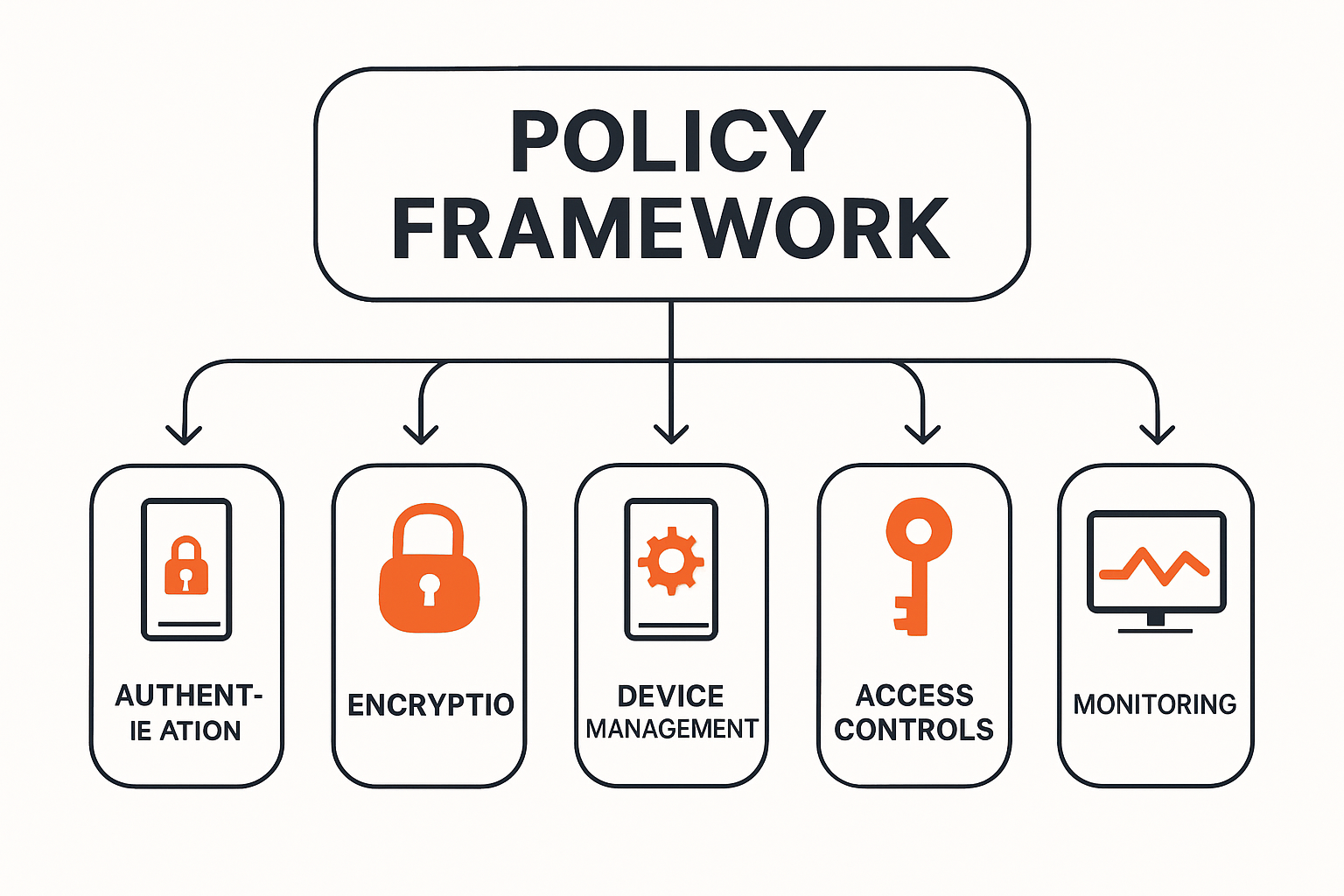
- Centralized device management systems
- User authentication protocols
- Granular access control mechanisms
- Continuous monitoring and threat detection capabilities
According to NIST Mobile Device Security Guidelines, effective policy frameworks must balance robust security measures with operational flexibility.
Implementation and Control Mechanisms
Successful mobile device security policies rely on sophisticated control mechanisms that dynamically adapt to emerging technological landscapes. These mechanisms create multi-layered defense strategies that protect organizational assets through proactive and reactive security interventions.
Critical implementation strategies encompass:
- Establishing comprehensive device registration processes
- Implementing encryption standards for data transmission
- Creating clear protocols for device loss or theft
- Developing continuous employee training programs
By integrating technical controls with strategic organizational practices, mobile device security policies transform potential vulnerabilities into manageable, controlled technological environments.
Real-World Impact of Mobile Device Security Policies
Mobile device security policies have evolved from theoretical frameworks into critical operational strategies that directly influence organizational resilience, financial stability, and competitive positioning. The tangible consequences of implementing robust security measures extend far beyond technical compliance.
