
Complete Guide to Mobile Device Security
Over 80 percent of businesses now rely on mobile devices for daily operations, yet many underestimate how quickly these tools can become security risks. As employees connect personal smartphones and tablets to corporate networks, sensitive information faces new threats from malware, phishing, and outdated software. Mastering mobile device security essentials helps prevent costly data breaches and keeps your organisation’s reputation intact by creating a safer digital environment for every user.
Key Takeaways
| Point | Details |
|---|---|
| Mobile Device Security Importance | Protecting organizational data on mobile devices is critical as personal devices used for work significantly increase cybersecurity risks. |
| Core Security Components | Essential security measures include device management, data protection, network security, and strong access controls. |
| Prevalent Threats | Common mobile security threats include malware infections, phishing attacks, and vulnerabilities from unsecured networks. |
| Best Practices for Management | Effective mobile security combines policy development, employee training, strict access controls, and continuous monitoring of device usage. |
Defining Mobile Device Security Essentials
Mobile device security represents a comprehensive approach to protecting organisational data, networks, and digital assets across smartphones, tablets, and other portable computing devices. According to research from Wits University, employees using personal devices for work purposes significantly increases cybersecurity risks, making robust security measures critical for modern businesses.
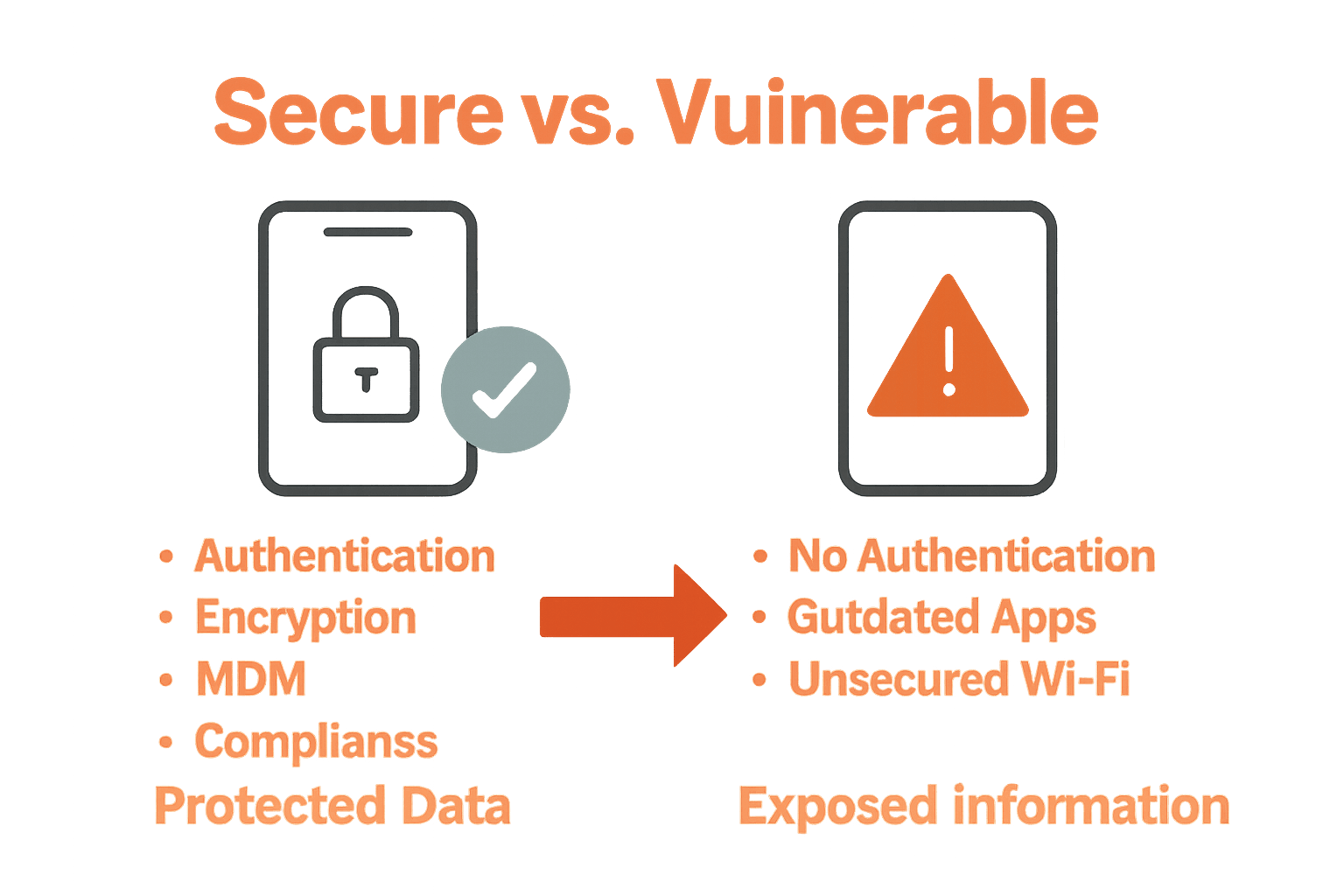
The core components of mobile device security encompass several strategic elements that work together to create a robust protection framework. These include:
- Device Management: Implementing controls that govern how mobile devices access company resources
- Data Protection: Encrypting sensitive information and creating secure transmission channels
- Network Security: Restricting and monitoring device network connections
- Access Controls: Establishing strong authentication mechanisms and user permissions
Research from ArXiv further highlights the increasing cyber-risks associated with Bring-Your-Own-Device (BYOD) policies, emphasizing that organisations must proactively develop comprehensive mobile security strategies. Without proper safeguards, businesses expose themselves to potential data breaches, unauthorized access, and significant financial and reputational damage.