The table below compares the consequences of mobile device security breaches with the benefits of implementing strong policies, helping businesses see the direct impact on their operations:
| Impact Area | Consequences Without Strong Policies | Benefits With Robust Policies |
|---|---|---|
| Financial Losses | High risk of costly breaches and regulatory fines | Reduced risk of direct losses and legal penalties |
| Reputation | Loss of client trust and business opportunities | Maintained client confidence and competitive advantage |
| Operational Efficiency | Increased downtime and disrupted productivity | Streamlined operations and improved employee productivity |
| Data Protection | Exposure of sensitive information | Enhanced protection of confidential business data |
Financial and Reputational Consequences
Security breaches through mobile devices can trigger catastrophic financial repercussions for organizations. Unauthorized data access, information leakage, and potential regulatory non-compliance can result in substantial monetary losses, legal penalties, and long-term reputational damage.
Key financial implications include:
- Direct costs of data breach remediation
- Potential regulatory fines and legal settlements
- Lost business opportunities due to compromised client trust
- Increased cybersecurity insurance premiums
According to NIST Research on Mobile Device Security, organizations with comprehensive mobile security policies demonstrate significantly reduced financial risk exposure.
Operational Efficiency and Risk Mitigation
Effective mobile device security policies transform technological vulnerabilities into strategic advantages. By establishing clear protocols and implementing proactive monitoring mechanisms, businesses can create more resilient, adaptable technological ecosystems.
Operational benefits encompass:
- Enhanced data protection across distributed workforce environments
- Streamlined device management and configuration processes
- Improved employee productivity through secure, reliable infrastructure
- Reduced downtime associated with security incidents
By integrating mobile device security policies as fundamental organizational strategies, businesses can convert potential technological risks into opportunities for strategic innovation and competitive differentiation.
Emerging Trends in Mobile Device Security for Professionals
The landscape of mobile device security continues to evolve rapidly, presenting professionals with increasingly sophisticated technological solutions to address complex cybersecurity challenges. As digital threats become more nuanced, innovative approaches emerge to protect organizational digital assets and maintain operational integrity.
Advanced Authentication and Identity Management
Biometric and multi-factor authentication technologies represent the forefront of mobile device security, moving beyond traditional password-based systems. These advanced mechanisms leverage unique physiological and behavioral characteristics to create more robust user verification processes.
Key emerging authentication technologies include:
- Facial recognition with advanced depth sensing
- Behavioral biometric analysis
- Contextual authentication using device location and usage patterns
- Advanced machine learning-powered threat detection
According to NIST Mobile Device Security Guidelines, these technologies provide more dynamic and adaptive security frameworks compared to traditional static authentication methods.
Zero Trust and Adaptive Security Architectures
Zero trust security models fundamentally reimagine organizational cybersecurity approaches, treating every access attempt as potentially suspicious regardless of its origin. These frameworks require continuous verification and minimize inherent trust assumptions in network interactions.
Critical components of zero trust approaches involve:
- Continuous user and device authentication
- Granular access control mechanisms
- Real-time threat monitoring and response
- Microsegmentation of network resources
Professionals can explore emerging security technologies to understand how these innovative approaches transform mobile device protection strategies.
Strengthen Your Mobile Device Security with Techtron
Are you concerned about losing sensitive business data to cybersecurity threats lurking within your mobile workforce? The article highlights how mobile device vulnerabilities, from weak authentication to poor data encryption, put your organisation at risk of financial loss or reputational harm. You know that a holistic mobile device security policy is crucial, but building and maintaining it can be overwhelming — especially when you want to focus on growing your business, not constantly managing IT risks.
Let our specialists at Techtron help you take decisive action now. We offer advanced managed IT services, from cybersecurity solutions to secure cloud integration, tailored for South African businesses striving for compliance and operational continuity. Do not let mobile security gaps slow your team down. Visit our site now and discover how effortless it is to move from policy to protection. Speak to an expert and take charge of your mobile device security today.
Frequently Asked Questions
What are mobile device security policies?
Mobile device security policies are comprehensive guidelines designed to protect an organization’s digital assets and sensitive information on mobile devices like smartphones and tablets. These policies establish protocols for device authentication, data encryption, and remote management.
Why are mobile device security policies important for businesses?
Mobile device security policies are crucial as they protect against potential cybersecurity threats. Unsecured mobile devices can be entry points for cyber attacks, leading to unauthorized access, data leakage, and financial losses. Implementing strong policies helps safeguard confidential information and maintain regulatory compliance.
What key components should a mobile device security policy include?
A mobile device security policy should include device authentication methods, data encryption practices, remote management capabilities, acceptable use guidelines, incident response protocols, and ongoing employee training programs to effectively mitigate risks.
How can businesses assess the effectiveness of their mobile device security policies?
Businesses can assess the effectiveness of their mobile device security policies by conducting regular risk assessments, monitoring for compliance with the policies, evaluating the incidence response effectiveness, and gathering employee feedback to identify areas for improvement.