Understanding these mobile device security essentials is not just a technical requirement but a strategic business imperative.
 Secure Mobile Device Management for Businesses becomes crucial in creating a holistic approach that balances employee flexibility with robust organisational protection.
Secure Mobile Device Management for Businesses becomes crucial in creating a holistic approach that balances employee flexibility with robust organisational protection.
Major Threats Facing Business Mobile Devices
Mobile devices have become critical business tools, but they simultaneously represent significant cybersecurity vulnerabilities. According to Kaspersky, mobile cyberthreats have increased dramatically, with a staggering 104% rise in mobile threats targeting South African businesses, signaling an urgent need for comprehensive security strategies.
The most prevalent mobile device threats include:
- Malware Infections: Sophisticated viruses designed to compromise device functionality
- Phishing Attacks: Deceptive communications attempting to steal sensitive credentials
- Network Vulnerabilities: Unsecured Wi-Fi networks enabling unauthorized data interception
- Social Engineering: Manipulative tactics tricking employees into revealing confidential information
- Unpatched Software: Outdated applications creating potential security backdoors
CIO highlights that BYOD (Bring Your Own Device) policies significantly exacerbate these risks, introducing complex security challenges for organisations. Employees using personal devices without robust security protocols create potential entry points for cybercriminals.
Understanding these threats is crucial, which is why reviewing our guide on understanding cybersecurity threats can provide deeper insights into protecting your business’s digital infrastructure. Proactive threat recognition and strategic mitigation remain the most effective defense against evolving mobile security risks.
Core Security Features and Technologies
Mobile device security has evolved into a complex ecosystem of sophisticated technologies designed to protect organisational digital assets. According to Accountancy SA, implementing comprehensive security features is crucial for mitigating risks associated with modern workplace mobility, particularly in Bring-Your-Own-Device (BYOD) environments.
The core security technologies businesses should prioritize include:
- Multi-Factor Authentication (MFA): Requiring multiple verification methods before device access
- End-to-End Encryption: Protecting data transmission and storage
- Mobile Device Management (MDM): Centralized control and monitoring of corporate devices
- Remote Wipe Capabilities: Enabling instant data deletion for lost or stolen devices
- Containerization: Separating personal and professional data environments
Research from ArXiv emphasizes the critical nature of implementing robust cyber-risk mitigation strategies, particularly focusing on anti-virus software, comprehensive encryption protocols, and advanced mobile device management tools. These technologies work synergistically to create multiple layers of security protection.
To gain deeper insights into emerging security technologies that can further enhance your mobile device protection strategy, explore our guide on emerging security technologies. Proactive investment in these core security features represents the most effective defense against increasingly sophisticated digital threats.
Regulatory Compliance and Data Protection Laws
Data protection laws represent a critical framework for organizations navigating the complex landscape of mobile device security. According to SAJIM, the increasing digitalization of business operations has amplified the challenges surrounding data security and privacy risks, making regulatory compliance more crucial than ever.
Key regulatory considerations for businesses include:
- Data Minimization: Collecting and storing only essential personal information
- Consent Management: Obtaining explicit user permissions for data processing
- Data Breach Notification: Implementing immediate reporting mechanisms
- User Rights: Ensuring individuals can access, correct, and delete their personal data
- Cross-Border Data Transfer Restrictions: Managing international data movement
Wits University emphasizes the critical importance of establishing clear guidelines when implementing Bring-Your-Own-Device (BYOD) policies, particularly in relation to data protection regulations. Organizations must develop comprehensive strategies that balance operational flexibility with stringent legal requirements.
To navigate these complex regulatory landscapes more effectively, explore our guide on understanding privacy laws for businesses. Proactive compliance is not just a legal necessity but a fundamental aspect of maintaining trust and protecting your organization’s reputation.
Best Practices for Managing Mobile Security
Mobile security management requires a strategic, multifaceted approach that goes beyond simple technological solutions. According to Wits University, businesses must develop comprehensive strategies that address both technical and human factors to effectively mitigate mobile security risks.
Key best practices for managing mobile security include:
- Policy Development: Creating clear, comprehensive mobile device usage guidelines
- Regular Training: Educating employees about security risks and prevention strategies
- Access Control: Implementing strict authentication and permission management
- Continuous Monitoring: Tracking device usage and potential security anomalies
- Rapid Response Planning: Establishing protocols for immediate action during security incidents
Research from ArXiv emphasizes the critical importance of establishing robust BYOD policies and providing targeted employee training. Organizations must create a holistic approach that balances technological safeguards with human awareness and proactive risk management.
To dive deeper into managing mobile security effectively, check out our guide on understanding mobile device security policies. Successful mobile security is not just about implementing tools, but creating a culture of cybersecurity awareness and vigilance.
Common Mistakes and Security Pitfalls
Mobile device security is fraught with potential vulnerabilities that can compromise entire organizational networks. According to Accountancy SA, businesses frequently encounter critical security pitfalls that can expose them to significant risks, particularly in Bring-Your-Own-Device (BYOD) environments.
The most prevalent mobile security mistakes include:
- Inadequate Authentication: Weak or non-existent multi-factor authentication protocols
- Unpatched Devices: Failing to update software and operating systems regularly
- Unsecured Networks: Connecting to public Wi-Fi without proper protection
- Lack of Employee Training: Insufficient cybersecurity awareness among staff
- Weak Password Policies: Using simple, reusable passwords across multiple platforms
Wits University emphasizes that many security breaches stem from inadequate security configurations on personal devices and insufficient employee training. These oversights can transform seemingly innocuous mobile devices into significant entry points for cybercriminals.
To help prevent these critical security mistakes, explore our guide on how not to get hacked.
 Remember, in the world of mobile security, prevention is always more cost-effective than recovery.
Remember, in the world of mobile security, prevention is always more cost-effective than recovery.
Protect Your Business with Expert Mobile Device Security Solutions
The risks highlighted in the Complete Guide to Mobile Device Security make it clear many South African businesses face serious challenges from malware infections, phishing attacks, and weak BYOD policies. Without strong mobile device management, multi-factor authentication, and employee training, sensitive company data can become vulnerable. If you are feeling overwhelmed by the complexity of safeguarding mobile devices while meeting compliance demands, you are not alone.
At Techtron, we understand these pain points and provide tailored IT management services that focus on proactive mobile security, seamless integration with cloud platforms like Microsoft 365 and Azure, and continuous monitoring to detect threats early. Don’t wait for a costly breach to act. Discover how our cybersecurity services and proven mobile security strategies can protect your organisation’s digital assets and keep your team productive.
Ready to safeguard your mobile environment and reduce risk now Visit Techtron for expert IT management and security support specifically designed for professional firms with growing digital needs. Take control of your mobile security today and secure your future.
Frequently Asked Questions
What is mobile device security?
Mobile device security is a comprehensive approach to protecting organizational data, networks, and digital assets on devices like smartphones and tablets. It involves implementing measures such as device management, data protection, and access controls.
Why is mobile device security important for businesses?
Mobile device security is crucial for businesses to mitigate the increased cybersecurity risks associated with the use of personal devices for work (BYOD). Without proper security measures, organizations can face data breaches and financial losses.
What are some common threats to mobile devices?
Common threats to mobile devices include malware infections, phishing attacks, network vulnerabilities, social engineering attacks, and unpatched software, all of which can expose sensitive organizational information to cybercriminals.
How can organizations improve mobile device security?
Organizations can improve mobile device security by implementing best practices like developing comprehensive usage policies, conducting regular training sessions for employees, utilizing multi-factor authentication, and continuously monitoring for security anomalies.